CrowdStrike
Workflow for Building Agentless Microsegmentation
Onboarding
This section describes the steps required to onboard CrowdStrike integration to the Xshield platform.
Prerequisites
The following subscriptions need to be active in the CrowdStrike platform:
-
Falcon Data Replicator(FDR) - For ingesting network flow records from CrowdStrike platform. Xshield requires a configured FDR information (that allows data to be exported) to be generated on the CrowdStrike platform.
-
Falcon Firewall Management - For pushing FireWall policies to the CrowdStrike Agents
You can check the status of the enabled subscriptions/modules by navigating to Support and resources > General settings > CID details in the CrowdStrike console.
The following CrowdStrike credentials are required to activate the integration:
- API Credentials - To make programmatic API calls to CrowdStrike platform
- FDR Credentials - To capture the network events from CrowdStrike platform
API Credentials
The procedure for generating API credentials on the CrowdStrike platform is available at Generating API Credentials on CrowdStrike UI
API credentials are used to make programmatic API calls to CrowdStrike platform. The following operations are performed using the API credentials:
- Fetch host groups and hosts information from CrowdStrike platform
- Creation of host groups and assign hosts to host groups
- Manage firewall policies, rule groups and rules
- Fetch firewall events from CrowdStrike platform
These credentials must have sufficient permissions. These permissions are termed as Scopes in CrowdStrike platform. Each Scope can be provided with Read only or Write permissions. Below table describes the Scopes that must be enabled on the provided API credentials.
| Scope | Read/Write | Comments |
|---|---|---|
| Host groups | Read & Write | To read information about the host groups and to create required host groups for Firewall Enforcement. If we are only targeting visibility, write permission is not required. |
| Hosts | Read | To read information about the hosts. |
| Firewall Management | Read & Write | To create Firewall policies, Rule Groups, Rules, assign Host groups to policies etc. If we are only targeting visibility, this permission is not required. |
Refer to https://falcon.us-2.crowdstrike.com/documentation/page/a2a7fc0e/crowdstrike-oauth2-based-apis for details about how to generate API credentials.
FDR Credentials
The procedure for generating FDR credentials on the CrowdStrike platform is available at Generating FDR Credentials on CrowdStrike UI
FDR credentials also called CrowdStrike Data Replicator feed credentials are required to capture the network events from CrowdStrike platform.
A separate feed must be created for each Xshield-Crowdstrike integration and feed must have following Primary events enabled:
| Event Name | Platforms | Comments |
|---|---|---|
| NetworkListenIP4 | Windows, Linux, macOS | To capture IPv4 listen events |
| NetworkConnectIP4 | Windows, Linux, macOS | To capture IPv4 connect events |
| NetworkReceiveAcceptIP4 | Windows, Linux, macOS | To capture IPv4 accept events |
A total of 9 primary events must be enabled. A total of 3 kinds of events for each of the Windows, Linux, and macOS platforms. The created FDR credentials must not be shared for any purpose other than Xshield integration and every Xshield integration must have separate set of FDR credentials.
IMPORTANT NOTE: There can only be a maximum of 4 active FDR feeds on a given CrowdStrike tenant. Make sure the created FDR feed is active.
Refer to https://falcon.us-2.crowdstrike.com/documentation/page/fa572b1c/falcon-data-replicator for details about how to generate FDR credentials.
Activate Integration
In Xshield console, navigate to Settings > Integrations > EDR > CrowdStrike. Click on Activate button. Provide the API credentials and FDR credentials. Click on Test button to validate the credentials. Once the test is successful, click on Save button to activate the integration.
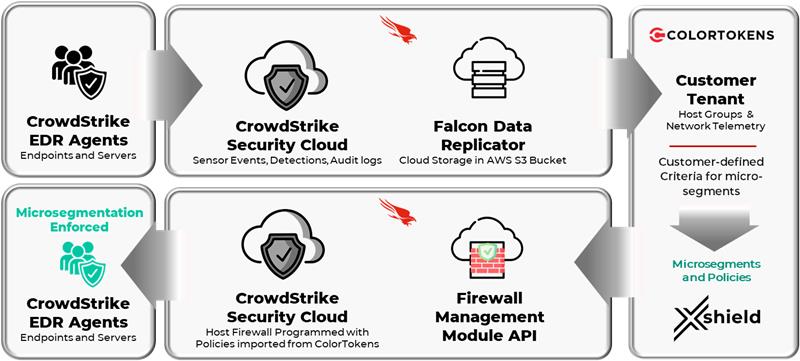
Once the integration is activated, Xshield platform will automatically fetch all the host groups present in the CrowdStrike platform. It can take up to 5 minutes for the host groups to be fetched. A new menu item Host Groups will appear in the left navigation bar. Clicking on this menu item will display the list of host groups fetched from the CrowdStrike platform.
Host Discovery
The CrowdStrike platform installs agents on endpoints to discover them. Operators can group discovered hosts into Host Groups based on tags such as Hostname, Grouping Tags, OS Version, Platform etc. These Host Groups and Hosts are first-class abstractions in the CrowdStrike platform.
Customers may have a large number of hosts managed by the CrowdStrike platform. They may decide to implement micro segmentation on all or only a certain set of those hosts using the Xshield solution. To facilitate this, the integration provides a facility to limit the hosts to be managed by the Xshield platform. Customers can activate a selected set of host groups and the Xshield platform will onboard/import hosts from these activated host groups.
Activate/Deactivate Host Groups
From Host Groups page in Xshield console, select one or more host groups and select Active/Inactive option under Change Status. This will open a fly panel. Review the selected host groups and click on Confirm button to activate/deactivate the selected host groups.
In case of activation, Xshield platform will start fetching hosts from the activated host groups. It can take up to 10 minutes for the hosts to be fetched and added to Xshield platform.
In case of deactivation, Xshield platform will remove the hosts from the deactivated host groups. It can take up to 10 minutes for the hosts to be removed from Xshield platform. If the hosts that are part of the deactivated host group are also part of another active host group, such hosts are not removed from Xshield platform.
Xshield platform will sync hosts from the active host groups at regular intervals (every 24 hours) or sync can be manually triggered. Xshield retrieves hardware, operating system telemetry data, and other tags for hosts (using the CrowdStrike API) within selected host groups. This data is populated as assets in Xshield and used to define segmentation groups.
View and Explore Assets
From Assets page in Xshield console, you can view and explore the hosts imported from CrowdStrike platform. Click on any asset name to view the details. The asset details page will display information like IP Address, Operating System, Tags, etc.
Network Visibility
CrowdStrike provides network events through a facility called Falcon Data Replicator (FDR). As soon as the integration is added, Xshield platform starts gathering the network events using FDR and starts ingesting these events to the Xshield platform. Only network events pertaining to imported hosts are ingested and remaining unwanted events are discarded.
These events are mapped to ports&paths in Xshield and are associated with appropriate assets. This data allows network communications visibility through the Xshield visualizer.
Considerations:
- CrowdStrike Falcon agent pushes the network events data almost immediately on collection to the CrowdStrike platform but will throttle if the CPU is busy. CrowdStrike platform buffers the events across all hosts and uploads them to the S3 bucket once every five(5) minutes. The Xshield platform reads data from the S3 bucket once every five(5) minutes. The Xshield Traffic Ingestion service will take another two(2) minutes to consume this data. This roughly takes under fifteen(15) minutes for data collected by the CrowdStrike agent to show up on the Xshield platform.
- CrowdStrike Falcon agents limits the number of similar network events they send to CrowdStrike platform. Agents only send one unique network event per one hour on Linux, and on Windows/macOS, they send one unique network event per every 24 hours. Unique event is defined as process ID, source IP, destination IP, destination port, and protocol for outbound connections and process ID, source IP, destination IP, destination port, and protocol for inbound connections.
CrowdStrike Falcon agents captures only the network events Connect, Accept, and Receive. They do not capture packet events. Hence, it is not possible to derive the volume of data transmitted over these connections. Because of this, Data Bytes in the Paths is always specified as zero(0)
Segment and Template Definition
New CrowdStrike segments (based on tags) can be created on the Xshield for assets imported from CrowdStrike. This follows the standard segment creation process in Xshield.
Click on Segments menu item in the left navigation bar. Select CrowdStrike tab and click on Create Segment button. Provide the segment name and description. Click on Save button to save the segment
Templates and named networks can be added to the segment during segment creation time or can be added later. To add templates and named networks after the segment is created, click on More Options button of the segment in the CrowdStrike segments page and select Manage Templates or Manage Named Networks. Add appropriate templates and named networks and click Assign button to save the changes.
Templates allow specifying FQDN for outbound rules. CrowdStrike agents resolves FQDN into IP addresses before programming the firewall rule. It also updates firewall rules when a new IP address is discovered for the FQDN.
Considerations:
BELOW ARE SOME OF THE CRITICAL ASPECTS THAT MUST BE FOLLOWED FOR THE SOLUTION TO WORK SEAMLESSLY.
- We do not support mixed mode of operation of firewall policies. This means, customer must not have any pre-existing firewall policies in CrowdStrike platform. All the firewall policies are created & managed by Xshield integration.
- As part of CrowdStrike segment creation, Xshield creates a custom core tag with name "CrowdStrike Firewall Host Group" in Xshield platform and the integration tags imported CrowdStrike assets with appropriate values for this tag.
- Make sure that there is a free slot for this custom core tag as the integration attempts to create this tag during CrowdStrike segment creation. As of now, Xshield platform allows up to 4 custom core tags.
- Make sure that this tag is not deleted manually by the customer as this is required for functioning of firewall implementation.
- For this tag, do not manually modify an asset's tag value or add new tag values.
CrowdStrike Platform Firewall Implementation
CrowdStrike platform does not allow firewall programming of individual assets and it happens at Host Groups level.
Following entities in CrowdStrike platform facilitates firewall enforcement:
- Firewall Policies
- Firewall Rule Groups
- Firewall Rules
Firewall policy contains one or more rule groups. And each rule group contains one or more rules. And Firewall policy and rule groups are platform specific. Hence, every platform should have separate Firewall policies. Each firewall policy has a precedence assigned to it.
We can assign one or more hosts groups to a firewall policy in CrowdStrike. And a given CrowdStrike asset can belong to more than one host groups (either by static assignment or by means of dynamic tags).
A critical restriction in CrowdStrike is that a given CrowdStrike asset can only get/capture firewall rules from one and only one firewall policy. If a host belongs to multiple host groups and if each of those host groups is assigned to different firewall policies, then the target firewall policy for that host is decided based on the precedence of the firewall policies. Firewall policy with the highest precedence is selected and applied on that CrowdStrike asset.
Refer to CrowdStrike documentation https://falcon.us-2.crowdstrike.com/documentation/page/a6e15696/falcon-firewall-management for details about how Firewall Management.
Xshield Firewall Implementation
ColorTokens has different firewall policy implementation semantics and differs from how CrowdStrike implements it.
- ColorTokens segmentation model is hierarchical in the sense that we can create higher level segments, mid level segments and finally leaf segments.
- These leaf segments are the true micro segmentation boundaries.
- All the segments above leaf level are used to assign common templates/named networks that are common leaf segments.
- We can configure policy automation configurations either at segment level or at individual asset level.
Because of the way CrowdStrike implements firewall enforcement, you must follow below segmentation model for CrowdStrike enforcement:
- CrowdStrike platform does not provide support for hierarchical microsegmentation.
- All the segments created must be leaf segments.
- All the common templates must be assigned to each leaf segments along with micro segment specific templates. Same thing is applicable for named networks.
- Policy automation configurations cannot be applied at asset level and can only be applied at the segment level.
To facilitate the same, concept of precedence is introduced for the segments created in Xshield platform. With this, if a given asset matches with criteria of multiple segments, the asset is made part of the segment with highest precedence.
As a part of this integration, Xshield platform will create a pseudo asset named as EDR_GROUP_<segment> for every CrowdStrike Segment created by the user. This is necessary because in CrowdStrike platform, policy enforcement is only at the HostGroup level; this means that any changes to the segment policy must be enforced at that Host Group. The Xshield platform uses the Push To Firewall (PTF) mechanism to let users (or automatically) to actually apply the policy at an asset level (and not at a segment level). Hence, a pseudo asset is created for CrowdStrike to allow the user to continue to mimic the same function for CrowdStrike integration.
Assets that become part of a segment automatically inherit zero trust settings, templates, and named networks from the segment. And these settings cannot be applied at asset level because of restrictions mentioned above. Customers can use the created CrowdStrike segments to program automation settings, assign templates, named networks and other configurations just like native Xshield segments.
As part of CrowdStrike segment creation, a host group will be created in the CrowdStrike platform and all the assets that are members of the corresponding segment in the Xshield platform will be made members of this host group. The integration will continuously monitor for segment-asset membership changes and corresponding membership changes will be done for CrowdStrike host group. These changes may take up to 30 minutes to reflect in CrowdStrike platform.
Segment Enforcement
When CrowdStrike segment is enforced, following entries are created in the CrowdStrike platform:
- Firewall Policies
- Rule Groups
- Rules
Two firewall policies will be created (one for each of Windows and MacOS). Two rule groups will be created for each of the firewall policies. One for inbound rules and one for outbound rules.
The integration will continuously monitor segments for any configuration changes and will program the firewall policies on the CrowdStrike platform accordingly. It can take up to 15 minutes for the changes to reflect in CrowdStrike platform.
Access policy is supported on CrowdStrike segment by manually creating two different segments and using them as a source or destination in the Inbound or Outbound paths in a template and assigning the template to respective segments.
The addition or deletion of an asset to/from the segment used for access policy will lead to firewall hostgroup membership changes:
- user has to wait up to 30 minutes for the firewall hostgroup membership update.
- user can perform manual firewall hostgroup membership Sync operation to make the change effective immediately.
Firewall Events
CrowdStrike platform makes firewall events available for the firewall rules configured with allow with log and deny with log actions. These events are collected by the integration via API and ingested to Xshield platform. This process works similar to how native Xshield agents collect and publish firewall events to the platform.
The deny events show up under Monitor > Logs with Log Category as Policy and Log Name as Blocked communication attempt.
Limitations:
CrowdStrike platform does not provide firewall events when traffic matches a rule with a wildcard port and protocol.
- This prevents detection of network communications without a matching policy template (simulate mode restriction).
- Traffic dropped by the default deny policy is not reported by the Falcon platform, limiting Xshield’s ability to display discarded network communications.
Limitations
There are certain limitations on the micro-segmentation implementation when compared to the agent based micro-segmentation. These are either due to restrictions or limited capabilities on the CrowdStrike platform and some similar limitations on the Xshield security platform.
The following features are unsupported due to restricted functionality on the Xshield Security Platform:
- Breach Response Templates for CrowdStrike Segments
- Process based Policy Templates
- No support for Progressive Active/Open Ports
The following features are unsupported due to limitations in functionality on the CrowdStrike Platform:
- Hierarchical microsegmentation
- FQDN based Policy Templates (No association of FQDN to Paths in Network Telemetry)
Linux
CrowdStrike platform does not support host firewall programming on Linux hosts, preventing Xshield from enforcing micro-segmentation policies on such hosts.
Segmentation
Refer to Segment and Template Definition section for details.
User Segmentation
User Segmentation policies cannot be applied on Crowdstrike installed assets.
User Segmentation works by identifying the user who has logged onto the desktop or laptop so that the policies that applies to group membership can be enforced on the desktop or laptop.
CrowdStrike platform does not provide a mechanism to notify this event and hence the Xshield platform cannot bind the user's policy to the asset where a CrowdStrike agent is installed.
Recommendation: Install the Xshield agent on Linux hosts for micro-segmentation policy enforcement.
Network Telemetry
Refer to the Network Visibility section for details.
Firewall Logs
Refer to the Firewall Events section for details.
Sync Timings
| Operation | Trigger | Time to Update |
|---|---|---|
| Import Host Groups | Integration activation Manual sync Scheduled Sync(every 24 hours) | Up to 10 minutes |
| Import Hosts | Host Group activation/deactivation Manual Sync Scheduled Sync(every 24 hours) | Up to 10 minutes |
| Import Firewall Logs | Continuous | Up to 10 minutes |
| Import Network Telemetry | Continuous | Up to 30 minutes |
| Export Firewall Host Group Members | CrowdStrike Segment membership changes Manual Sync Scheduled Sync(every 30 minutes) | Up to 10 minutes |
| Export Firewall Policy | Any Segment Policy update Manual Sync | Up to 10 minutes |