Assets
In today’s digital landscape, most organizations operate in Hybrid Cloud environments, where application infrastructures are distributed across on-premises data centers and Hyperscale Cloud Providers. These applications may be built using either Monolithic or Microservices architectures and are deployed on a variety of platforms including physical servers, virtual machines, Docker containers, or cloud-native services.
To implement effective Zero-Trust Microsegmentation, it is critical to first discover and secure all application workloads and user endpoints—regardless of where or how they are deployed.
What Are Assets? In this context, assets refer to all the critical components of your IT and OT environments, including:
- Servers (physical or virtual)
- Containers
- User endpoints (laptops, desktops)
- Operational Technology (OT) devices (such as industrial control systems, PLCs, and SCADA devices) These assets form the foundation of your digital infrastructure and are often the primary targets for cyber threats.
Asset Discovery
Xshield provides a robust and unified platform for comprehensive asset discovery and security enforcement across your digital infrastructure. It enables enterprises to gain full visibility into their servers, containers, user endpoints, and operational technology (OT) assets through flexible deployment options:
- Xshield Agent-Based Discovery a. Lightweight Xshield agents are installed directly on assets (Servers & Endpoints) b. Leverage ISTIO Service mesh for Containers
- Agentless Integration Seamless integration with third-party platforms:
- CrowdStrike: Leverages existing endpoint telemetry for asset discovery and monitoring. (Integration with more EDR platforms are on the way!)
- Gatekeeper Enables visibility and control without deploying additional software for devices such as OT, legacy systems and other workloads where agent deployment is not possible.
Once deployed, the Xshield platform performs the following key functions:
-
Asset Telemetry Collection Continuously gathers detailed telemetry data from each asset
-
Policy Enforcement Applies security policies defined in the Xshield Management Portal directly to the assets, ensuring consistent protection across the environment.
-
Threat Prevention & Traffic Control Actively blocks unauthorized or suspicious traffic in real time, reducing the attack surface and preventing lateral movement.
-
Violation Reporting & Visibility All policy violations and blocked activities are logged and reported back to the central portal, providing actionable insights via reports and audit trails for security teams.
Asset Types
- Server Assets
- User Assets
- Devices
- Containers
Asset Search, Visualization, and Detailed View
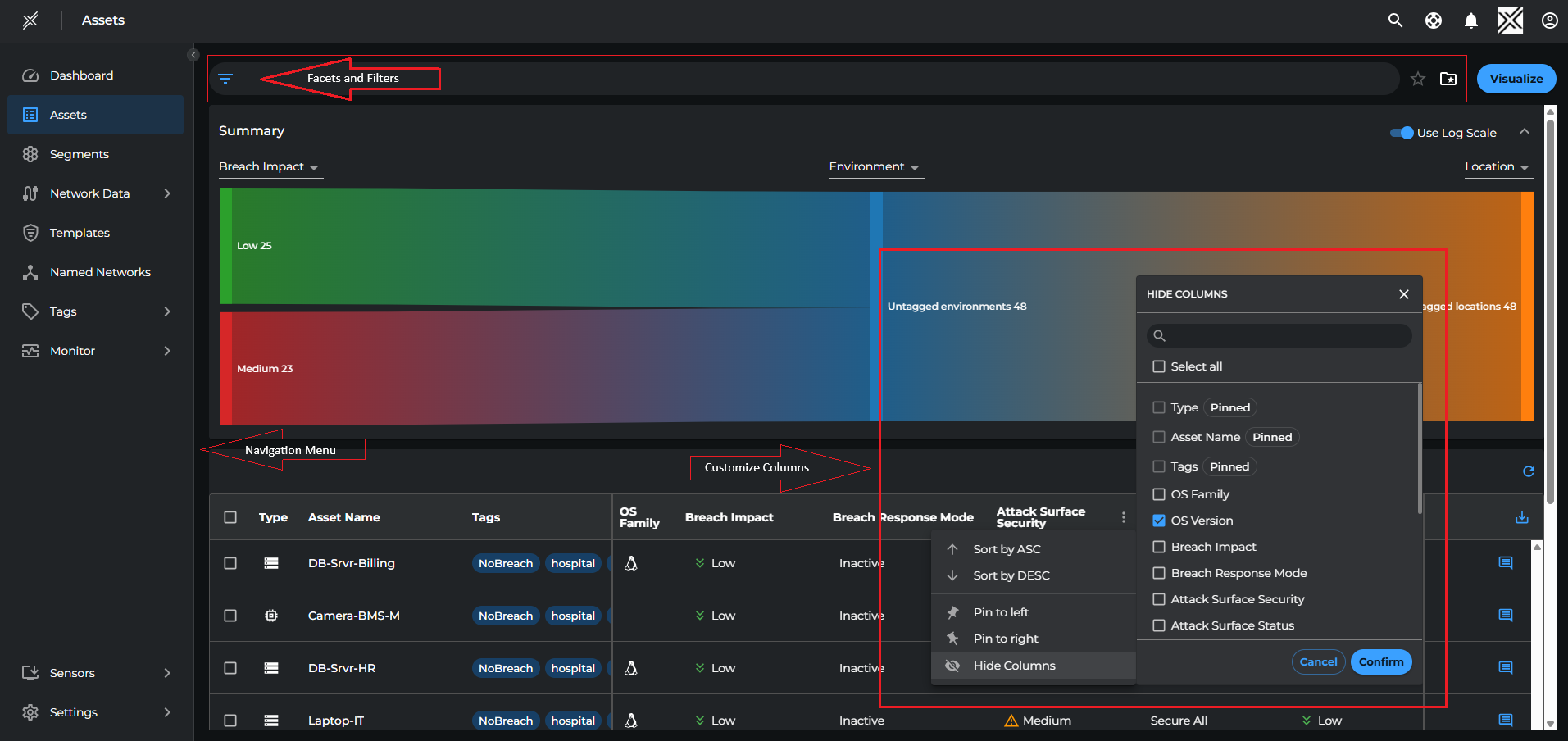
Clicking on the Asset tab in the left-hand Navigation menu will list all the discovered assets in your tenancy.
The Search box at the top-right corner allows you to search for assets by their hostname or tags. Advanced context-based searching can be done using filter options. If you want to search for assets that match multiple criteria, you can use Facets and Filters. Facets are unique dimensions in Xshield, such as Tags, Templates, and Agents. Each Facet consists of multiple filter groups and filters. For example, the "Security" facet includes filter groups such as Attack Surface, Blast Radius, Asset Inbound Status, and Asset Outbound Status.
To filter assets:
- Click the Funnel icon in the filtering bar at the top of the Assets page.
- View all available facets and filters.
- Select a Facet, choose the Filter Group, and apply the desired Filter(s).
- Choose one or more values for the selected filter(s).
The filtering bar will display the applied criteria, and the Assets page will show only the filtered list of assets.
Sankey Chart for Asset Search
Another way to search for specific assets is by using the Sankey Chart. A Sankey Chart visualizes the flow from one set of values to another. In Xshield, the Sankey Chart represents tags as nodes and the relationships between the tags as links.
Viewing Asset Details
To view an asset's telemetry data and other details, navigate to Assets in the left navigation menu to see all servers, endpoints, and microservices containers. The asset page provides a quick view of assets with their basic information such as the Operating system, breach impact status, tags etc that are displayed in the columns. Columns can be customised by adding, hiding or pinning using the ellipsis icon.
Example of the Asset page:
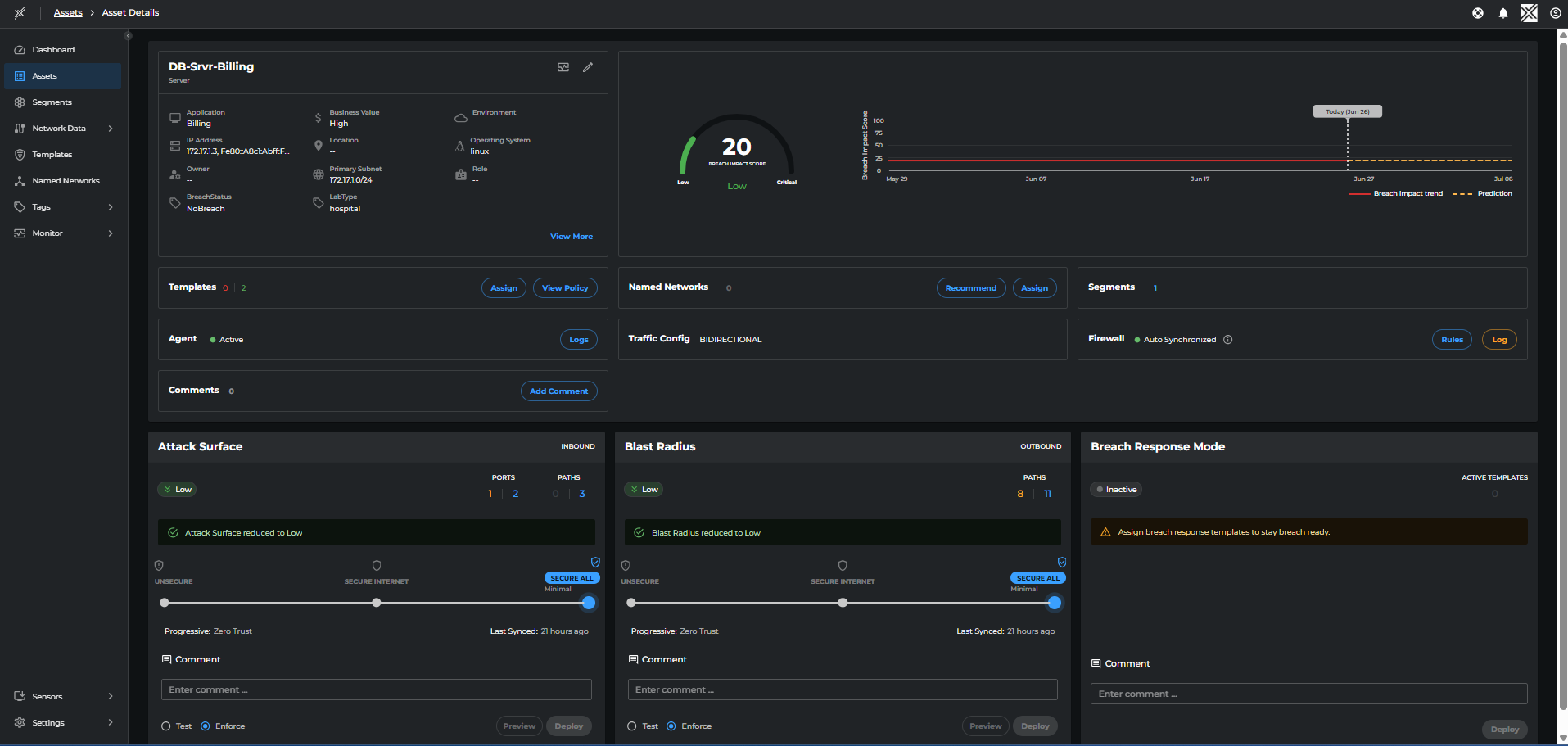
Clicking on an asset will open the Asset Details page that displays more information and configurable options:
- Asset Properties - IP Address, OS, Cloud tags
- Configuration Data - Breach impact score and trend
- Templates, Named Networks, Firewall Status
- Agent Logs and Firewall Logs
- Security Enforcement Details - Attack Surface, Blast radius, Breach Response
Example of the Asset Details page: