Ports and Paths
Overview
The Xshield Platform is designed to provide deep visibility into enterprise network communications, enabling security administrators to implement robust micro-segmentation policies. These policies are essential for enforcing Zero Trust principles and minimizing the attack surface by preventing unauthorized lateral movement within the network.
Xshield achieves this through two core abstractions:
Ports – Representing service endpoints on assets. Paths – Representing communication flows between entities. These constructs allow administrators to visualize, analyze, and control network behavior with precision.
Ports: Network Service Endpoints
A port is an observable, real-world network service endpoint that identifies a specific process or a service on the device, listening for incoming traffic. Ports are managed by the operating system's TCP/IP stack and are essential for enabling inter-process and inter-device communication.
Port Classifications in Xshield
Active & Open Ports
- These are ports currently engaged in network communication.
- Xshield continuously monitors traffic to determine which ports are actively being used.
- Active ports are critical for identifying legitimate services and understanding communication patterns.
Inactive Ports
- These are open (listening) ports that are not currently involved in any communication.
- Inactive ports may indicate unnecessary or potentially malicious services.
- Xshield flags these ports for review, allowing administrators to proactively block them via micro-segmentation policies.
Malicious Ports
- These are ports known to be associated with malware, backdoors, or unauthorized services. Xshield provides pre-defined policy templates to block Malicious and vulnerable ports that can be applied immediately upon agent deployment.
Security Implications
Unauthorized Access: Open ports can be exploited by attackers to gain unauthorized access or exfiltrate data. Policy Enforcement: Xshield enables administrators to define granular policies that:
- Block unused or suspicious ports.
- Restrict access to critical ports based on source identity, network zone, or device role.
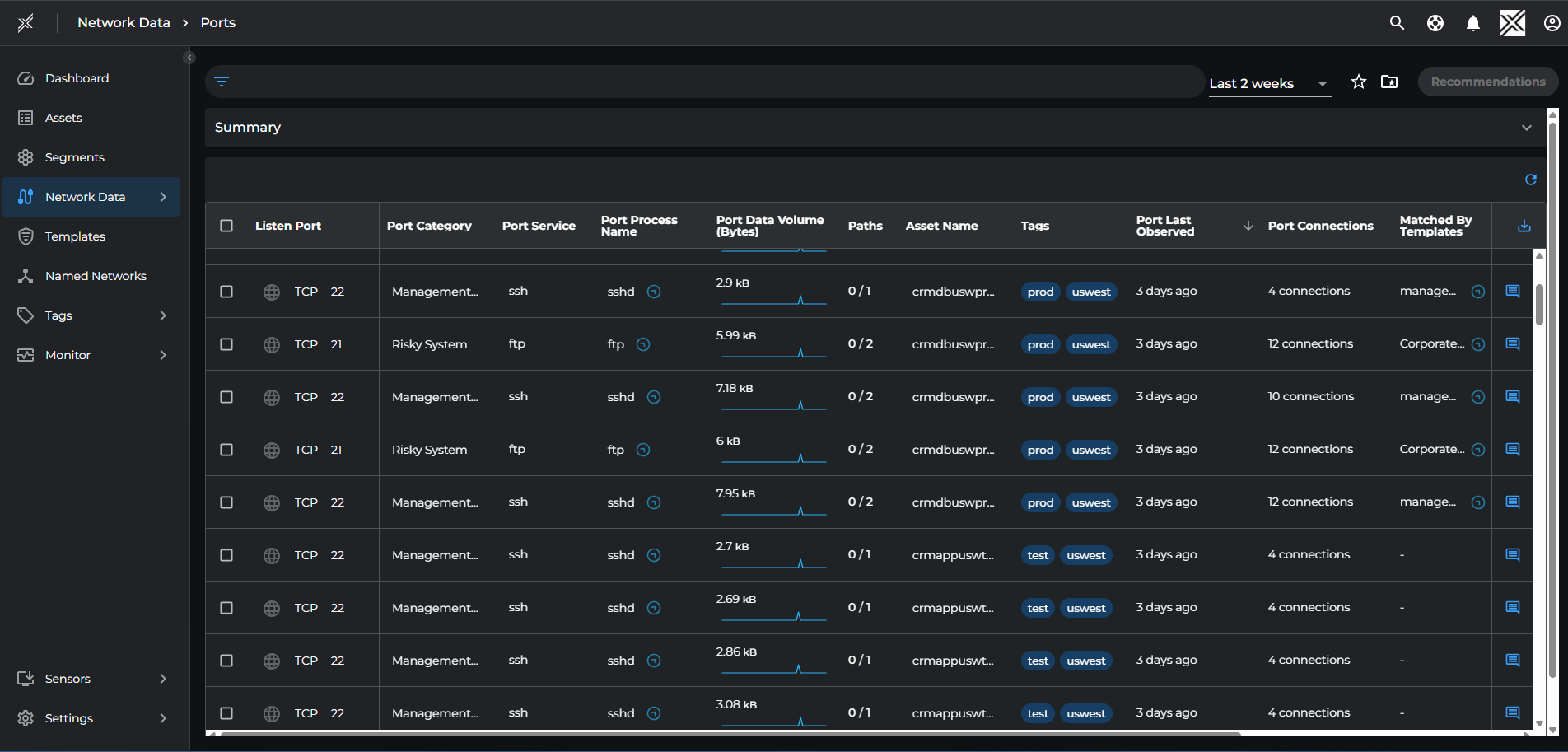
The Ports Page provides a dynamic view of all ports currently in use by assets in the network and tracks the following metrics:
- Listening Port
- Port Category
- Port Service
- Port Process name
- Port data Volume (in Bytes)
- Paths (Number of paths)
- Asset Name
- Tags
- Port Last Observed (Timestamp)
- Port Connections (Number of connections)
- Matched by Template (Id any Template matches the port)
- Port Status
- Port Candidate Status
- MITRE Attack Techniques (Shows the Technique ID with url and Technique Name)
The metrics can either be hidden or shown based on the user's preference.
A screenshot of the ports page:
Paths: Communication Flow Abstraction
A Path represents a logical communication flow between a source and a destination over a specific port. If the Source and destination communicate multiple times (on the same port), they will all be registered as a single path
A path can also be extended to support multiple source and/or destination IP addresses. If the IP addresses are part of a grouping (Named Networks) then all communications to/from the addresses in that group to/from the application are considered as the same path.
A device connecting to a set of domain controllers can be better abstracted in a single path rather than a path to each domain controller as the micro-segmentation policy to be applied will be the same.
This abstraction simplifies the complexity of network traffic by grouping related flows into a single, manageable entity.
Benefits of Path Abstraction
Scalability: Reduces the need to analyze thousands of individual connections. Policy Simplification: Enables administrators to define policies for groups of communications rather than individual flows. Visibility: Provides a clear view of which services are being accessed, by whom, and how frequently.
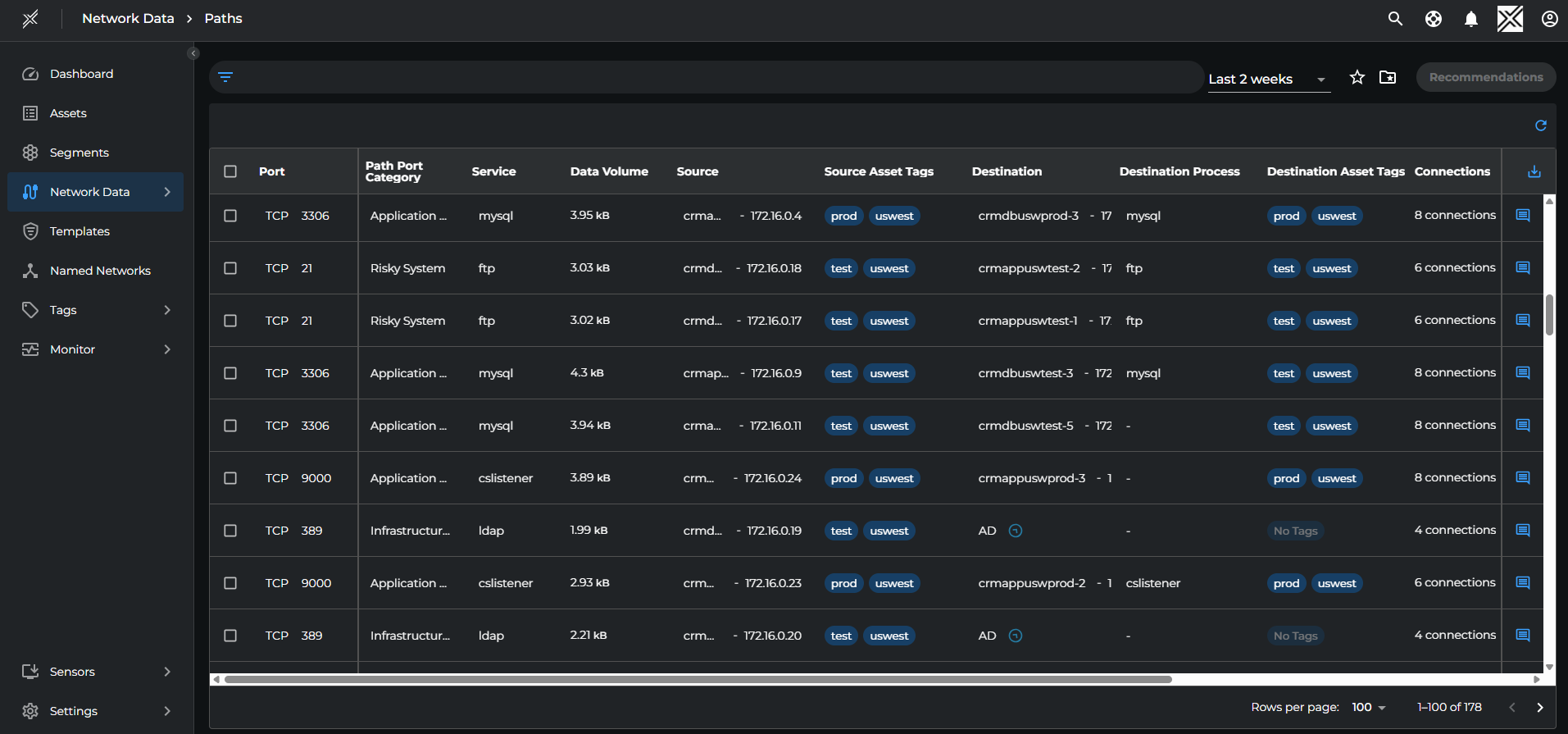
Each path tracks multiple metrics and reports them in the Paths page. The metrics include:
- Port
- Path Port Category (Application, infrastructure, Risky etc)
- Service
- Data volume
- Source and destination IP addresses
- Source and Destination Asset Tags
- Number of connections
- Matched By Templates
- Destination Process
- Path Last Observed (Timestamp)
- Path Status (Reviewed or Unreviewed)
- Path Candidate Status (Allowed or Denied)
The metrics can either be hidden or shown based on the user's preference.
A screenshot of the paths page:
Conclusion
The Xshield Platform’s Ports and Paths abstractions provide a powerful foundation for implementing Zero Trust security by offering deep visibility and actionable insights. Xshield enables enterprises to build a resilient, breach-ready network architecture through intelligent micro-segmentation.