Exporting Events
Overview
Using SIEM Solutions with ColorTokens Zero Trust Security Platform - Xshield
The Xshield platform generates and logs events pertaining to configuration and operational state changes that may impact the enterprise security. These events also include network communication information. These events can be exported to Security Information and Event Management (SIEM) tools for further analaysis.
The Xshield platform writes these events to a customer provided object storage (preferably in Azure cloud and in the same region where the customer tenant is hosted) in Common Event Format (CEF).
Most of the modern SIEM tools such as Splunk, QRadar, ArcSight and Microsoft Sentinel can read events from cloud storage (such as Azure Object Store) in CEF and process them.
Data Control and Protection
You can control and protect the data feed using:
-
Event Filtering
Filter the type of security events collected in your SIEM by configuring Xshield to focus on events critical to your infrastructure. -
Data Retention
Security events data is stored in a cloud storage provider of your choice (preferably Azure or AWS Cloud). You can set a data retention policy based on your needs. -
Fetch Interval
Define how often calls are made to the Cloud API to fetch security event data. -
Format Standardization
Xshield pushes event data in the Common Event Format (CEF), ensuring compatibility with most SIEM tools.
How SIEM Integration Works
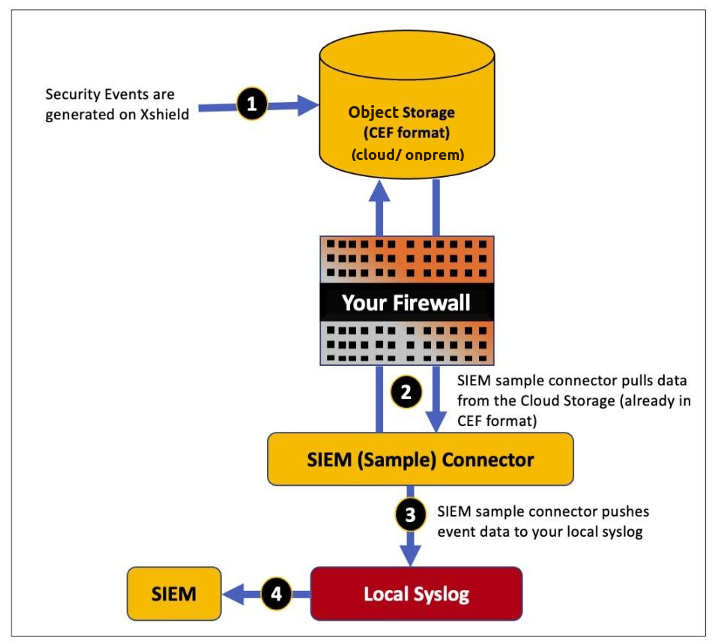
Customer provisions data storage on their Azure cloud (preferable) and provides write access to the storage to the Xshield Platform.
Xshield generates security events and pushes them in CEF format to this provisioned cloud storage. CEF is a standardized logging format introduced by ArcSight, Inc. and is compatible with many SIEM solutions.
If your SIEM tool cannot directly read events in CEF, then a connector can be used to pull the events from the cloud storage and then write it to the SIEM in a more traditional mechanism such as syslog. A sample connector is provided for used to pull security event data (already in CEF format) from cloud storage. The sample connector must be hosted by the customer in their premise and must be able to reach the provisioned cloud storage as well as the SIEM tool. More details is available in the installation guide.
If your SIEM tool can read CEF data directly from cloud storage, the sample connector is not required.
Xshield platform exports the below information
- Events: An event is a message reported by the platform (and not due to user operation) on the occurrence of something that requires customer attention or is a notification of success or failure of an operation that was performed by the user.
- Audits: An event generated on performing user operations are marked as audits.
- Alerts: An alert is configured by a user and is based on filters for specific events which triggers notifications to the user.
- Flow logs: A flow log records metadata about network connections, such as source/destination IPs, ports, protocols, timestamps, and traffic direction. It helps visualize communication patterns, detect anomalies, and support security investigations without capturing packet contents.
Data Upload Frequency
The Xshield platform uploads data to the configured object storage at the following intervals:
| Data Type | Upload Frequency |
|---|---|
| Alerts | Every 5 minutes |
| Audits | Every 15 minutes |
| Events | Every 15 minutes |
| Flow Logs | Every 15 minutes |
On-Premise SIEM Integration requirements
- An object store, in cloud or onprem, should be provided by the customer
- Ensure connectivity from the kubernetes cluster nodes to the customer provisioned object storage
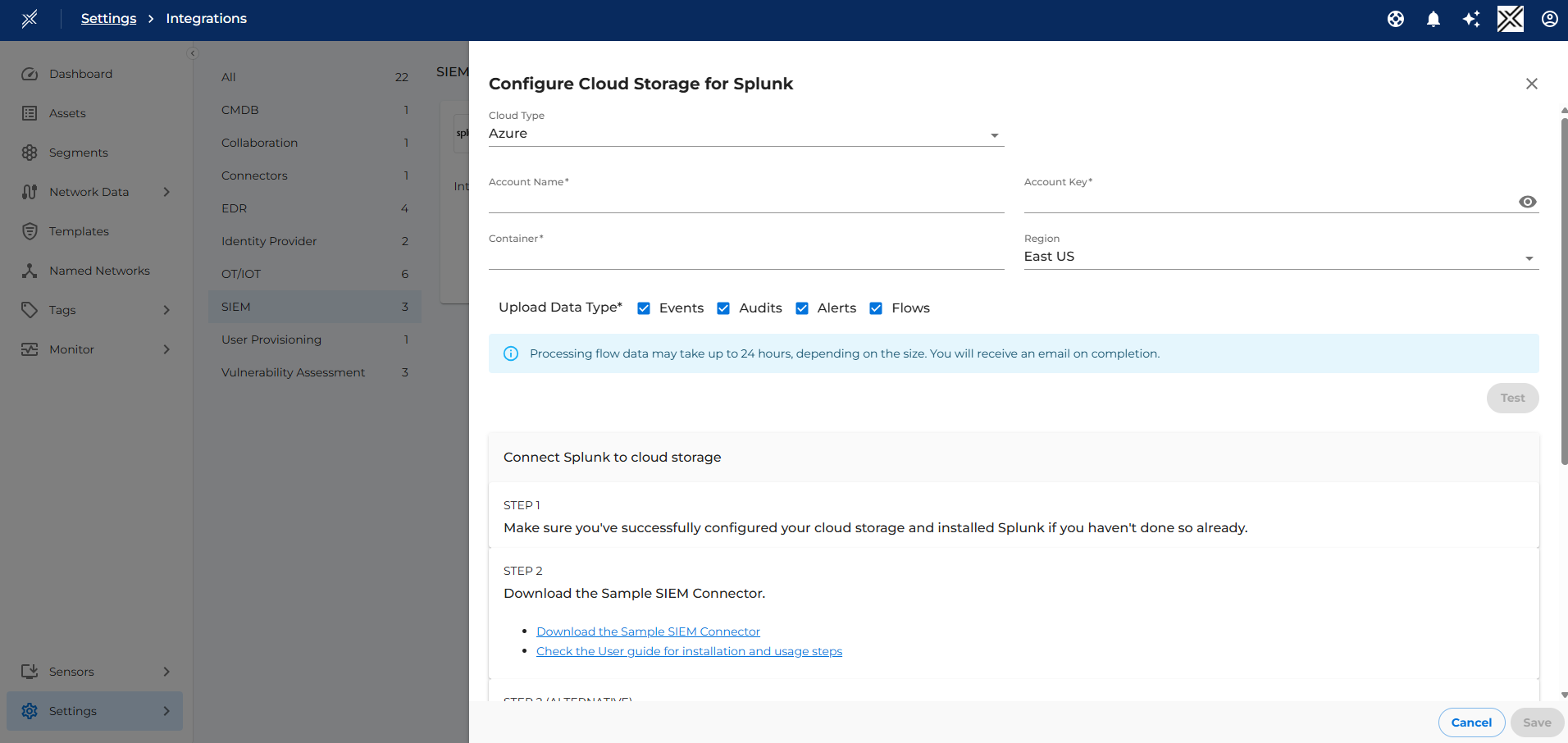
Set Up SIEM Integration
Step 1: Activate Your SIEM Integration
- Log in to the Xshield Platform.
- Navigate to the Integrations page in Xshield.
- Go to the SIEM category of integrations and activate the SIEM integration of your choice.
- Enter the cloud storage credentials where Xshield will write security event data.
- Select the security events you want to receive. The SIEM or the SIEM (sample) connector can fetch security events at intervals of up to 15 minutes.
- Click Test to verify the connectivity.
- Once the end-to-end integration is set up, click Save to complete the integration.
- A log entry will be generated under Monitoring > Tabs to confirm activation.
NOTE:
- The file pattern to be used on the SIEM tool is
^\d{4}_\d{2}_\d{2}T\d{2}_\d{2}_\d{2}\.\d{3}_(audits|alerts|events)$- For on-premise S3 compatible object stores, like garage, minio, rook-ceph etc., select Cloud Type as AWS and provide the customized S3 URI as bucket name (eg: s3://bucket-name?region=region&awssdk=v1&endpoint=https://local-object-store-url&disableSSL=boolean&s3ForcePathStyle=true) and credentials.
- Flow logs: Processing flow data may take up to 24 hours, depending on the size. Once the processing is completed, an email notification is sent to the user who enabled this option.
Step 2: Download the SIEM (Sample) Connector
Skip this step if the SIEM tool can read CEF data directly from object storage.
Download the sample CEF connector package using the link below:
Download SIEM Connector
Step 3: Install and Configure Your SIEM (Sample) Connector
Skip this step if the SIEM tool can read CEF data directly from object storage.
Install the SIEM sample connector behind your firewall. The SIEM sample connector retrieves security events (in CEF format) from cloud storage using Cloud API.
For detailed installation instructions, refer to the Sample CEF Connector.
If your SIEM tool supports reading CEF data directly from cloud storage, it can be configured within the SIEM tool itself. Configuration steps may vary depending on the SIEM tool, and referring to its official documentation is recommended.
Develop Your Own SIEM Connector
If your SIEM solution isn't supported by the sample connector, you can develop a custom connector. The API returns a list of chosen security events in CEF format, as described above.
Storage requirement for SIEM
Assumptions
The following assumptions are made for the storage requirement calculation:
- The calculation considers alerts, events and flow logs enabled
- The average log size from an asset per hour is 500KB
Storage Requirement
With the above assumption, the storage requirement for SIEM, per asset, is calculated as follows with the relevant retention period:
| Retention Period (days) | Storage Requirement per asset (MB) |
|---|---|
| 1 | 12 |
| 3 | 36 |
| 7 | 84 |
| 30 | 360 |