Gatekeeper Traffic Flow With /32 Netmask Configuration
This document demonstrates how traffic flows through a Gatekeeper appliance when end hosts are configured with a /32 subnet mask. The examples show a real-world deployment with network captures to illustrate traffic patterns.
Network Topology Overview
In this deployment scenario:
- Devices in VLAN 801 (IT) and VLAN 802 (OT) are managed by the Gatekeeper
- The Gatekeeper acts as a secondary gateway in these VLANs
- Host-specific reverse routes are configured on the distribution switch to ensure traffic from other networks passes through the Gatekeeper
Distribution Switch Configuration
The distribution switch has the following VLAN interfaces configured:
distSW# show running-config interface Vlan 801
interface vlan 801
name IT
ip address 172.16.81.1 255.255.255.0
!
distSW# show running-config interface Vlan 802
interface vlan 802
name OT
ip address 172.16.82.1 255.255.255.0
!
Original End Host Configuration
The Ubuntu server in VLAN 801 initially has its default gateway pointing to the existing distribution switch gateway (172.16.81.1):
# This is the network config written by 'subiquity'
network:
ethernets:
ens160:
addresses:
- 172.16.81.10/24
nameservers:
addresses: [ "8.8.8.8" ]
routes:
- to: default
via: 172.16.81.1
version: 2
The original routing table looks like this:
# ip route
default via 172.16.81.1 dev ens160 proto static
172.16.81.0/24 dev ens160 proto kernel scope link src 172.16.81.10
Gatekeeper Deployment
After deploying the Gatekeeper to manage VLAN 801 and VLAN 802, the following network interfaces are configured on the Gatekeeper:
- WAN Interface: 10.11.96.249 (with VIP 10.11.96.248)
- VLAN 801 Interface: 172.16.81.253 (with VIP 172.16.81.254)
- VLAN 802 Interface: 172.16.82.253 (with VIP 172.16.82.254)
The Gatekeeper interface configuration shows:
# ifconfig -a
...
vlan.801:vip: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.16.81.254 netmask 255.255.255.255 broadcast 0.0.0.0
ether 00:60:e0:97:ef:8f txqueuelen 1000 (Ethernet)
vlan.802:vip: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.16.82.254 netmask 255.255.255.255 broadcast 0.0.0.0
ether 00:60:e0:97:ef:8f txqueuelen 1000 (Ethernet)
Network Configuration Changes
1. Configure Host-Specific Reverse Route on Distribution Switch
To ensure traffic from other networks reaches the managed host via the Gatekeeper:
distSW# configure terminal
distSW(config)# ip route 172.16.81.10/32 10.11.96.248 metric 1
This static route directs all traffic destined for 172.16.81.10 to go through the Gatekeeper's WAN VIP (10.11.96.248).
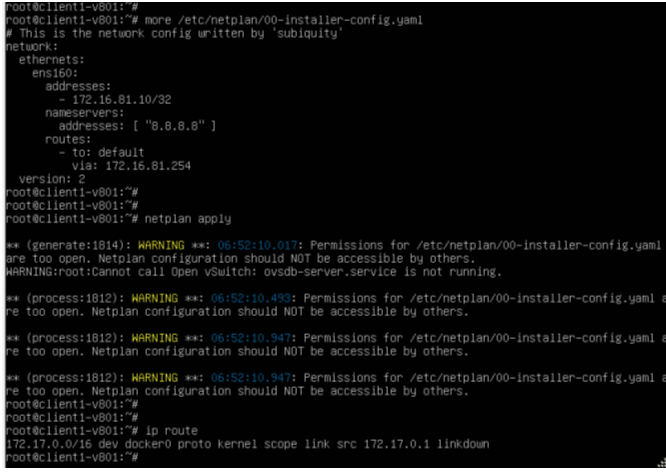
2. Modify End Host Network Configuration
The Ubuntu server's netplan configuration is updated to use a /32 subnet mask and set the Gatekeeper's VLAN VIP as its default gateway:
# This is the network config written by 'subiquity'
network:
ethernets:
ens160:
addresses:
- 172.16.81.10/32
nameservers:
addresses: [ "8.8.8.8" ]
routes:
- to: default
via: 172.16.81.254
version: 2
Traffic Flow Examples
The following examples demonstrate how traffic flows through the Gatekeeper after these configurations are applied:
Case 1: Traceroute from External Network
A traceroute from an external PC to the managed host (172.16.81.10) shows traffic passing through the Gatekeeper's WAN interface:
ashok.k@INCT-AshokK:~$ traceroute 172.16.81.10
traceroute to 172.16.81.10 (172.16.81.10), 30 hops max, 60 byte packets
1 * * *
2 172-11-172-1.lightspeed.frokca.sbcglobal.net (172.11.172.1) 7.283 ms 7.255 ms 7.230 ms
3 10.100.100.2 (10.100.100.2) 8.937 ms 8.909 ms 8.883 ms
4 10.11.96.249 (10.11.96.249) 7.076 ms 7.047 ms 7.019 ms
5 172.16.81.10 (172.16.81.10) 7.018 ms 6.993 ms 6.950 ms
This confirms that traffic from external networks is routed through the Gatekeeper (10.11.96.249) before reaching the end host.
Case 2: ICMP Traffic Between VLANs
When a host in VLAN 803 (172.16.83.13) pings the managed host in VLAN 801 (172.16.81.10):
ctuser@twamp-803:~$ ping 172.16.81.10
PING 172.16.81.10 (172.16.81.10) 56(84) bytes of data.
64 bytes from 172.16.81.10: icmp_seq=1 ttl=62 time=0.531 ms
64 bytes from 172.16.81.10: icmp_seq=2 ttl=62 time=0.692 ms
64 bytes from 172.16.81.10: icmp_seq=3 ttl=62 time=0.471 ms
Packet capture on the Gatekeeper's VLAN 801 interface confirms traffic inspection:
07:16:41.811610 IP 172.16.83.13 > 172.16.81.10: ICMP echo request, id 5, seq 6, length 64
07:16:41.811913 IP 172.16.81.10 > 172.16.83.13: ICMP echo reply, id 5, seq 6, length 64
07:16:42.835544 IP 172.16.83.13 > 172.16.81.10: ICMP echo request, id 5, seq 7, length 64
07:16:42.835783 IP 172.16.81.10 > 172.16.83.13: ICMP echo reply, id 5, seq 7, length 64
Case 3: TCP Traffic (SSH) Between VLANs
When establishing an SSH connection from VLAN 803 to the managed host in VLAN 801:
ctuser@twamp-803:~$ ssh ctuser@172.16.81.10
Packet capture on the Gatekeeper's VLAN 801 interface shows the TCP handshake and traffic inspection:
07:22:54.567723 IP 172.16.83.13.49324 > 172.16.81.10.ssh: Flags [S], seq 3300298553, win 64240, options [mss 1460,sackOK,TS val 2622396215 ecr 0,nop,wscale 7], length 0
07:22:54.568229 IP 172.16.81.10.ssh > 172.16.83.13.49324: Flags [S.], seq 624327838, ack 3300298554, win 65160, options [mss 1460,sackOK,TS val 660195098 ecr 2622396215,nop,wscale 7], length 0
07:22:54.568647 IP 172.16.83.13.49324 > 172.16.81.10.ssh: Flags [.], ack 1, win 502, options [nop,nop,TS val 2622396215 ecr 660195098], length 0
Case 4: UDP Traffic (SNMP) Between VLANs
When performing SNMP requests from VLAN 803 to the managed host in VLAN 801:
ctuser@twamp-803:~$ snmpget -v2c -c public 172.16.81.10 1.3.6.1.2.1.1.1.0
iso.3.6.1.2.1.1.1.0 = STRING: "Linux client1-v801 5.15.0-151-generic #161-Ubuntu SMP Tue Jul 22 14:25:40 UTC 2025 x86_64"
Packet capture on the Gatekeeper's VLAN 801 interface shows the UDP request and response:
08:08:57.049978 IP 172.16.83.13.45810 > 172.16.81.10.snmp: GetRequest(28) system.sysDescr.0
08:08:57.050542 IP 172.16.81.10.snmp > 172.16.83.13.45810: GetResponse(117) system.sysDescr.0="Linux client1-v801 5.15.0-151-generic #161-Ubuntu SMP Tue Jul 22 14:25:40 UTC 2025 x86_64"
Case 5: UDP Traffic (Syslog) Between VLANs
When sending syslog messages from VLAN 803 to the managed host in VLAN 801:
Packet capture on the Gatekeeper's VLAN 801 interface shows the syslog messages:
08:23:53.759788 IP 172.16.83.13.58684 > 172.16.81.10.syslog: SYSLOG authpriv.notice, length: 132
08:23:53.760393 IP 172.16.83.13.58684 > 172.16.81.10.syslog: SYSLOG authpriv.info, length: 112
08:23:53.791083 IP 172.16.83.13.38368 > 172.16.81.10.syslog: SYSLOG daemon.info, length: 76
Conclusion
This document demonstrates how the Gatekeeper appliance, when properly configured with /32 netmasks on end hosts and appropriate network routing, ensures that all traffic to and from protected hosts passes through the Gatekeeper for inspection and policy enforcement. The configuration creates a secure architecture where:
- End hosts in protected VLANs use the Gatekeeper as their default gateway
- The distribution switch routes traffic to these hosts through the Gatekeeper's WAN interface
- All traffic types (ICMP, TCP, UDP) are properly inspected by the Gatekeeper