Dashboard
By aggregating data from all the assets across the enterprise, the Xshield Dashboard delivers a real-time, enterprise-level snapshot of breach readiness—empowering operators to monitor and act on the Enterprise's overall security posture in an effective manner.
Main Dashboard Sections
- Metrics Board
- Title Bar
- Filter/Query Bar
- Navigation Bar
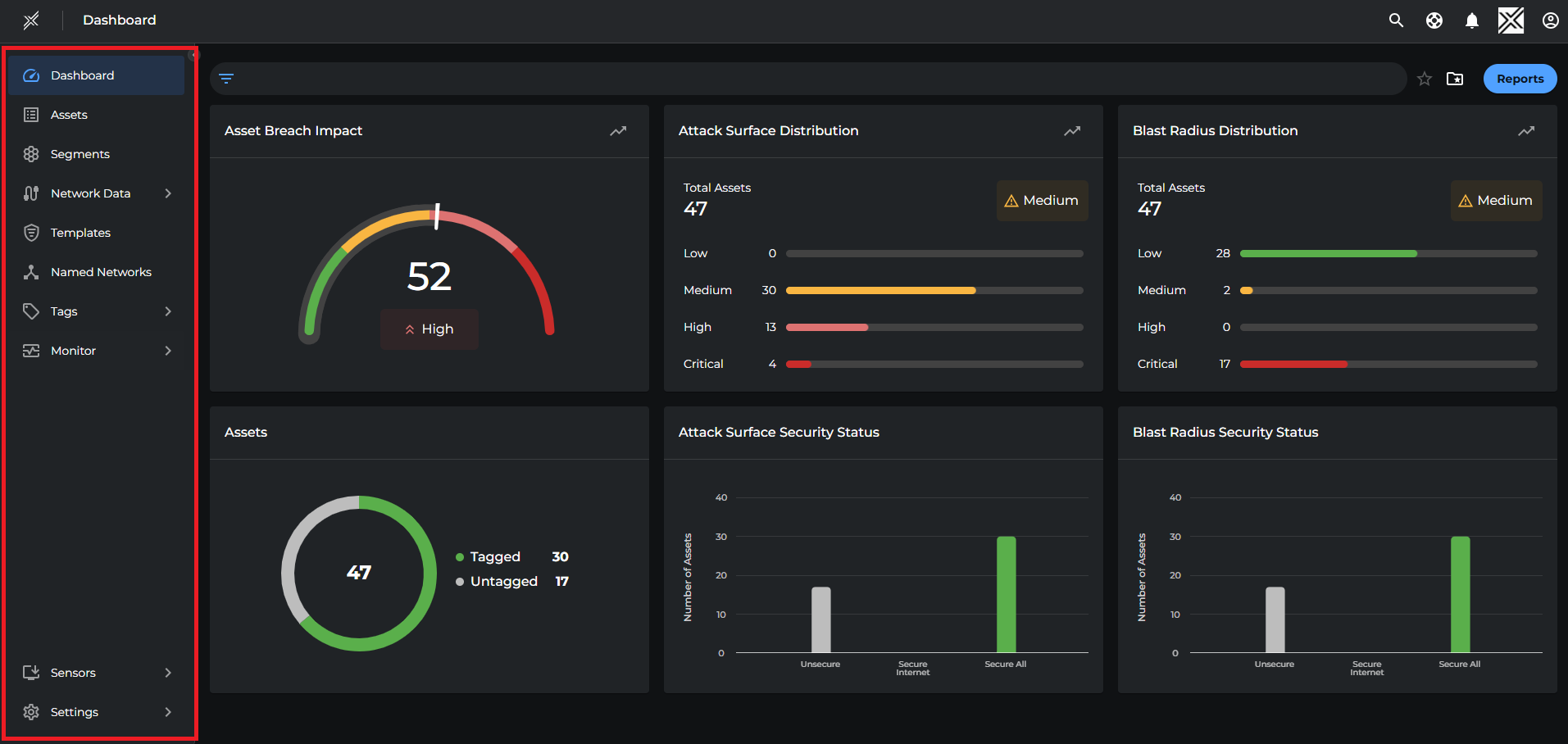
Metrics Board
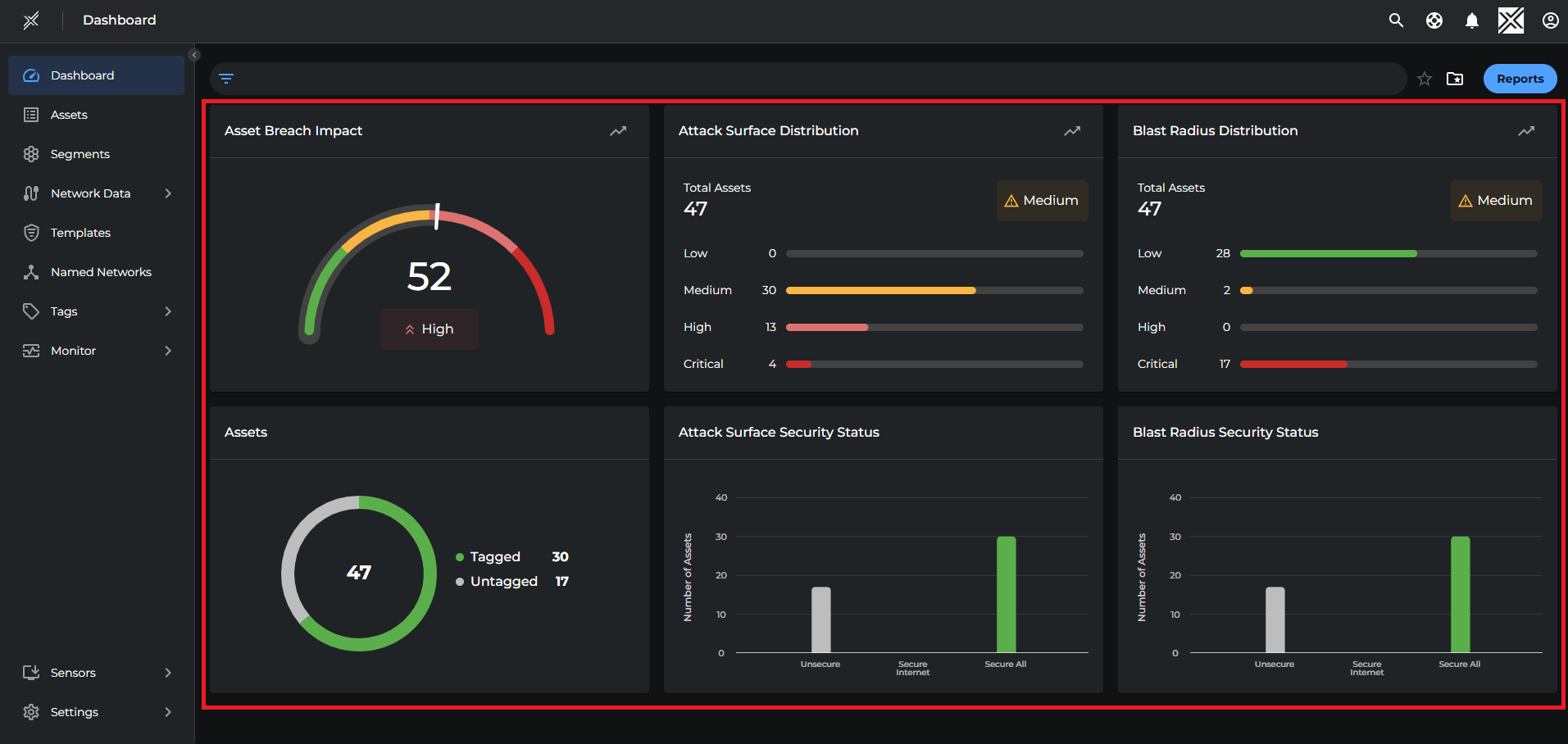
This main area presents an overview of the environment’s security posture through interactive tiles:
- Asset Breach Impact: Shows the average breach impact score across all assets in the platform. Helps to prioritize remediation by identifying how severely a breach could affect the organization. The trend icon provides historical context and future posture prediction
- Attack Surface Distribution: Distribution of assets across Low, Medium, High, and Critical security states. Aids in understanding overall risk posture and targeting high-risk areas first and the historical trends help track improvements or deteriorations over time.
- Blast Radius Distribution: Displays how widespread the impact would be if an asset is breached. Highlights critical assets that can affect large portions of the environment, the predictive insights help in proactively reducing potential blast radius.
- Assets: Shows total assets and how many are tagged and untagged, helps in ensuring complete asset inventory and encourages proper classification for policy enforcement.
- Attack Surface Security Status: Bar graph showing the number of assets that are Unsecure, Secure to Internet, or Fully Secure which provides a quick visual of segmentation effectiveness and exposure to external threats.
- Blast Radius Security Status: Bar graph showing how many assets are unsecure or protected against lateral movement, helping evaluation of internal segmentation strength and limit breach spread within the network.
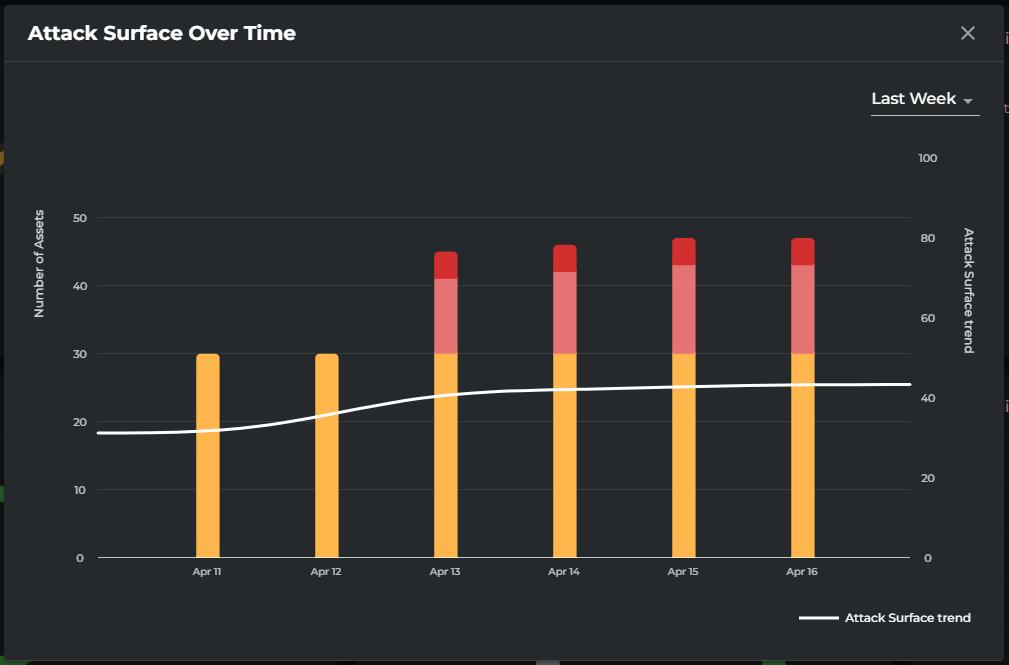
Tip: Metrics are interactive. Clicking on a graph redirects to relevant detailed pages. Trend icons open a popover with historical & future prediction of the security posture. The operator may use filters to review metrics specific to the requirement
Title Bar
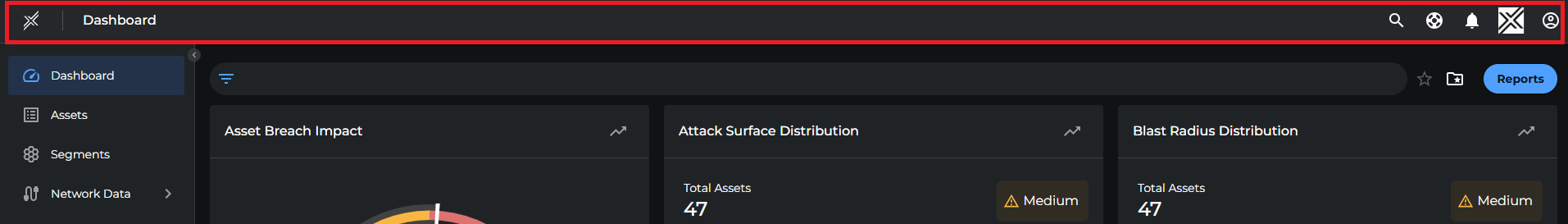
Persistent across all pages in the Xshield tenant, it includes:
- Xshield Logo: Redirects to the dashboard
- Current Page Indicator
- Search Icon
- Help Icon: Opens knowledgebase and release notes
- Alerts: Redirects to the Alerts page; shows notification bubble if alerts are configured
- Tenant Name or Logo
- Profile: Switch orgs, access demo, view tasks, change themes/language, log out
Filter/Query Bar
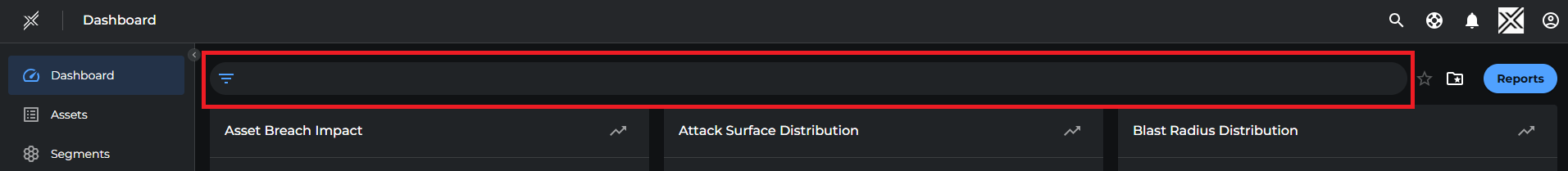
Allows users to narrow down data and views by applying filters such as tags and metadata attributes. Each filter category is collapsible and allows for targeted searching.
Navigation Bar
Consists of the administration pages and facilitates navigation across the Xshield tenant:
- Dashboard: Centralized view of security metrics and alerts
- Assets: Displays all onboarded assets with key details and summary in a graph
- Segments: Centralized workspace to create segments and manage the security policies of the segments. Segment Reports can be generated and downloaded from the segments page
- Network Data: Divided into two sections
- Ports: Provides a detailed view of all network ports and services across assets.
- Paths: Shows real-time data flows between source and destination assets/networks
- Templates: Create and manage reusable policy templates
- Named Networks: Define and manage a logical group of network IPs
- Tags:
- Tag Rules: Manage automated tagging logic
- Tag Names: View and create custom/pre-configured tags
- Monitor: Real-time visibility into alerts, logs, and system tasks
- Sensors:
- Agents: Download agent software, review and manage installed agents
- Gatekeepers: Secure IT/OT systems with Gatekeeper appliances
- Containers: Download container agent and manage container agents
- Settings:
- General: Manage platform settings like theme, language, and agent security
- User Management: Add and manage user accounts
- Integrations: Set up third-party integrations
- Alert Rules: Configure alert rules
- API Keys: Access documentation and create keys for API usage