Lab Setup
Basic Lab Setup
Please refer to the basic Xshield Lab setup guide for the base setup.
Deploying the server segmentation lab
In this demonstration, we will begin by building basic security (blocking malicious and risky communications, restricting management and infrastructure ports) followed by allow-listing environment-specific traffic flows.
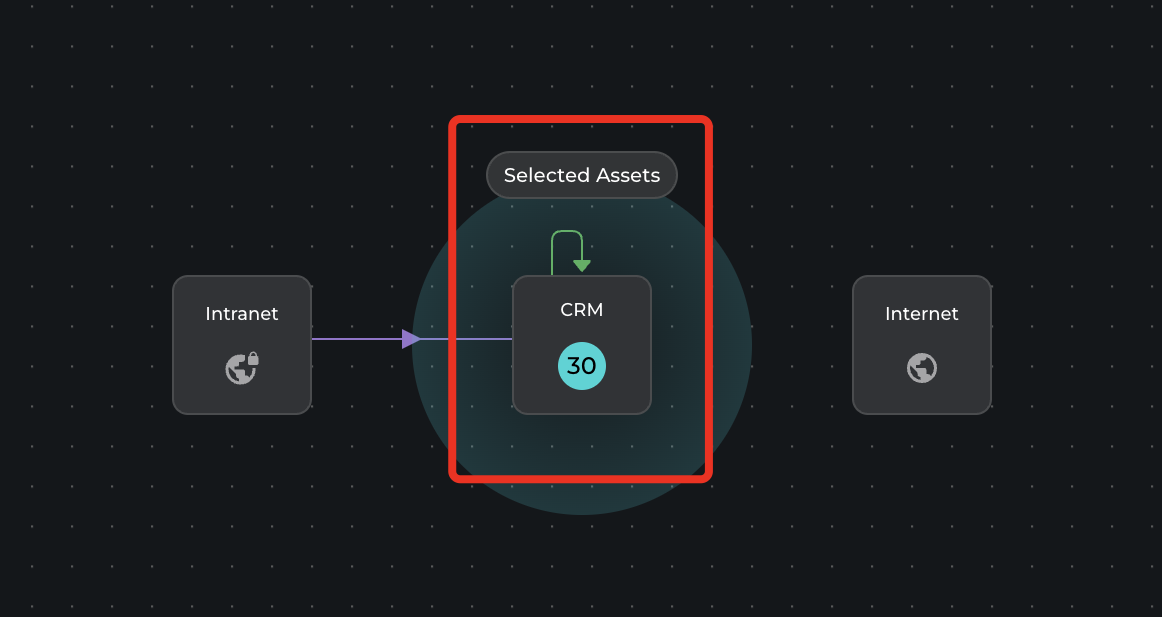
we are using a CRM application use case to segment production vs Non-production environments. The goal is to progressively implement microsegmentation policies, starting with the Location and Environment layers, and advancing to the Application layer. This approach gradually reduces the attack surface and lowers the risk of blast radius at each stage.
To deploy the lab environment specific to server segmentation and this use case, follow the steps below:
Steps to Deploy the Lab Environment:
- Make sure you are in the directory with the
xshield_lab.pyscript (either /etc/colortokens/lab or directory where the xshield lab package is downloaded) - Run the following commands to activate the python virtual env if it's not activated yet or if a new ssh session of the VM is started
source .venv/bin/activate
- If you want to deploy the default demo lab available for server segmentation use case mentioned above, then just run the command to launch xshield lab tool and Select Option 1: Create Lab Environment for Server Segmentation.
python3 xshield_lab.py
- If you are deploying the lab for customized use case, provide the correct paths for lab and traffic config yaml files from your VM along with the xshield lab tool command
- Make sure your lab config file should be named as "<usecase>_lab.yaml" and traffic config file should be named as "<usecase>_lab_traffic_yaml"
python3 xshield_lab.py --lab-config <path/to/lab/config/file>/<usecase>_lab.yaml --traffic-config <path/to/traffic /config/file>/<usecase>_lab_traffic.yaml
You’ll see the following menu:
root@util-01:/home/ctuser/xshieldUtil/lab# python3 xshield_lab.py
INFO - Reading configuration from /home/ctuser/xshieldUtil/config/config.yaml
Welcome to the Xshield Lab Environment setup tool.
1. Create Lab Environment for Server Segmentation
2. Create Lab Environment for Container Segmentation
3. Create Lab Environment for Gatekeeper
4. Create Lab Environment for User Segmentation
5. Create Lab Environment for CrowdStrike Integration
6. Create Lab Environment for Cloud Segmentation (Beta)
7. Customize Lab Environment
8. Remove Lab Environment
9. Remove Docker Images
10. Exit
Final Result
The setup process will create 30 assets that can communicate with the tenant on the Xshield platform.
Image - To be added
Demo Lab Components & Topology
Key Components:
1. Networks:
- Managed Network:
172.16.0.0/24 - Unmanaged Network:
172.20.0.0/24
2. Devices (Nodes):
- Controller: Acts as a gateway between the managed and unmanaged networks.
- CRM Web Server: Managed nodes of WEB role for Prod and Test env connected to the managed network.
- CRM App Server: Managed nodes of APP role for Prod and Test env connected to the managed network.
- CRM DB Server: Managed nodes of DB role for Prod and Test env connected to the managed network.
- Nextcloud Client: An unmanaged node connected to the unmanaged network.
- Nextcloud IT Admin: An unmanaged node connected to the unmanaged network.
- Nextcloud AD Infra (US): An unmanaged node connected to the unmanaged network.
3. Routing & Gateways:
- The controller device has interfaces in both the managed network (
172.16.0.1) and unmanaged network (172.20.0.1), acting as a routing bridge between them. - The managed nodes (Web Server, App Server, DB Server) all communicate through the controller’s managed network interface.
- The unmanaged nodes (Client, IT Admin, AD Infra) communicate through the controller’s unmanaged network interface.
4. Network Configurations:
- The controller enables IP forwarding and masquerading, allowing communication between the two networks.
- Each node in the managed network has a gateway of
172.16.0.1. - Each node in the unmanaged network has a gateway of
172.20.0.1.
Network Topology Diagram:
Here’s a textual description of the topology:
-
Managed Network (172.16.0.0/24):
- CRM App Servers (Prod -
172.16.0.2-172.16.0.6, Test -172.16.0.7-172.16.0.11) - CRM DB Servers (Prod -
172.16.0.12-172.16.0.16, Test -172.16.0.17-172.16.0.21) - CRM Web Servers (Prod -
172.16.0.22-172.16.0.26, Test -172.16.0.27-172.16.0.31) - Controller (
172.16.0.1)
- CRM App Servers (Prod -
-
Unmanaged Network (172.20.0.0/24):
- Nextcloud IT Admin (
172.20.0.2) - Nextcloud Client (
172.20.0.3) - Nextcloud AD Infra (
172.20.0.4) - Controller (
172.20.0.1)
- Nextcloud IT Admin (
Policy Modelling
1. Allowed Traffic:
- Web Prod --> App Prod (9000), DB Prod(22), AD Infra(389, 53)
- App Prod --> DB Prod (3600, 21), AD Infra(389, 53)
- DB Prod --> App Prod(21, 22), AD Infra(389, 53)
- Web Test --> App Test (9000), DB Test (22), App Prod(9000), DB Prod(3306), AD Infra(389, 53)
- App Test --> DB Test (3600, 21), AD Infra (389, 53)
- DB Test --> App Test (21), AD Infra (389, 53)
- NextCloud client --> Web Prod (443), Web Test (443, 80), App Prod (22)
- NextCloud IT Admin --> Web Prod (22), App Prod (22), DB Prod (21, 22)
2. Denied Traffic:
- NextCloud Client to App Prod Server on Port 22
- IT Admin to DB Server on Port 3306
- Web to DB Server on Port 22
- App to DB Server on Ports 21/22
- DB to App Server on Ports 21/22
Recovery Instructions
If you need to reconnect the lab environment after a host restart
- Follow the Recovery of Demo Lab Environment instructions
If you want to recreate the lab environment completely by deleting and rebuilding it
- Follow the Remove Lab Environment instructions
- Return to the Steps to Deploy the Lab Environment section above