SaaS Platform Management
Overview
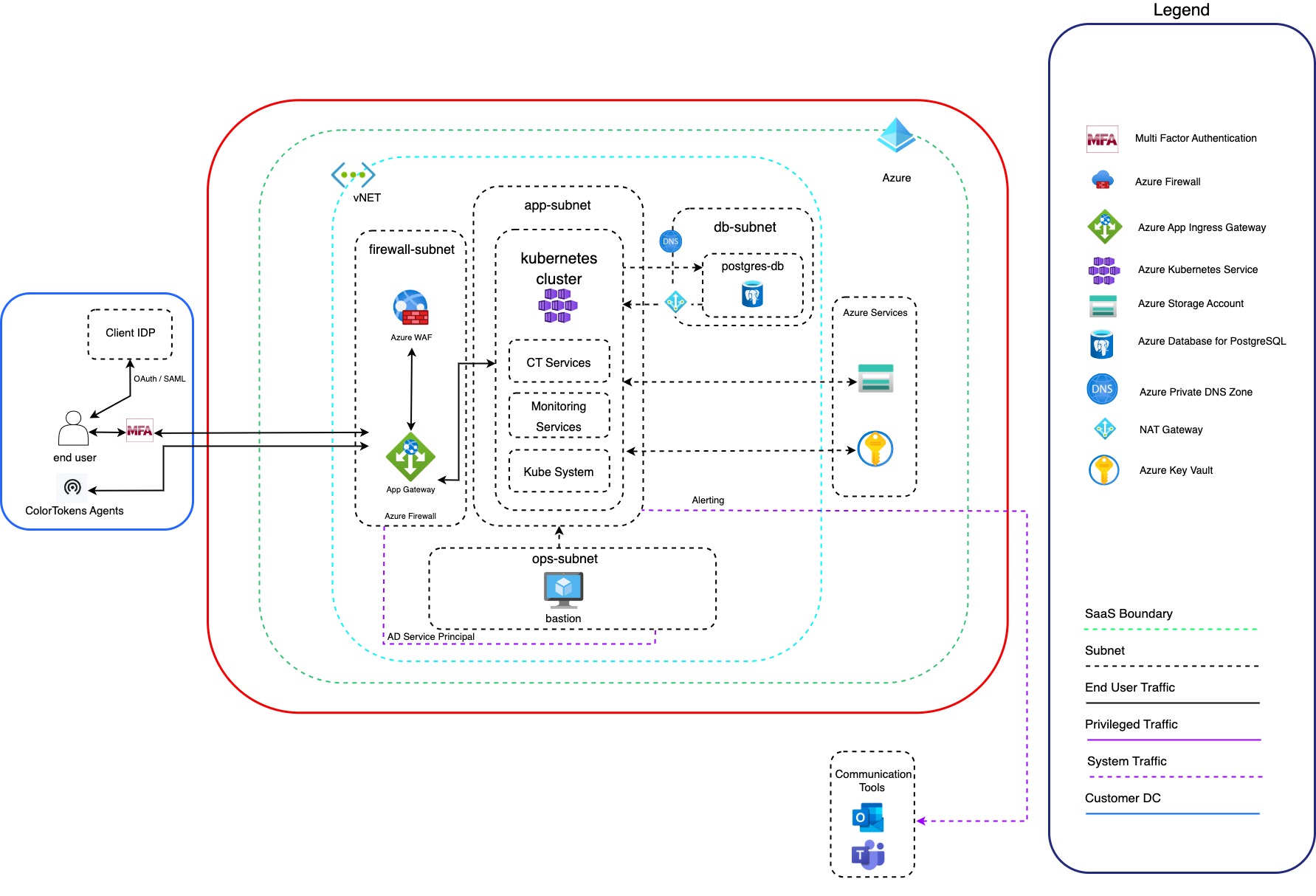
The Xshield Security Platform is delivered as a cloud-native SaaS solution hosted on Microsoft Azure using Azure Kubernetes Service (AKS). This architecture leverages Azure’s built-in security, scalability, and operational resilience to ensure robust protection of customer environments and continuous platform availability. With AKS, the platform benefits from automated scaling, self-healing containers, and seamless deployment pipelines, enabling rapid innovation without service disruption. Designed for enterprise-grade performance, the platform is architected to deliver 99.99% (four nines) availability, ensuring highly reliable access for mission-critical security operations.
Complementing this, Xshield uses Azure’s fully managed PostgreSQL service as its core database engine. This managed service provides built-in high availability, automated backups, and geo-redundancy, eliminating the operational overhead of database management while ensuring data durability and resilience. To meet data residency and compliance requirements, all data—while redundantly stored—is retained within the same Azure region as the deployment. By leveraging this cloud-native database layer, the platform achieves consistent performance, fault tolerance, and data integrity—key requirements for delivering a reliable, always-on security platform at scale.
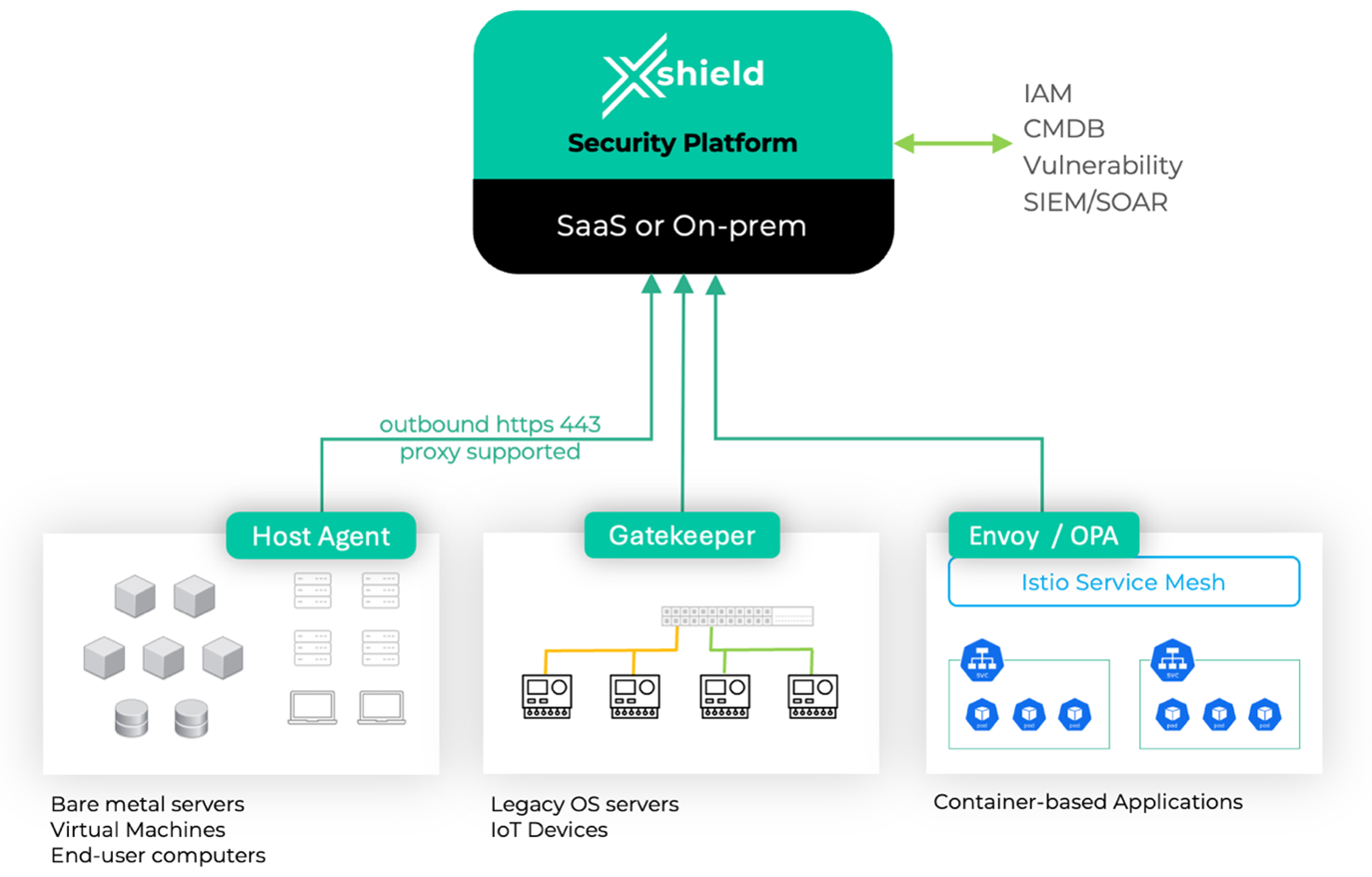
The Xshield platform supports the installation of a lightweight software component, the Xshield agent, on host servers and endpoints. All Xshield agents establish secure communication with the Xshield platform using TLS, authenticated by the platform’s server certificate. These encrypted channels are used by the agents to periodically transmit host and network metadata to the platform. In addition, the same secure connection is leveraged by the agents to retrieve updated policy configurations, which are then enforced locally by programming the host firewalls. Importantly, even in the event of temporary connectivity issues between the agent and the platform, the agent continues to enforce the last known security policies, thereby maintaining host protection without interruption.
To safeguard the platform against external threats, the Xshield Security Platform is front-ended by a Web Application Firewall (WAF). The WAF inspects all incoming traffic and filters out malicious requests, allowing only authenticated and well-formed requests to reach the backend services. This provides robust protection against Distributed Denial-of-Service (DDoS) attacks, injection attacks, cross-site scripting (XSS), and other common web-based threats. The WAF is a critical component in maintaining the integrity, availability, and security of the SaaS interface.
Additionally, the Xshield Platform is secured and orchestrated through an API Gateway, which ensures that only authenticated and authorized sessions can interact with the platform’s APIs and services. The API Gateway also incorporates rate-limiting, request validation, and threat detection capabilities. Combined with a cloud-native load balancer, the gateway efficiently distributes incoming traffic across multiple backend services to ensure both security and scalability under varying load conditions.
Platform and Data Security
Data at rest security
The platform employs 256-bit AES encryption, compliant with FIPS 140-2 standards, to secure all stored data. Encryption and decryption occur transparently and storage encryption cannot be disabled. This protection extends across all database storage, including disk data, backups, and temporary files generated during query execution.
Data-in-Transit Security
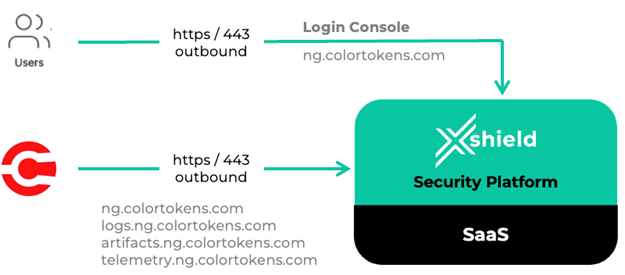
ColorTokens ensures the confidentiality and integrity of data in transit by leveraging industry-standard Transport Layer Security (TLS) 1.2 or higher, utilizing encryption keys aligned with CESG/NCSC recommendations. This encryption secures all communications between customer environments—such as web browsers—and the ColorTokens portal, as well as between ColorTokens agents deployed on customer assets and the portal.
In addition, all tenant and user communications are encrypted by default. The platform supports integration with Identity Provider (IdP) solutions to prevent unauthorized or unintended data transfers. To further enhance security and flexibility, ColorTokens also supports Bring Your Own Key (BYOK) and certificate management capabilities.
Tenant Administration
When a tenant is created for your organization, the designated Xshield administrator will receive an invitation via email. Once the invite is accepted, the administrator can add other members of the organization to the tenant. These members will then receive their own invites to set up access to the tenant via the portal.
Inviting Members
When a tenant is created for your organization, the designated Xshield administrator will receive an invitation via email. Once the invite is accepted, the administrator can add other members of the organization to the tenant. These members will then receive their own invites to set up access to the tenant via the portal.
To invite a member to the Xshield management portal:
- Navigate to Settings in the left navigation menu
- Select User Management
- Click on Invite Member button on the top right corner
- Enter the member's name and email address
- Assign the relevant role from the Role dropdown:
More information on user management and roles can be found in User Management section.
- Click Invite
The newly added user will receive an email invitation to set up their account. By following the link provided, the user needs to create a password and configure Single Sign-On (SSO), after which they will be able to access the portal.
Security Considerations
-
Enable SSO for Enhanced Security Enable Single Sign-On (SSO) via an Identity Provider (IdP) of your choice. Xshield supports OAuth and SAML 2.0 protocols.
See: Azure AD Integration & PingOne Integration for setup instructions.
-
Without SSO: Use MFA for Local Users If SSO is not used, members must enroll in Multi-Factor Authentication (MFA) provided by ColorTokens upon accepting their invitation. These users:
- Are considered local users
- Must create a password and use an authenticator app (e.g., Google Authenticator) for MFA
- Are stored in a local Microsoft Azure AD instance
-
Password Requirements for Local Users (Azure AD B2C – SaaS Default):
-
Minimum of 8 characters
-
Must include at least 3 of the following 4 categories:
- Uppercase letters
- Lowercase letters
- Numbers
- Symbols
-
-
On-Premise Deployment Authentication Options (set at cluster level):
-
Customer IdP Integration
- Integrate with the customer’s existing IdP (SAML) to enable SSO.
-
No-Auth (without IdP integration)
- Tenant users can access without passwords or authentication.
-
Local Users with KeyCloak
- Cluster uses KeyCloak as a local IdP.
- Users must authenticate using a password.
Password rules (configurable):
-
No default password policy enforced, but typically:
-
Minimum of 16 characters
-
Must include at least 3 of the following 4 categories:
- Uppercase letters
- Lowercase letters
- Numbers
- Symbols
-
-
Xshield Management Portal
The Xshield Management Portal provides a centralized interface for securing and monitoring your IT infrastructure. The Dashboard serves as the homepage.
Navigation
-
Left Navigation Menu Access all Xshield Microsegmentation features
-
Profile Icon (Top-Right Corner) For accessing Tenant features
- Organizations (If the user is a member of more than one organization)
- System Tasks
- Theme
- Language
- Logout
Key Features
-
Configurable Session Timeout The portal allows you to configure the session timeout in the Settings > General section. The default session timeout is twenty four (24) hours.
-
Filters & Queries Use filtering options to filter the required data such as Assets, Ports etc. based on search criteria.
For comprehensive guidance on managing Xshield, refer to the articles available in the Core Concepts section.