Port Level Zero Trust
Port Level Zero Trust is a granular security approach that applies Zero Trust principles at the port level, allowing organizations to secure their network communications with precision and flexibility. This methodology enables security teams to apply tailored security policies to specific network ports rather than implementing blanket policies across entire assets or networks.
Introduction: A Modern, Iterative Approach
Prioritized security - You can secure your most critical or vulnerable ports first (like SSH or RDP) without waiting for a complete security plan for all ports.
Faster time-to-security - Critical vulnerabilities get addressed immediately rather than waiting for a comprehensive deployment.
Operational confidence - Operations team gain confidence in the process as they see successful, non-disruptive implementations accumulate.
Adaptability to changing environments
Key Concepts
- Agile Microsegmentation: Apply Zero Trust iteratively, securing high-risk services first
- Template-based policy testing
- Port-level granular deployment
- Per-port testing cycles
- Iterative refinement without impacting existing policies
- Reduced disruption risk while securing critical infrastructure
Policy Types
Port Policy: Port level control using templates
Note: Policies are ordered by highest priority first.
| Policy | Description |
|---|---|
| Denied | All traffic is denied using port policy |
| Restricted to paths | Only paths mentioned in policy are allowed |
| Allow Intranet only | Only Intranet traffic is allowed |
| Allow All | All traffic is allowed using port policy |
Asset Policy: Fallback for all other ports which are not covered by port policy
Note: Policies are ordered by highest priority first.
| Policy | Description |
|---|---|
| Zero Trust | This strict mode blocks all ports unless explicitly permitted, aligning with the Zero Trust principle of 'never trust, always verify' and significantly reducing the attack surface. |
| Allow Active Ports | Ports that have been used in the last 30 days stay open to prevent disruptions to active services. |
| Allow Open Ports | Existing open ports remain accessible during deployment, ensuring uninterrupted communication between applications. |
| Allow All | All ports are open by default, allowing traffic to flow while administrators refine security rules. Caution should be exercised, as this may expose vulnerabilities. |
Port Status
Note: Statuses are ordered by highest priority first.
| Status | Description |
|---|---|
| Allow All (System) | All traffic is allowed by system default rules |
| Denied | All traffic is denied using port policy |
| Restricted to paths | Only paths mentioned in policy are allowed |
| Allow Intranet only | Only Intranet traffic is allowed |
| Allow All | All traffic is allowed using port policy |
| Allow All (Asset Policy) | All traffic is allowed by asset policy (Allow all, Allow open, Allow active) |
| Denied (Asset Policy) | All traffic is denied by asset policy (Zero trust) |
| Unreviewed | No policy |
Enforcement Rule for Path-Based Policies
If a path rule is applied to a port that is Unreviewed (i.e. no port rule is configured and the asset policy does not include this port), the enforced status of port will be Restricted to Paths. Otherwise, the enforced status of port will be Denied (Asset Policy).
Note: The candidate status of port will remain Unreviewed until user reviews the port with a port based rule.
Deployment Modes
| Mode | Description |
|---|---|
| Under Test | Traffic which is not allowed by policy is logged as violation without blocking |
| Enforced | Traffic which is not allowed by policy is blocked and recorded as blocked communication attempt |
Auto Deployment
Once you enable the Auto Deployment for a segment, all pending changes will be deployed under test immediately on detection of changes. If auto deployment mode is set to enforce, new changes will still be pushed under test immediately, system will then enforce tested policies as per the enforcement criteria periodically.
Note: Assets that have disabled deployment will not participate in auto deployment.
Asset States
| Asset State | Description |
|---|---|
| Unsecure | No policies are deployed |
| Partially Secure | Only individual port policies are deployed; asset-level policy is not deployed |
| Secure Test | Port policies may be deployed; asset-level policy is under test |
| Secure* | Asset level policy is in enforce mode; some port policies may still be under test |
| Secure | Both asset and port policies are in enforce mode |
Deployment Workflow
From the asset list, select the assets you want to deploy.
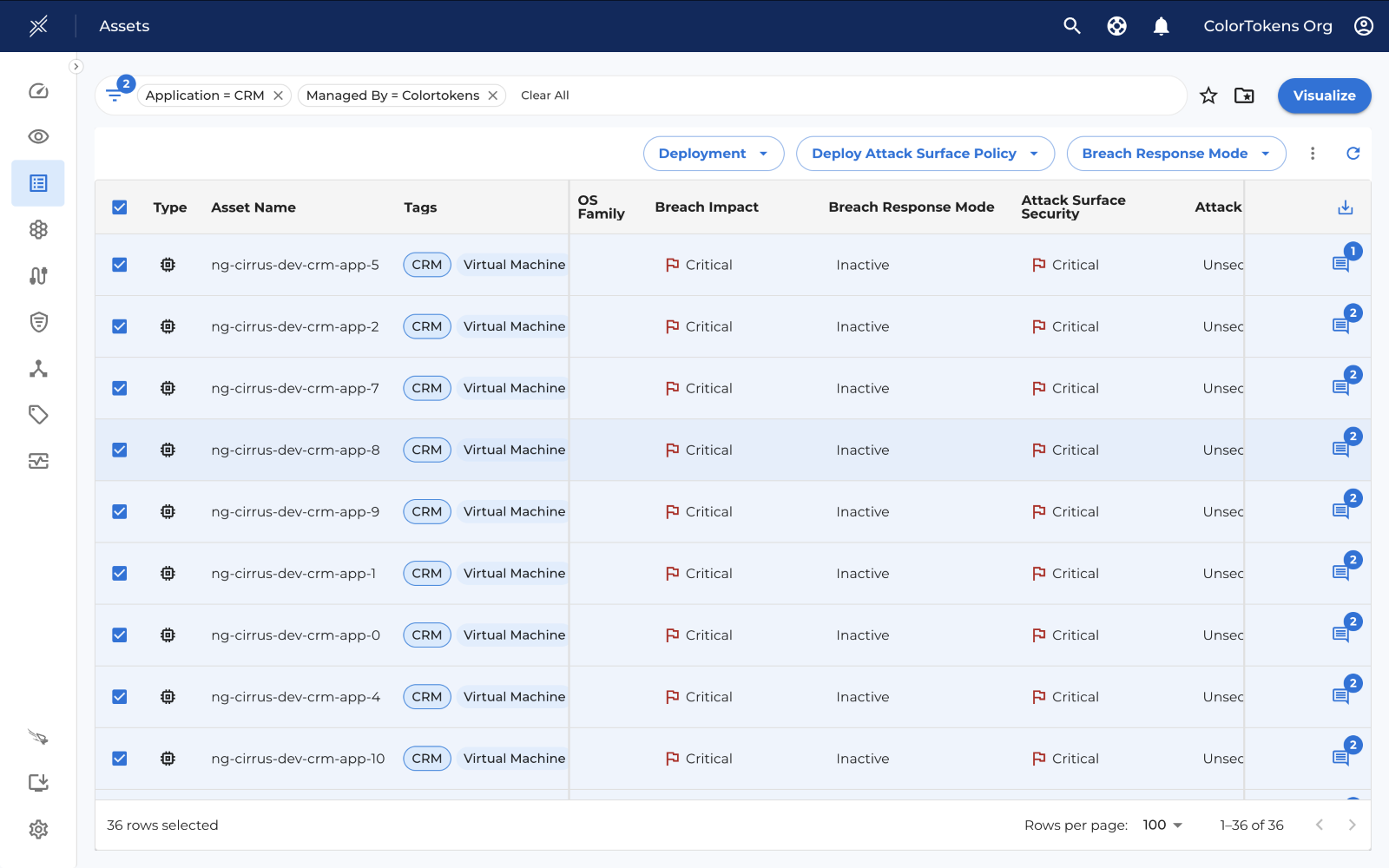
Deployment Control
Deployment control has 2 options:
- Enable Deployment: Enables the deployment process, allowing you to proceed with applying policies to the selected assets.
- Disable Deployment: This will disable future deployments and will remove existing policies.
Note: Deployment is by default enabled.
Deployment Methods
Policies can be deployed using two methods:
-
Full Deployment: Allows you to directly deploy policies in either Test or Enforce mode with minimal configuration. Whenever a policy is changed, whether it's an update to the policy itself or any related configuration, and you deploy using the full deployment method in either Test or Enforce mode, it triggers a complete fresh deployment. This means all previously deployed policies will be re-deployed in the mode you choose.
-
Micro Deployment: The Micro Deployment method gives you full control over policy deployment, allowing for a more progressive and flexible approach. You can selectively deploy port and asset policies based on their readiness and choose to deploy them in either Test or Enforce mode as needed.
Note: Micro deployment is disabled by default, to enable it, go to Settings > General > Micro Deployment. Additionally, assets deployed before micro deployment feature release will need to be deployed once in full deployment to become compatible with micro deployment.
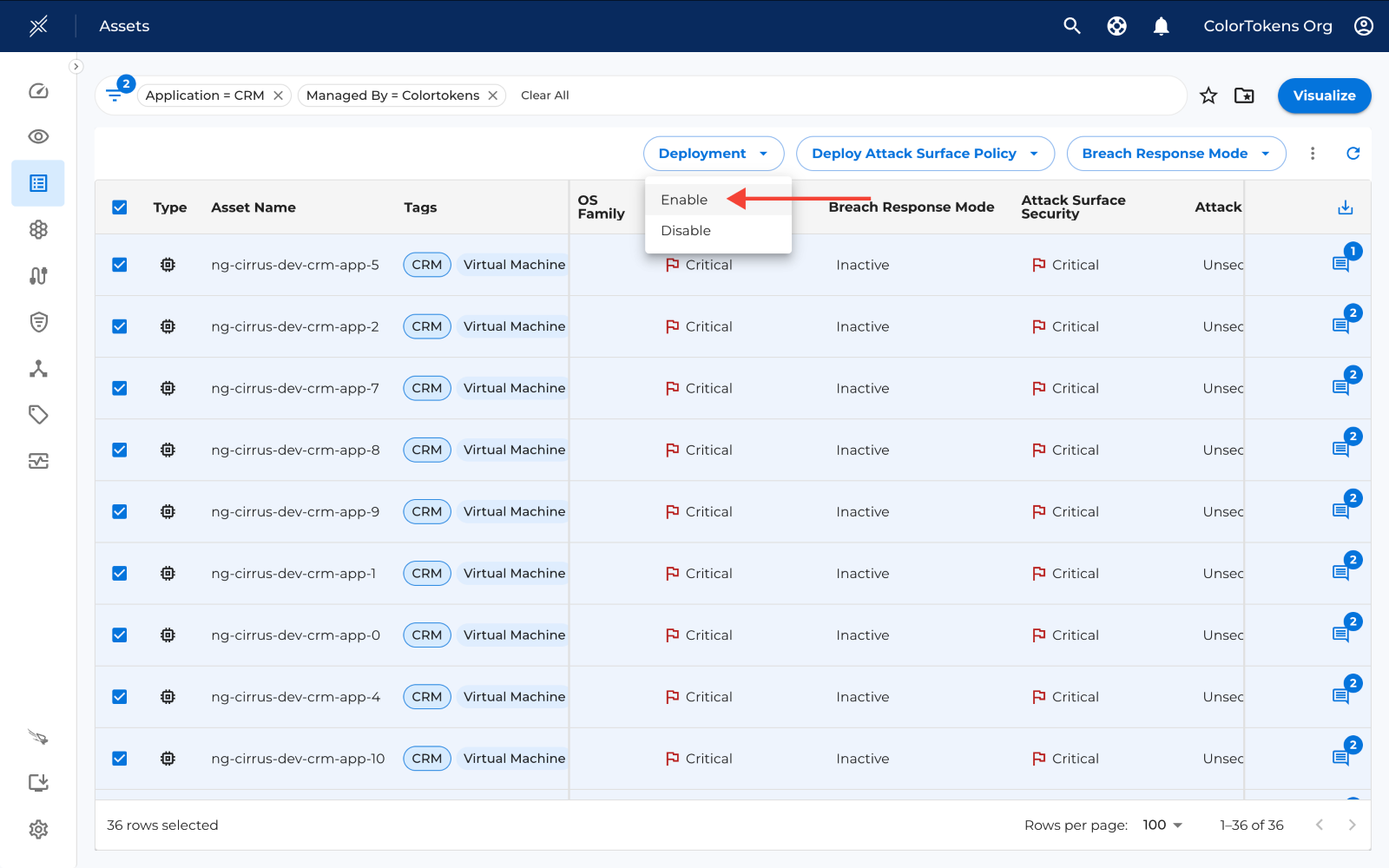
Deploy with full deployment method
To deploy using full deployment method, click on the deploy button to see the options, to deploy in test mode click on "Test", similarly to deploy in enforce mode click on "Enforce".
Once you click on the desired option, a drawer opens from where you can directly click on "Confirm Deployment" to deploy the policy.
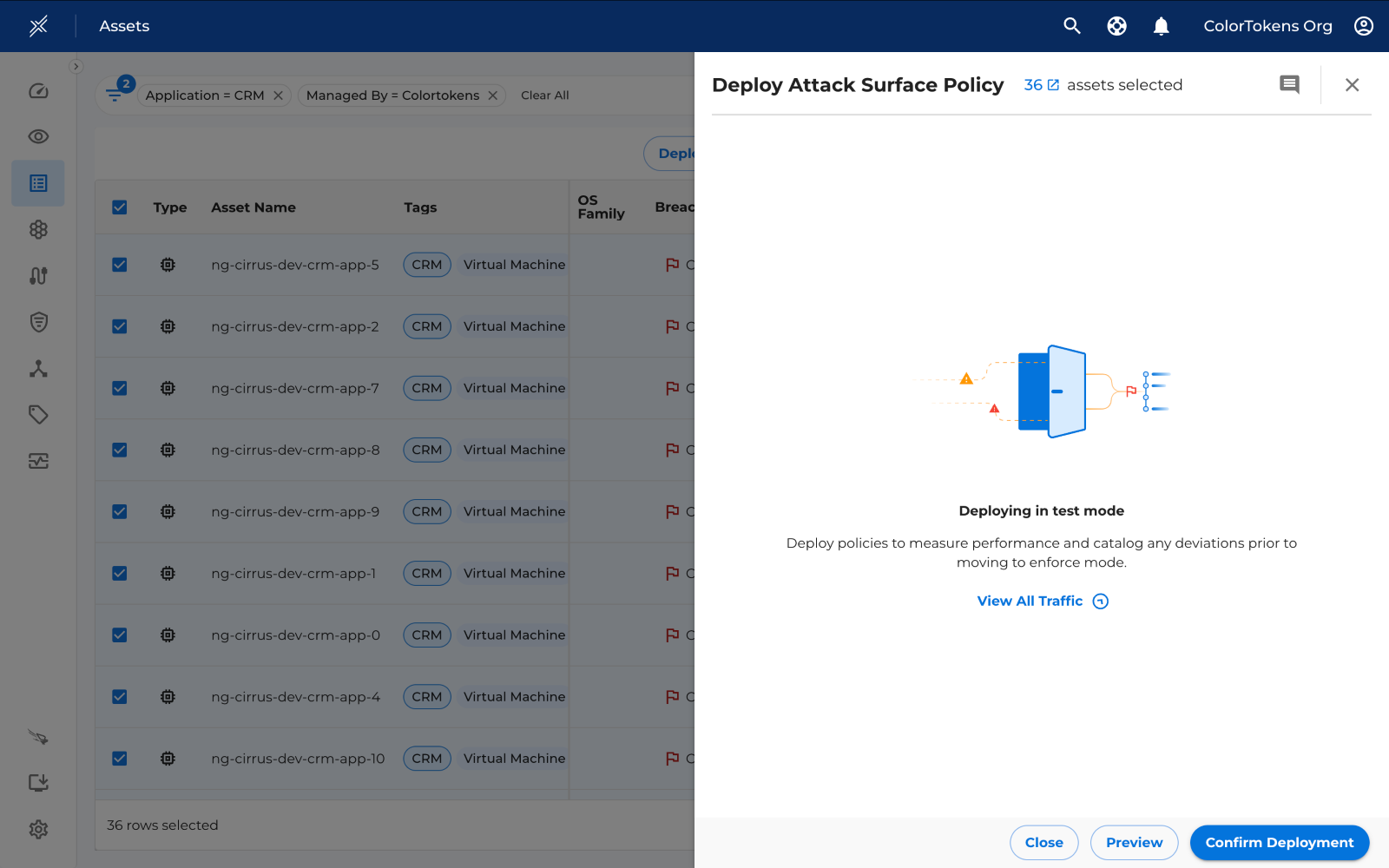
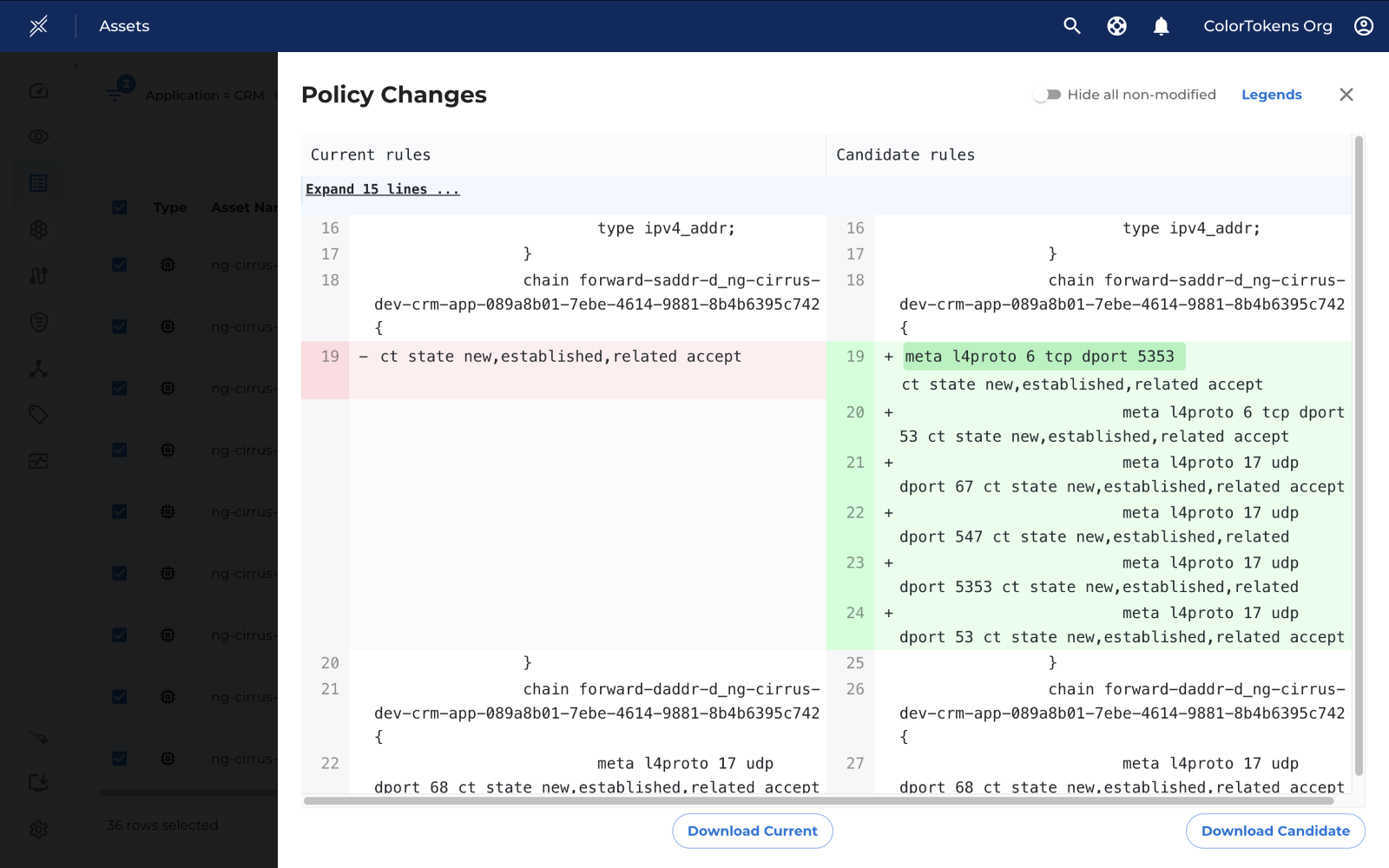
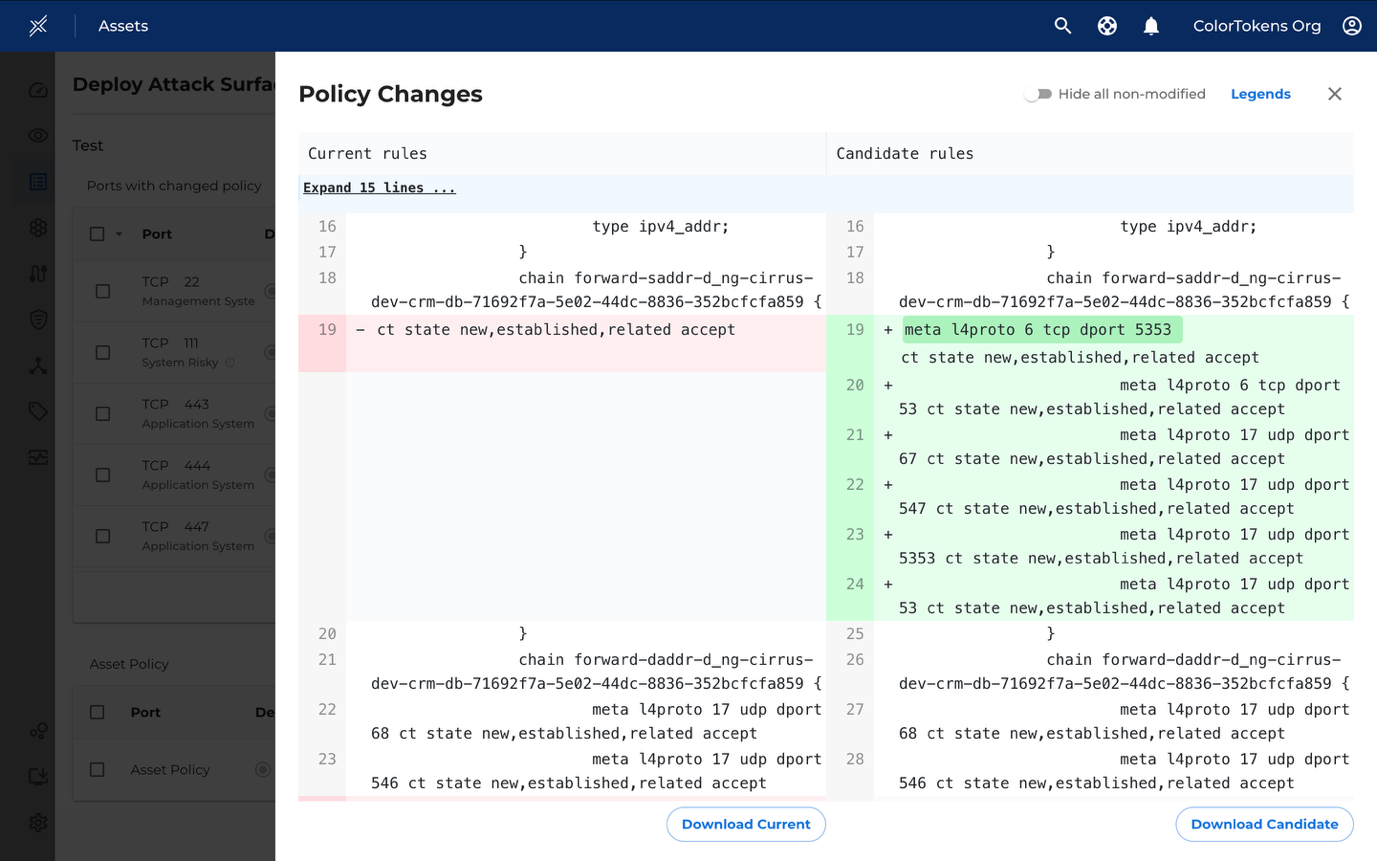
By clicking on Preview, you can view a list of assets and examine the changes individually for each asset.
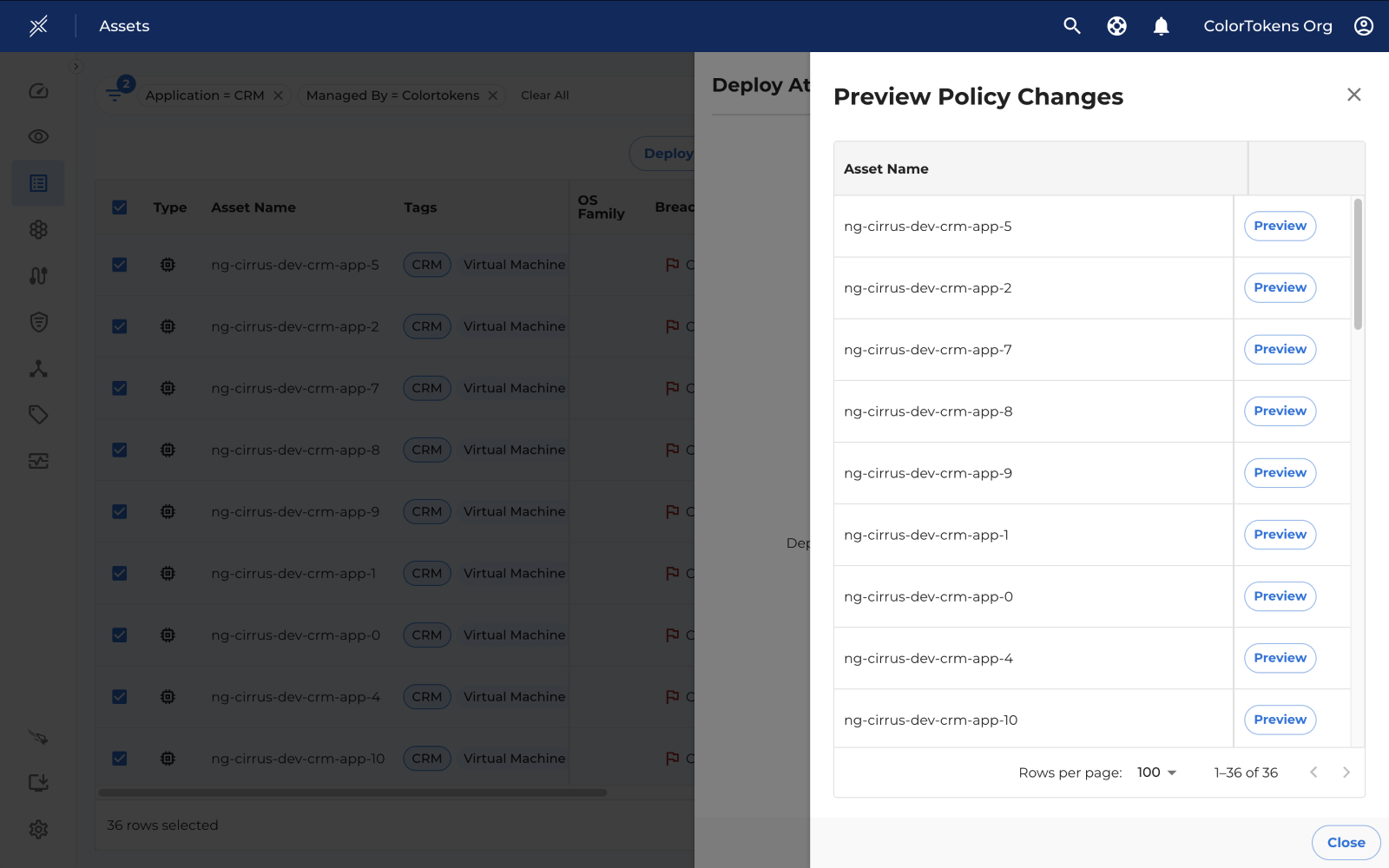
This drawer shows the changes in the policy.
Deploy with micro deployment method
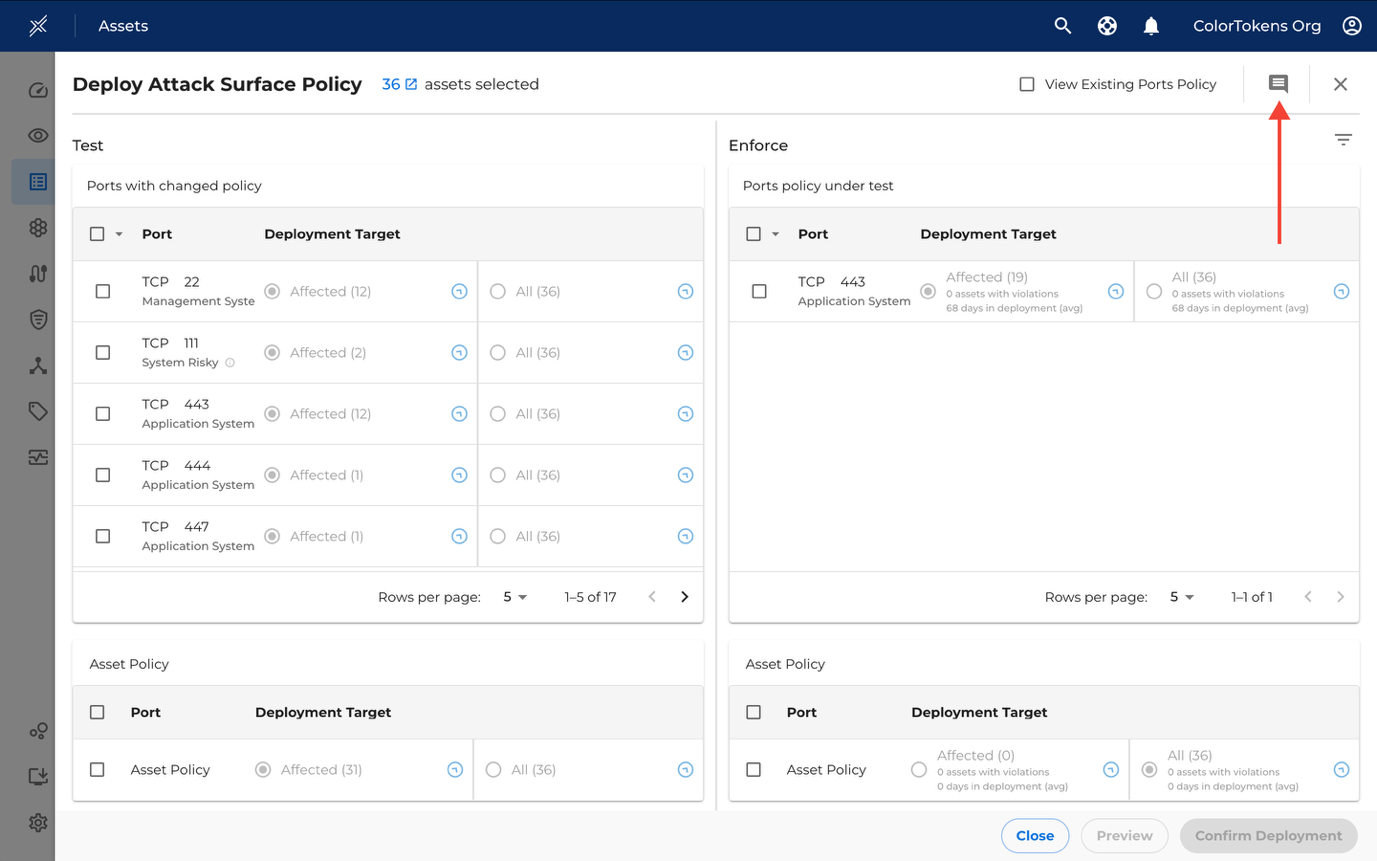
To deploy policies at a more granular level, where you can choose to deploy asset and port policies selectively in different deployment modes, use the Micro Deployment method.
In the Micro Deployment window, there are three tabs to help manage policy deployment:
-
Pending Test: This tab displays a list of ports and asset policies which have either been changed since last deployment or newly applied.
-
Pending Enforce: This section shows policies that have been in Test mode for at least 7 days without any violations. You can also customize the default settings to suit your preferences. Click here to learn more about the filters.
-
Under Test: This tab displays a list of ports and asset policies which are currently under test, you can undeploy these policies using this tab.
-
Enforced: This tab displays a list of ports and asset policies which are currently enforced, you can move these back to test using this tab.
Filters
In the Enforce section, filters allows you to:
- View ports with or without policy violations
- Change the number of days port has spent in Test mode.
NOTE: While you can customize the filters to view ports as needed, it is not recommended to modify the default settings. The recommended and default filter is "Assets with no violations". Ideally, ports should remain in Test for a minimum of "7" days before being enforced.
Policy Preview
To view policy changes, click on "Preview" next to the respective asset row.
Test Intranet vs Test All
In the Pending Test tab, under the Asset Policy section, you will find two options:
-
Test All: The asset policy will be in Test mode for both intranet and internet traffic.
-
Test Intranet: The asset policy will be in Test mode for intranet, while it will be enforced for internet traffic.
Annotations
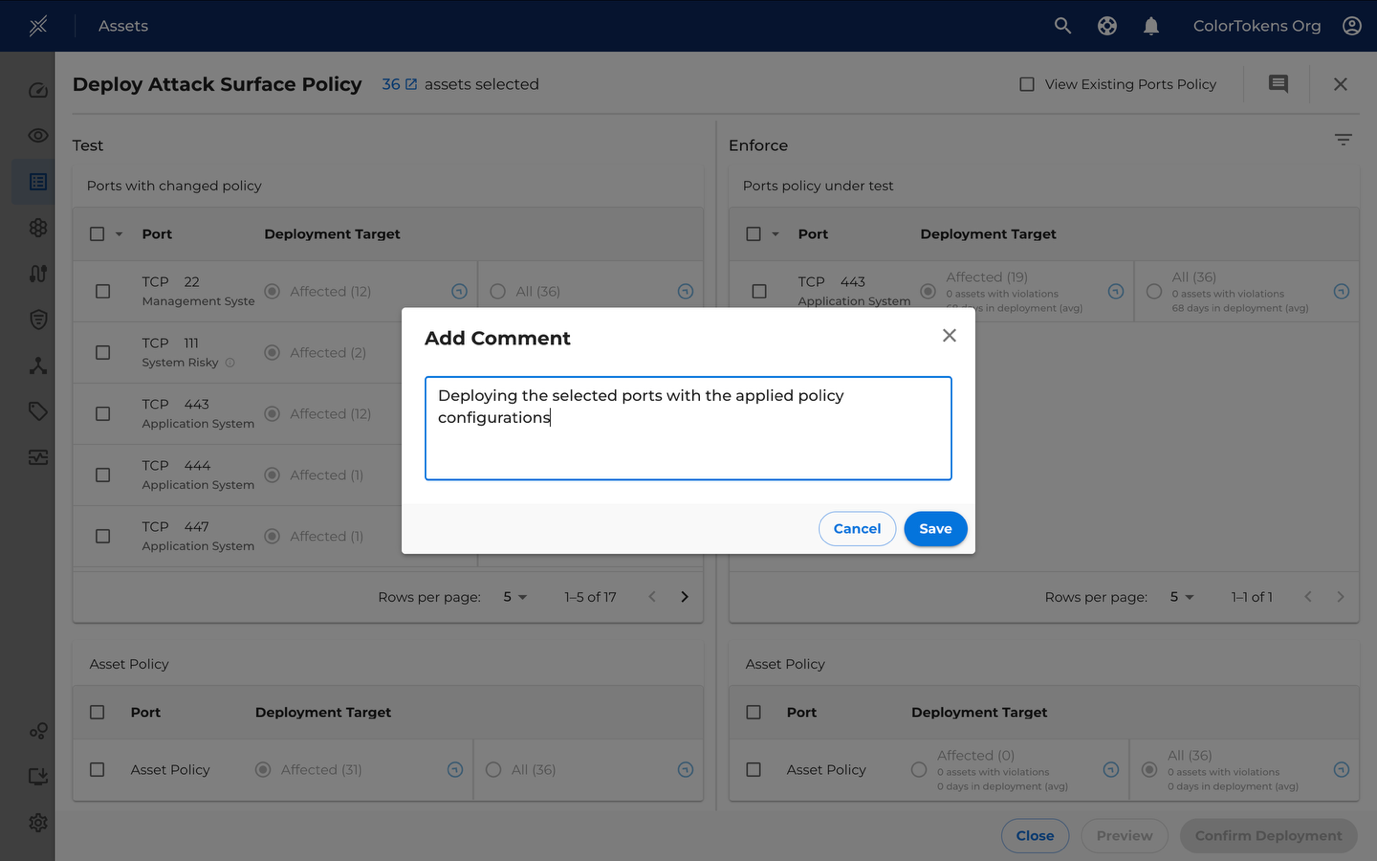
To deploy policies more efficiently and communicate with other users, you can add comments or annotations to highlight specific details about the deployment.
Viewing deployment in asset detail page
After the policies are deployed you can view them for each asset in assets page. Navigate to assets list page and click on a particular asset name to open its detail page as shown below:
Below are the deployment details and the policies applied during the deployment.
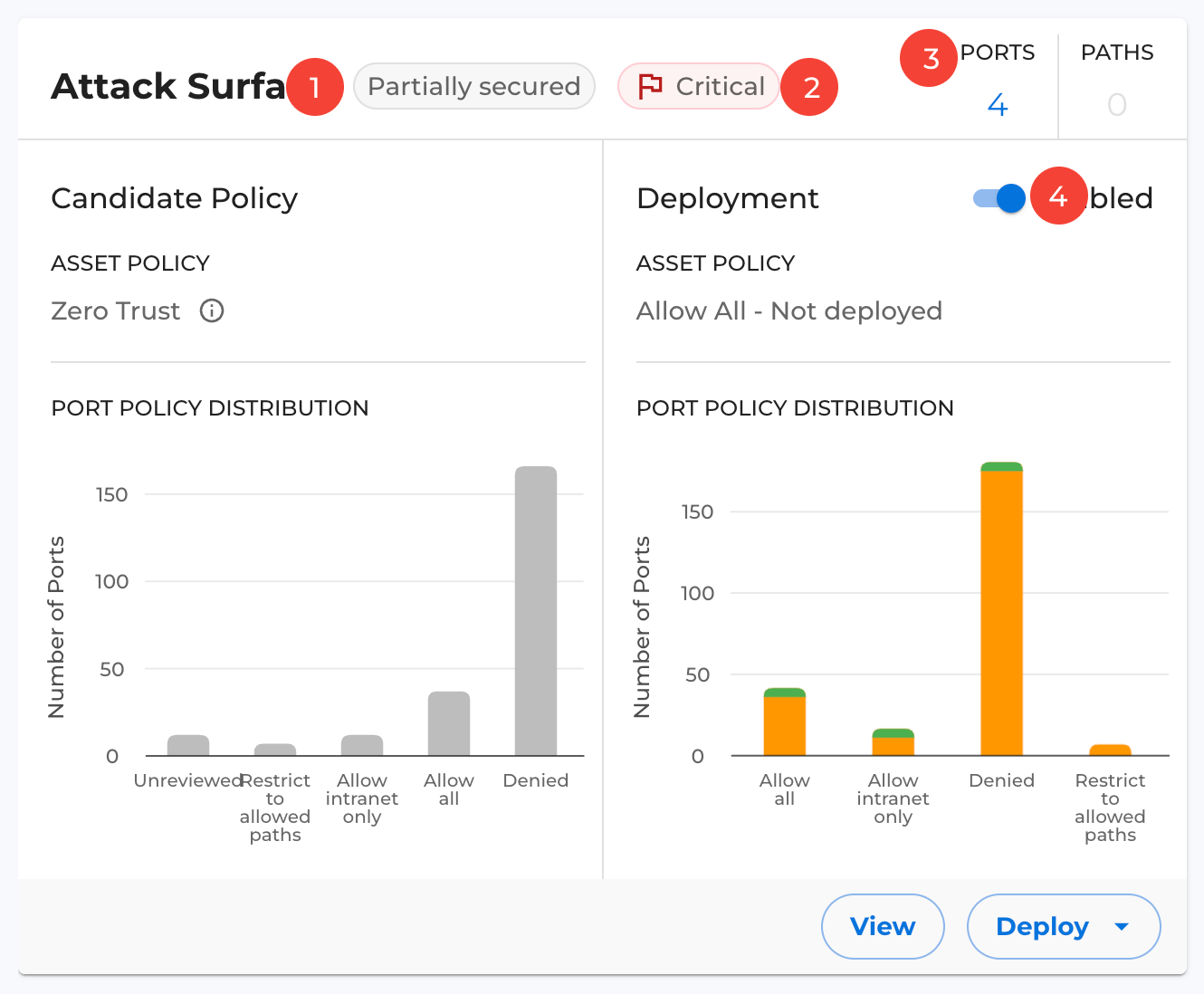
-
Attack Surface/Blast Radius Status: Represents the overall security state of the asset's attack surface/blast radius.
-
Security State: Indicates the status of attack surface protection.
-
Observed Traffic: Displays the count of ports and paths based on observed traffic.
-
Deployment Toggle: Allows you to enable or disable policy deployment for the specific asset.
Note: In the case of Inbound representation (i.e., the Attack Surface chart), the visualization shows both the count of observed ports, and the total ports added via port policies (from templates), as illustrated above.
In contrast, for Outbound (i.e., the Blast Radius chart), the chart displays only the count of port policies, not the observed ports.
The card below is divided into two main sections:
-
Future Policy (Left Section): Displays details of the future policy, including the distribution of ports based on their respective policy states. This section consists of two components: asset policy and port policy distribution, visualized in the grey-colored graph shown above.
-
Deployment (Right Section): Displays the deployment details, including a toggle at the top to enable or disable deployment. This section consists of two components: the deployed port policy and the port policy distribution after deployment. The graph shows the number of deployed ports by state:
- Grey: Not deployed
- Green: Enforced
- Yellow: Under Test
You can also view a detailed deployment breakdown by hovering over the bars in the graph, as shown below.
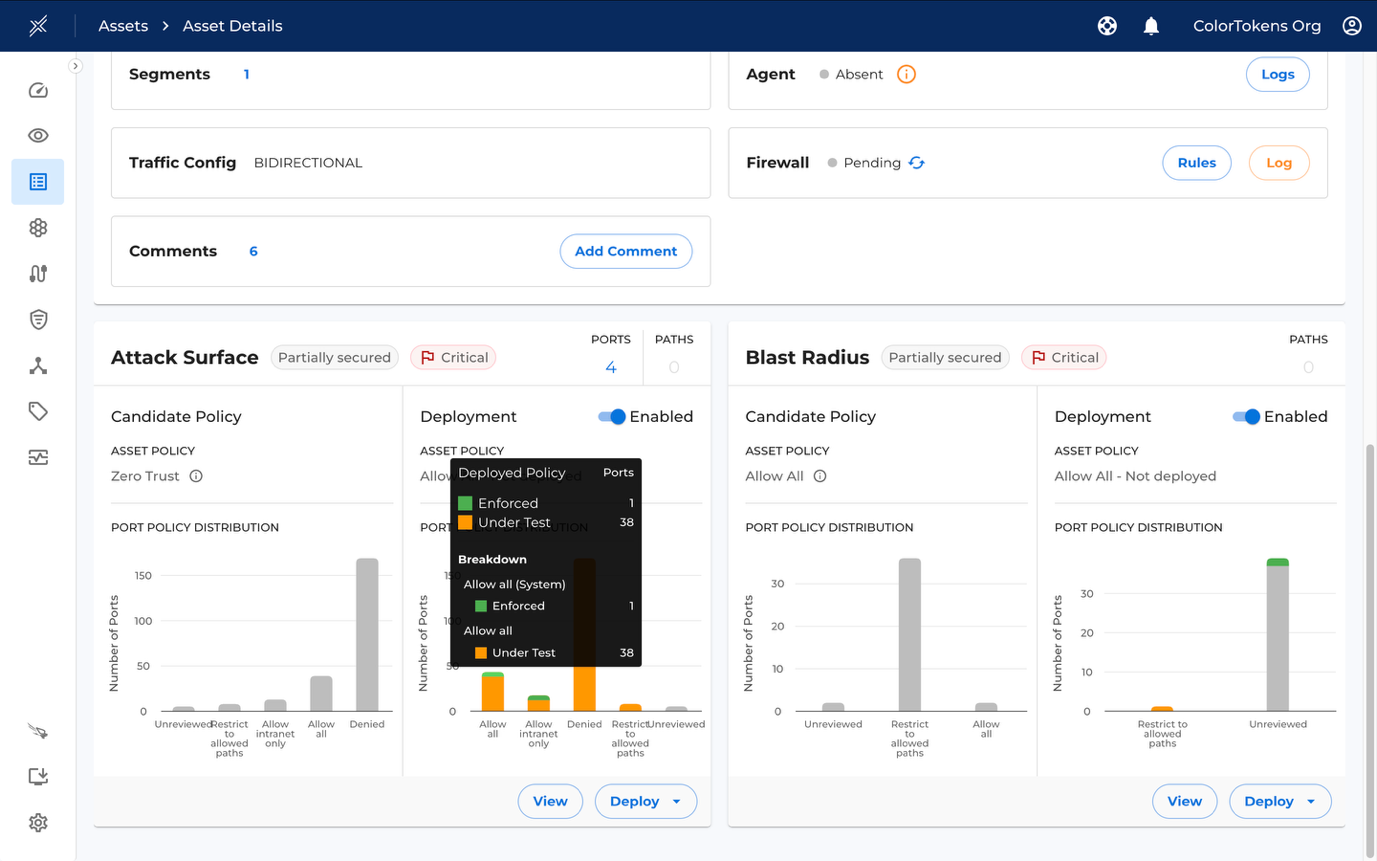
The controls below "View" and "Deploy" allow you to view the port and asset policies, while "Deploy" initiates the deployment flow for the selected asset.
Policy Breakdown
You can view the policy breakdown of an asset by clicking the View button in the attack surface/blast radius card or by clicking on View Policy button in the templates box.
There are two categories of policies namely Port Policies and Asset Policies as described in the Policy Types. The following definitions apply to both categories:
-
Current Deployment State: Indicates whether the latest candidate policy has been deployed and in what mode.
-
Current Port Policy: Shows the current deployed state of the policy.
-
Future Port Policy: Represents the final status derived from the applied policy templates.
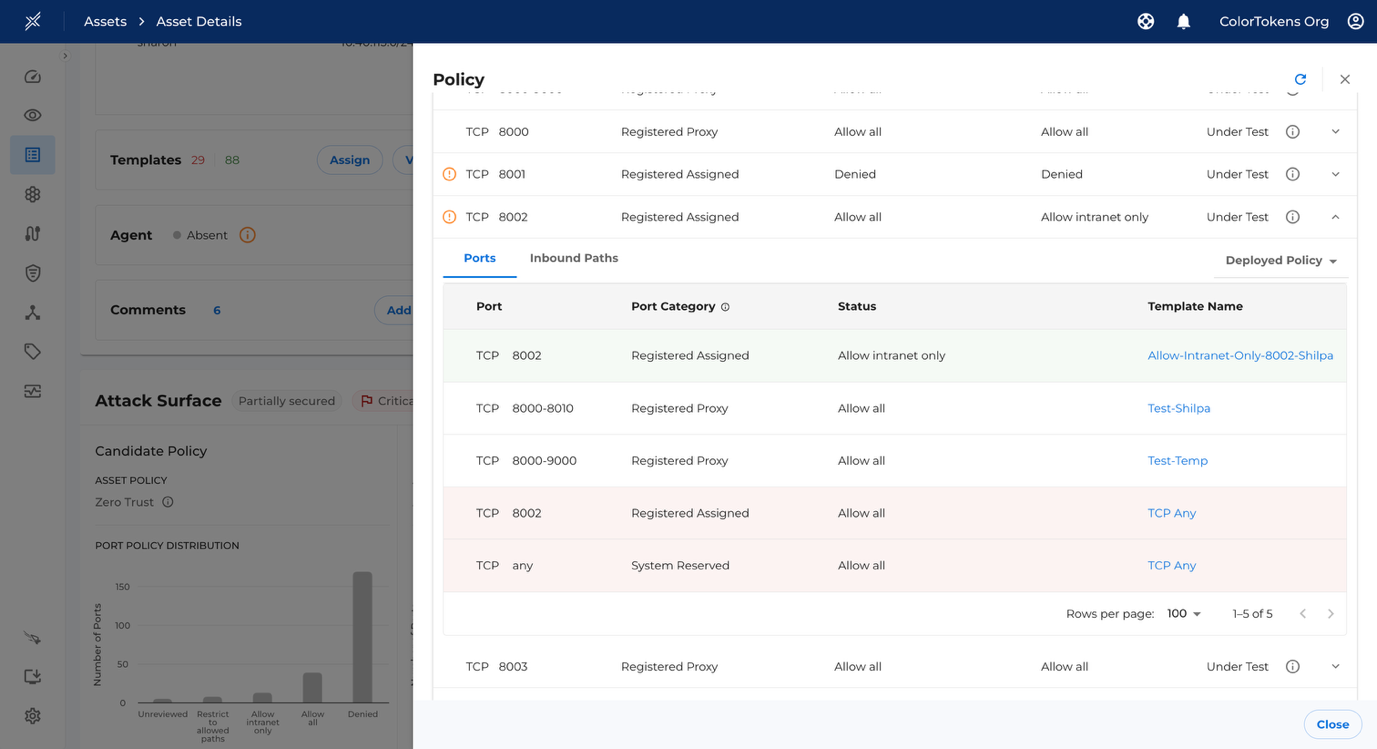
Future port policy status conflict
When multiple port policies are applied, conflicting future policy statuses may arise. In such cases, the final status is determined by the one with the highest priority. Check Priority Table for more details. Ports having conflicting future policy statuses are highlighted with a yellow icon in the port policy table.
Future Port Policy Changes
You may add or remove multiple policies without deploying them immediately. To view these changes, click on "View". Policies highlighted in red indicate removals, while those in green indicate additions.
Note: The overall status will only update after the deployment is completed.
Deployment launch points
You can trigger deployment for single or multiple asset from different launch points in the UI.
Single Asset
Once deployment is enabled and a deployment mode is selected from the "Deploy" option, the rest of the deployment flow follows the same steps as described in the Deployment section above.
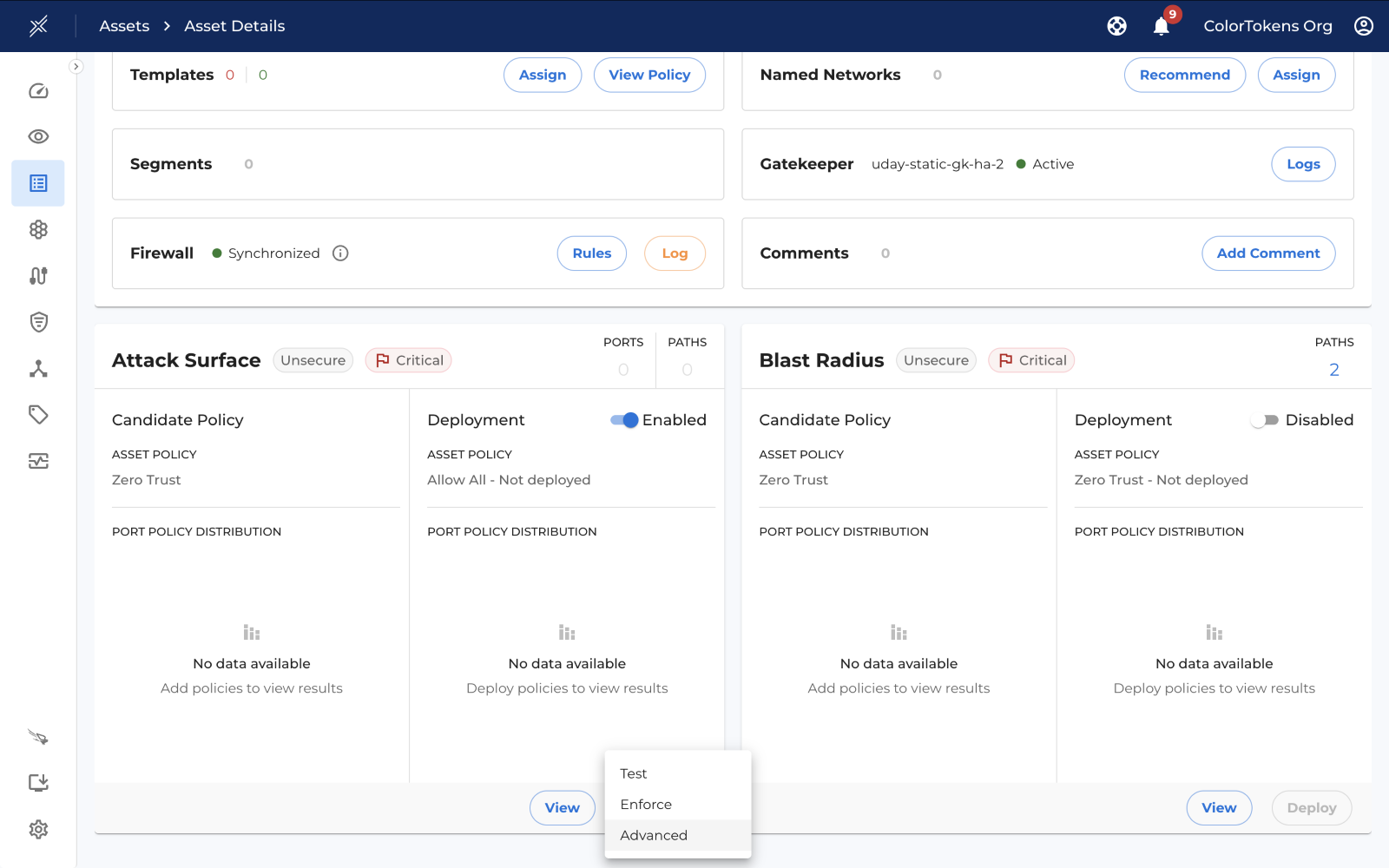
Rest of the deployment steps remains the same as mentioned here
Multi Assets
To deploy policies across multiple assets, select the desired assets from the Assets List page, as shown below.
Visualizer
After navigating to the Visualizer, click on any asset category and the button to deploy will be available in the drawer.
FAQ
Template removal flow
In micro deployment mode, removing a template moves affected ports to “Pending Test” (or directly to test if auto-deploy is enabled). The template remains attached until you test and enforce the ports, ensuring no disruption.