Containers
Overview
Kubernetes has become the de facto standard for container orchestration, enabling enterprises to deploy and scale containerized applications at speed. However, its complex architecture and dynamic environments introduce a unique set of security challenges.
ColorTokens Approach to Container Security
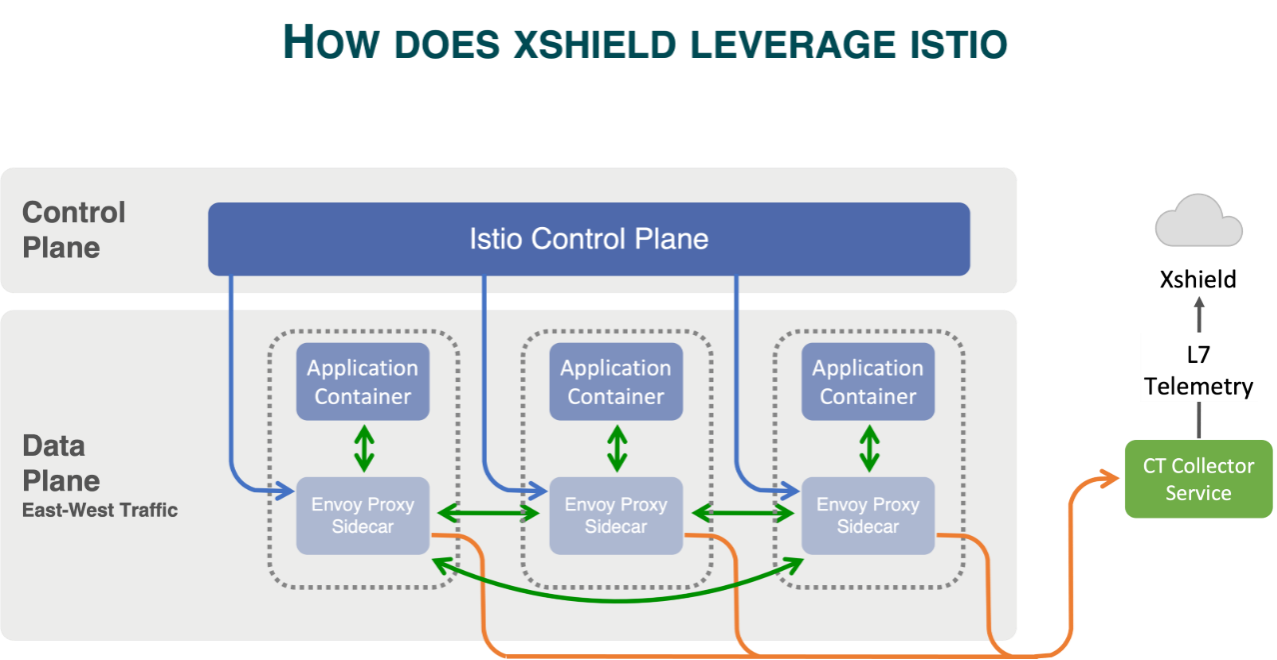
ColorTokens Xshield offers agentless security for microservices by integrating with service meshes like Istio.
It addresses the limits of network-level security as microservices scale and predominantly use HTTP/HTTPS for communication.
Using Istio’s Envoy proxy, Xshield enables API-layer micro-segmentation.
This ensures zero-trust security with deep visibility and precise control over microservices' traffic.
Complete Agentless Deployment
Xshield provides agentless container security, removing the need to deploy agents across Kubernetes environments.
It integrates with Istio and supports both managed and unmanaged Kubernetes deployments.
Visualization
Xshield visualizes microservices, their communication, and context across clusters to define logical business segments.
It helps security teams assess breach risk, create policies, and validate them without disrupting operations.
Policy Management
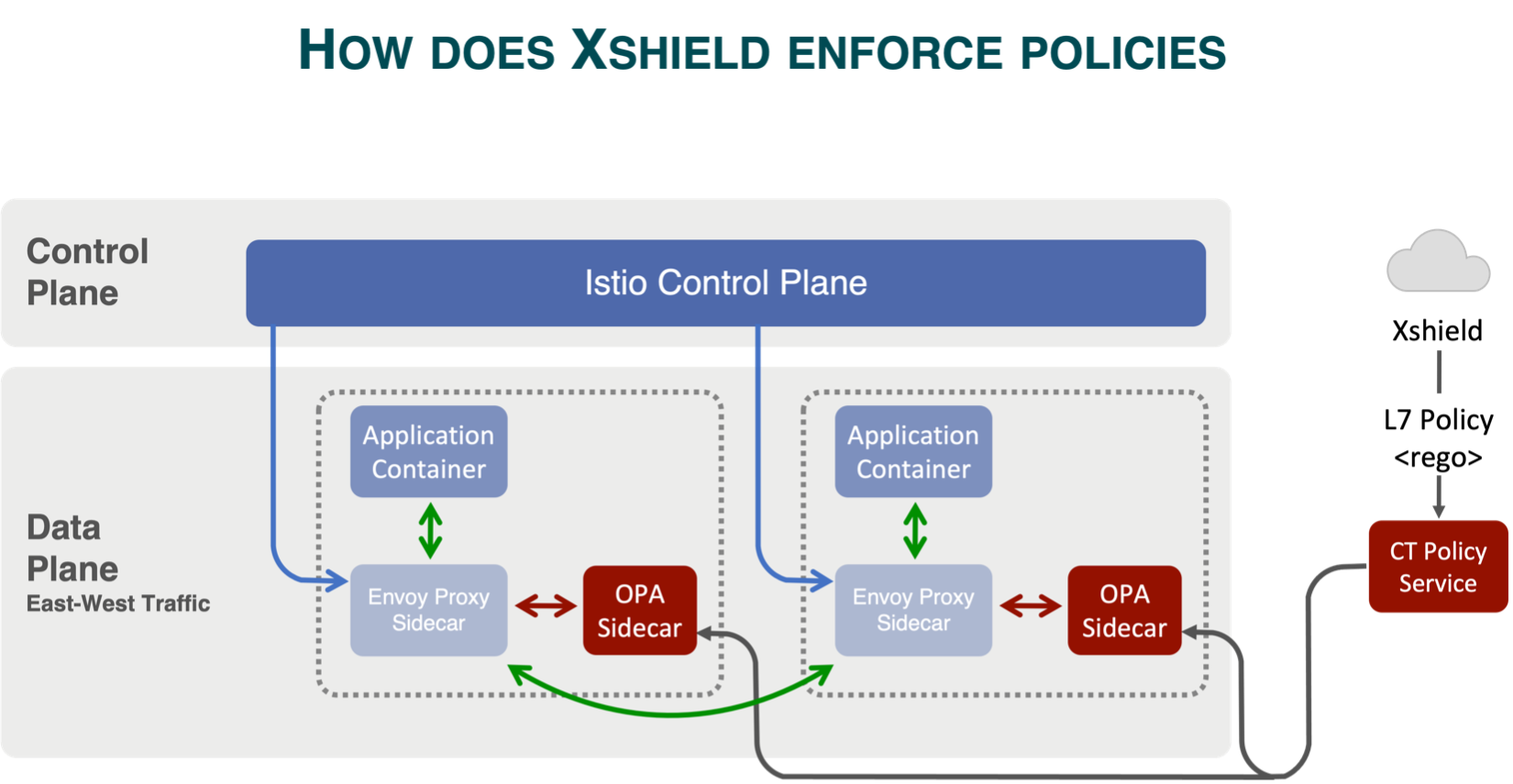
Xshield simplifies security in microservices by using API-level policies instead of unreliable IP-based rules.
It lets teams visualize service interactions, spot gaps, and apply precise, reusable policies.
Policies work across Kubernetes and external services, staying effective despite IP or network changes.
With OPA and Envoy integration, Xshield ensures fast, scalable, and consistent enforcement.
Kubernetes Building Blocks
- Pod: The smallest unit in Kubernetes, representing one or more containers.
- Service: Exposes a set of pods as a network service.
- Namespace: Provides a mechanism to isolate groups of resources.
- Deployment: Manages a replica set and rolling updates of pods.
Istio
Istio is a service mesh that provides a way to control how microservices share data with one another. It decouples traffic management, observability, and security from the application code.
The Istio architecture has two planes:
- Control Plane: Manages configuration and policies.
- Data Plane: Handles all the traffic between services using Envoy proxy sidecars injected into each pod.
Each microservice communicates through an Envoy proxy, which forwards traffic and enforces security policies. The control plane configures the proxies and aggregates telemetry.
Building blocks for Container Security
-
Assets - Each Kubernetes service is represented as an Asset in Colortokens. This encapsulates the ephemeral nature of Pods and enables the user to visualize the communication between services
-
Named Networks - A named network allows the user to group related networks to summarize communications between those networks and the critical assets.
- pod-network → Pod-to-pod communication.
- service-network → Internal services.
- external-ingress → Exposes services to the internet.
-
Segments - Segments are used in Container Segmentation to achieve the most effective first line of defence
-
Namespace Isolation: Xshield enforces API-level controls to isolate namespaces and prevent unauthorized cross-environment communication.
-
Application Ring-Fencing: Xshield enforces API-level controls to isolate applications and prevent unauthorized lateral movement.
-
-
Templates - Xshield analyzes API-level communication and recommends enforceable Zero Trust policies, eliminating the need for manually defining policies.
Policies are based on observed APIs and enforced at the service level for consistency in dynamic environments. Users can define reusable templates with rules, which are applied to matching assets via Segments.