Manual (Console-based)
Introduction
This document covers onboarding cloud segmentation and Xcloud compliance.
For Xcloud trust needs to be established to account: arn:aws:iam::723313884545:root
For Cloud segmentation trust needs to be established to account: 324037275567
This guide walks you through the manual (console-based) onboarding flow for connecting an AWS account to the Xshield Cloud Connector. You perform the steps directly in the AWS Console and the Xshield portal—no script is run in your environment.
Use this method when:
-
You prefer to deploy the CloudFormation stack yourself in the AWS Console for full control and auditability
-
You want to skip the template and create the IAM role and permissions yourself, step by step, in the AWS Console
-
Your change-management or compliance process requires manual, documented steps
-
You need to align with existing AWS governance (e.g. stack naming, parameter review)
Xcloud Compliance Requirements
For Xcloud compliance, the following additional privileges must be granted to the cross-account role:
access-analyzer:ListAnalyzers,
autoscaling:DescribeAutoScalingGroups,
cloudformation:ListStacks,
cloudtrail:DescribeTrails,
cloudtrail:GetTrailStatus,
cloudtrail:GetEventSelectors,
cloudwatch:DescribeAlarms,
config:DescribeConfigurationRecorderStatus,
config:DescribeConfigurationRecorders,
ec2:DescribeAddresses,
ec2:DescribeFlowLogs,
ec2:DescribeImages,
ec2:DescribeInstances,
ec2:DescribeNetworkAcls,
ec2:DescribeNetworkInterfaces,
ec2:DescribeRegions,
ec2:DescribeSecurityGroups,
ec2:DescribeSnapshots,
ec2:DescribeSnapshotAttribute,
ec2:DescribeVolumes,
ec2:DescribeVpcs,
ec2:DescribeSubnets,
ec2:DescribeRouteTables,
ecr:BatchGetImage,
ecr:DescribeRepositories,
ecr:DescribeImages,
ecr:GetAuthorizationToken,
ecr:GetDownloadUrlForLayer,
ecr:ListTagsForResource,
eks:DescribeCluster,
eks:ListClusters,
elasticloadbalancing:DescribeLoadBalancers,
elasticloadbalancing:DescribeListeners,
elasticloadbalancing:DescribeRules,
elasticloadbalancing:DescribeTargetGroups,
elasticloadbalancing:DescribeTargetHealth,
iam:GetAccountSummary,
iam:GetRole,
iam:GetCredentialReport,
iam:GetPolicyVersion,
iam:GetAccountPasswordPolicy,
iam:GenerateCredentialReport,
iam:ListAttachedUserPolicies,
iam:ListEntitiesForPolicy,
iam:ListPolicies,
iam:ListServerCertificates,
iam:ListUsers,
iam:ListUserPolicies,
iam:ListVirtualMFADevices,
kms:DescribeKey,
kms:GetKeyRotationStatus,
kms:ListKeys,
logs:DescribeMetricFilters,
rds:DescribeDBInstances,
rds:DescribeSourceRegions,
s3:GetAccountPublicAccessBlock,
s3:GetBucketAcl,
s3:GetBucketLocation,
s3:GetBucketLogging,
s3:GetBucketPolicy,
s3:GetBucketPolicyStatus,
s3:GetBucketVersioning,
s3:GetBucketPublicAccessBlock,
s3:GetEncryptionConfiguration,
s3:GetReplicationConfiguration,
s3:ListAllMyBuckets,
s3:ListBucket,
sns:ListSubscriptionsByTopic,
sns:ListSubscriptions,
sts:GetCallerIdentity
Who Does What
Manual (console-based) onboarding is done per AWS account by someone who has access to both AWS and Xshield:
| Who | What | Why |
|---|---|---|
| AWS account admin (or IAM principal with the required CloudFormation and IAM permissions) | Either deploy the CloudFormation stack from Xshield or create the cross-account IAM role and attach policies manually in the AWS Console (see Choose your path below) | The cross-account role and permissions allow Xshield to discover and monitor resources in your account; only someone with sufficient AWS permissions can create them. |
| Xshield user (with access to Cloud Connector) | Enter Account Name and Account ID in the Xshield portal, then Verify and Connect | Xshield uses this to associate the account with your tenant and complete the connection; verification confirms that ColorTokens can assume the cross-account role in your account (same for both paths). |
The same person can do both if they have access to AWS and Xshield; otherwise, the AWS admin completes the AWS steps and shares the Account ID, and a Xshield user completes the connection in the portal.
Prerequisites
Before you begin, ensure you have:
-
Active AWS account with the permissions required for the option you choose (see Choose your path below)
-
AWS Account ID for the account you want to onboard (find it in the AWS Console—account dropdown or Support center)
-
ColorTokens AWS account ID: use
xxxxxxxxxxxxas the ColorTokens AWS account ID. -
Active Xshield account with access to the management portal
Choose your path
You can complete the AWS setup in one of two ways:
-
Path A (CloudFormation template): Use the template from Xshield and create the stack in the AWS Console. The stack creates the cross-account IAM role and policies for you.
-
Path B (manual IAM): Skip the template and create the cross-account IAM role and attach policies yourself, step by step, in the AWS Console.
Both paths result in a cross-account IAM role that Xshield can assume to discover and monitor your AWS resources. After completing either path, continue with Step 3: Enter Account Details. For the full list of IAM permissions the cross-account role must have (e.g. for Terraform or other IaC), see Reference: IAM permissions for the cross-account role at the end of this guide.
Required permissions for the AWS admin
The IAM principal (user or role) that performs the AWS steps must have the following permissions. Use the row that matches the path you chose above.
| Path | Required permissions | Why |
|---|---|---|
| Path A (CloudFormation template) | CloudFormation: CreateStack, DescribeStacks, DescribeStackEvents, DescribeStackResource, GetTemplateSummaryIAM: CreateRole, PutRolePolicy, AttachRolePolicy, GetRole, PassRole | CloudFormation creates the stack and the stack creates IAM resources (role with inline policies, trust policy) using your credentials; you need CloudFormation write and IAM permissions to create the role and policies. |
| Path B (manual IAM) | IAM: CreateRole, PutRolePolicy, AttachRolePolicy, GetRole, ListAttachedRolePolicies, ListRolePolicies, PassRoleIf attaching AWS managed policies: GetPolicy (for customer-managed) or use policies that your account can already access | You create the role and attach inline or managed policies directly in IAM; no CloudFormation actions are needed. |
The PowerUserAccess (or AdministratorAccess) AWS managed policy includes the permissions needed for Path A. For Path B, IAMFullAccess is sufficient for creating the role and attaching policies. For least privilege, create a custom policy that grants only the actions in the table above (and the specific resources your organization allows).
Path A: Using the CloudFormation template
Overview: What happens during and after stack creation
Before you run the steps, here is what the template does.
During stack creation:
-
StackCreationRegistration (custom resource) runs first. It notifies ColorTokens that stack creation has started and sends the NotificationTopicArn you provide and the template version. ColorTokens can prepare for onboarding and optionally send status to that SNS topic.
-
ColorTokensCrossAccountAccessRole is created in your account. This IAM role has a trust policy that allows only the ColorTokens AWS account to assume it, and an inline policy with read-only access to the services needed for discovery and monitoring (EC2, S3, RDS, Lambda, X-Ray, etc.).
-
IamRoleRegistration (custom resource) runs after the role exists. It sends the new role ARN to ColorTokens so they can register it and associate it with your account. ColorTokens may also publish a notification to the NotificationTopicArn you provided (e.g. “role ready”).
After stack creation:
- The stack and the cross-account role exist in your account. ColorTokens has the role ARN and can assume it after you complete Step 3 (Enter Account Details → Verify → Connect) in the Xshield portal. Verify checks whether ColorTokens can assume the role (same as Path B); Connect starts syncing your AWS resources.
Step A.1: Get the CloudFormation Template
The template defines the cross-account IAM role and policies that allow Xshield to discover and monitor your AWS resources. Deploying it via CloudFormation gives you a single, auditable stack. You can review the template before creating the stack and manage it like any other stack in your account.
-
In the Xshield portal, go to Cloud Connectors → AWS → Manual onboarding.
-
Get the CloudFormation template from the Xshield portal or from the template below. Copy the full template and save it as a
.yamlfile on your computer for the next step.
CloudFormation template (copy and save as a .yaml file):
AWSTemplateFormatVersion: "2010-09-09"
Description: "ColorTokens Stack for Cloud Security (Read-Only Mode with Storage Access)"
Mappings:
TemplateDetails:
TemplateVersion:
Ver: "1.0.0-readonly-storage"
Metadata:
AWS::CloudFormation::Interface:
ParameterGroups:
- Label:
default: "Deployment Configuration"
Parameters:
- StackName
- IAMRoleName
- ColorTokensAccountID
- ColorTokensCloudSecurityServiceRole
- NotificationTopicArn
ParameterLabels:
StackName:
default: "Stack Name"
IAMRoleName:
default: "IAM Role Name"
ColorTokensAccountID:
default: "ColorTokens Account ID"
ColorTokensCloudSecurityServiceRole:
default: "ColorTokens Service Role Name"
NotificationTopicArn:
default: "Notification Topic ARN"
Parameters:
StackName:
Description: "CloudFormation stack for ColorTokens Cloud Security Integration."
Type: String
Default: "ColorTokensStackForCloudSecurity"
MinLength: 1
ConstraintDescription: "StackName cannot be empty."
IAMRoleName:
Description: "IAM role created in this account to enable cross-account access for ColorTokens."
Type: String
Default: "ColorTokensCrossAccountAccessRole"
MinLength: 1
ConstraintDescription: "IAM Role Name cannot be empty."
ColorTokensAccountID:
Description: "ColorTokens AWS Account ID for Cloud Security."
Type: String
Default: XXXXXXXXXXXX
AllowedValues: [XXXXXXXXXXXX]
ColorTokensCloudSecurityServiceRole:
Description: "IAM Role in ColorTokens Account that will assume role in this account for extracting security related information."
Type: String
Default: "ColorTokensCloudSecurityServiceRole"
MinLength: 1
ConstraintDescription: "ColorTokensRoleName cannot be empty."
NotificationTopicArn:
Description: "SNS Topic ARN in ColorTokens account for onboarding notifications."
Type: String
MinLength: 1
ConstraintDescription: "NotificationTopicArn cannot be empty."
Resources:
StackCreationRegistration:
Type: "Custom::StackCreationRegistration"
DeletionPolicy: Retain
Properties:
ServiceToken: !Sub "arn:aws:sns:${AWS::Region}:XXXXXXXXXXXX:cloudformation-custom-resource-topic"
NotificationTopicArn: !Ref NotificationTopicArn
TemplateVersion: !FindInMap [TemplateDetails, TemplateVersion, Ver]
ColorTokensCrossAccountAccessRole:
Type: "AWS::IAM::Role"
DependsOn:
- StackCreationRegistration
Properties:
RoleName: !Ref IAMRoleName
AssumeRolePolicyDocument:
Version: "2012-10-17"
Statement:
- Effect: "Allow"
Principal:
AWS: !Sub "arn:aws:iam::XXXXXXXXXXXX:role/ColorTokensCloudSecurityServiceRole"
Action: "sts:AssumeRole"
Policies:
- PolicyName: "ColorTokensAccessPolicy"
PolicyDocument:
Version: "2012-10-17"
Statement:
- Action:
- "s3:ListAllMyBuckets"
- "s3:GetBucketLocation"
- "s3:GetBucketAcl"
- "s3:GetBucketPolicy"
- "s3:GetBucketVersioning"
- "s3:GetBucketPublicAccessBlock"
- "s3:GetBucketNotification"
- "s3:GetBucketTagging"
- "s3:ListBucket"
- "s3:GetObject"
Resource: "*"
Effect: "Allow"
Sid: "ColorTokensS3FullReadAccess"
- Action:
- "lambda:ListFunctions"
- "lambda:GetFunction"
- "lambda:GetFunctionConfiguration"
- "lambda:GetPolicy"
- "lambda:ListTags"
- "lambda:ListEventSourceMappings"
Resource: "*"
Effect: "Allow"
Sid: "ColorTokensLambdaReadAccess"
- Action:
- "dynamodb:ListTables"
- "dynamodb:DescribeTable"
- "dynamodb:ListTagsOfResource"
Resource: "*"
Effect: "Allow"
Sid: "ColorTokensDynamoReadAccess"
- Action:
- "ec2:DescribeInstances"
- "ec2:DescribeTags"
- "ec2:DescribeSecurityGroups"
- "ec2:DescribeNetworkAcls"
- "ec2:DescribeSubnets"
- "ec2:DescribeVpcs"
- "ec2:DescribeVolumes"
- "ec2:DescribeSnapshots"
- "ec2:DescribeAddresses"
- "ec2:DescribeNetworkInterfaces"
- "ec2:DescribeRegions"
- "ec2:DescribeAvailabilityZones"
- "ec2:DescribeFlowLogs"
Resource: "*"
Effect: "Allow"
Sid: "ColorTokensEC2ReadAccess"
- Action:
- "rds:DescribeDBInstances"
- "rds:DescribeDBClusters"
- "rds:DescribeDBClusterEndpoints"
- "rds:DescribeDBSecurityGroups"
- "rds:DescribeDBSubnetGroups"
- "rds:DescribeDBParameterGroups"
- "rds:ListTagsForResource"
Resource: "*"
Effect: "Allow"
Sid: "ColorTokensRDSReadAccess"
- Action:
- "ec2:DescribeNatGateways"
- "ec2:DescribeInternetGateways"
- "ec2:DescribeTransitGateways"
- "ec2:DescribeVpcEndpoints"
- "ec2:DescribeVpcEndpointServices"
Resource: "*"
Effect: "Allow"
Sid: "ColorTokensNetworkResourceReadAccess"
- Action:
- "elasticloadbalancing:DescribeLoadBalancers"
- "elasticloadbalancing:DescribeTags"
- "elasticloadbalancing:DescribeTargetGroups"
- "elasticloadbalancing:DescribeListeners"
- "elasticloadbalancing:DescribeTargetHealth"
Effect: "Allow"
Resource: "*"
Sid: "ColorTokensELBReadAccess"
- Action:
- "apigateway:GET"
Effect: "Allow"
Resource: "*"
Sid: "ColorTokensAPIGatewayReadAccess"
- Action:
- "ec2:DescribeManagedPrefixLists"
- "ec2:GetManagedPrefixListEntries"
Effect: "Allow"
Resource: "*"
Sid: "ColorTokensPrefixListReadAccess"
- Action:
- "xray:GetTraceSummaries"
- "xray:BatchGetTraces"
Effect: "Allow"
Resource: "*"
Sid: "ColorTokensXRayReadAccess"
IamRoleRegistration:
Type: "Custom::IamRoleRegistration"
DeletionPolicy: Retain
DependsOn:
- ColorTokensCrossAccountAccessRole
Properties:
ServiceToken: !Sub "arn:aws:sns:${AWS::Region}:XXXXXXXXXXXX:cloudformation-custom-resource-topic"
NotificationTopicArn: !Ref NotificationTopicArn
RoleArn: !GetAtt ColorTokensCrossAccountAccessRole.Arn
TemplateVersion: !FindInMap [TemplateDetails, TemplateVersion, Ver]
Outputs:
IAMRoleARN:
Description: "ARN of the created IAM Role for ColorTokens cross-account access."
Value: !GetAtt ColorTokensCrossAccountAccessRole.Arn
Export:
Name: "ColorTokensCrossAccountAccessRoleARN"
StackName:
Description: "Name of the CloudFormation stack"
Value: !Ref StackName
NotificationTopicArn:
Description: "SNS Topic ARN used for notifications"
Value: !Ref NotificationTopicArn
TemplateVersion:
Description: "Version of the CloudFormation template"
Value: !FindInMap [TemplateDetails, TemplateVersion, Ver]
AccessMode:
Description: "Access mode - Read-Only with Storage Access"
Value: "readonly-storage"
Step A.2: Create AWS CloudFormation Stack
Why create the stack in the AWS Console: CloudFormation creates the IAM role and policies in your account. Creating the stack yourself in the Console lets you control when and where it runs, review each step, and satisfy change-management or compliance requirements. Use the stack name and parameters (including NotificationTopicArn) from the Xshield portal so the role trusts the correct ColorTokens account and notifications work.
-
In the AWS Console, search for and open CloudFormation.
-
Click Create stack, then select With new resources (standard).
-
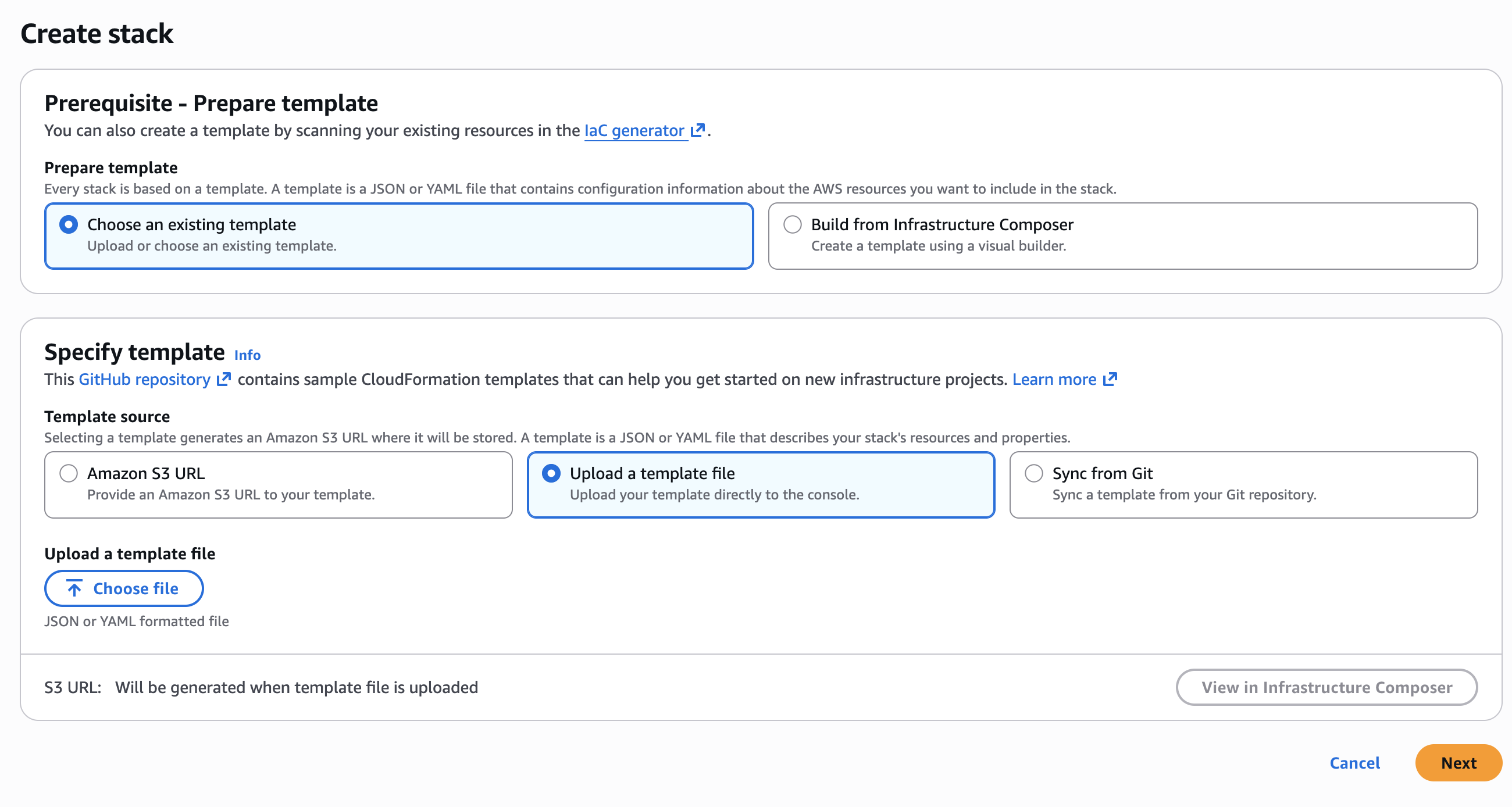
Upload the template file.
-
Under Prepare template, select Choose an existing template.
-
Under Specify template, select Upload a template file.
-
Click Choose file and select the YAML file you saved in Step A.1.
-
Click Next.
-
-
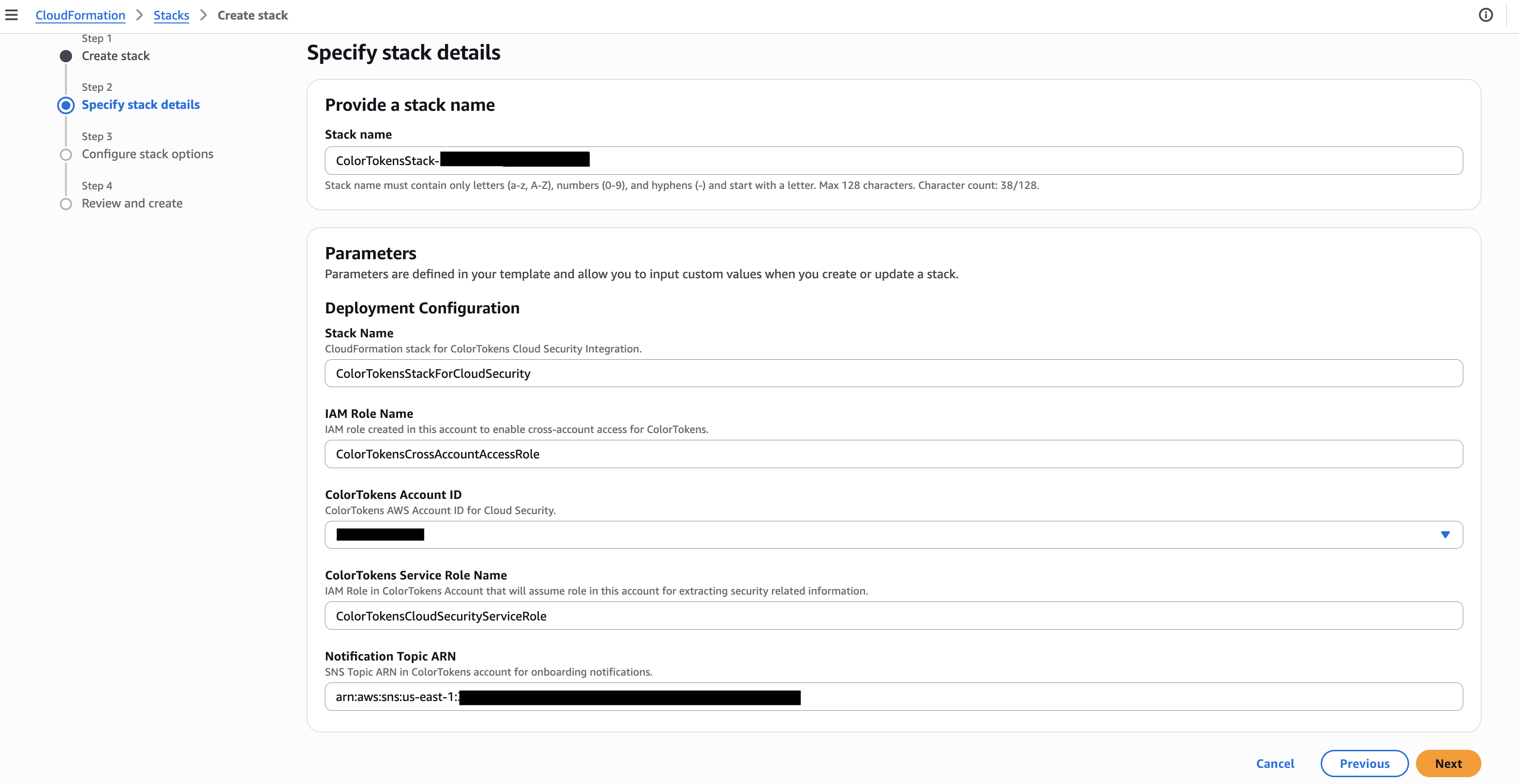
Specify stack name and parameters.
-
For Stack name, use the name shown in the Xshield portal (e.g. in the Manual onboarding flow).
-
In Parameters, enter the values prompted by the template:
-
StackName:
ColorTokensStackForCloudSecurity(or your naming standard) -
IAMRoleName:
ColorTokensCrossAccountAccessRole(or a custom role name) -
ColorTokensAccountID: use the value from the Xshield portal (the template allows only the correct account ID)
-
ColorTokensCloudSecurityServiceRole:
ColorTokensCloudSecurityServiceRole(keep the default unless instructed otherwise) -
NotificationTopicArn: paste the SNS topic ARN from the Xshield portal (e.g.
arn:aws:sns:us-east-1:XXXXXXXXXXXX:ccdev01-customer-onboarding-notifications)
-
-
Click Next.
-
-
Configure stack options.
-
(Optional) Add tags.
-
Check the box acknowledging that CloudFormation will create IAM resources.
-
Click Next.
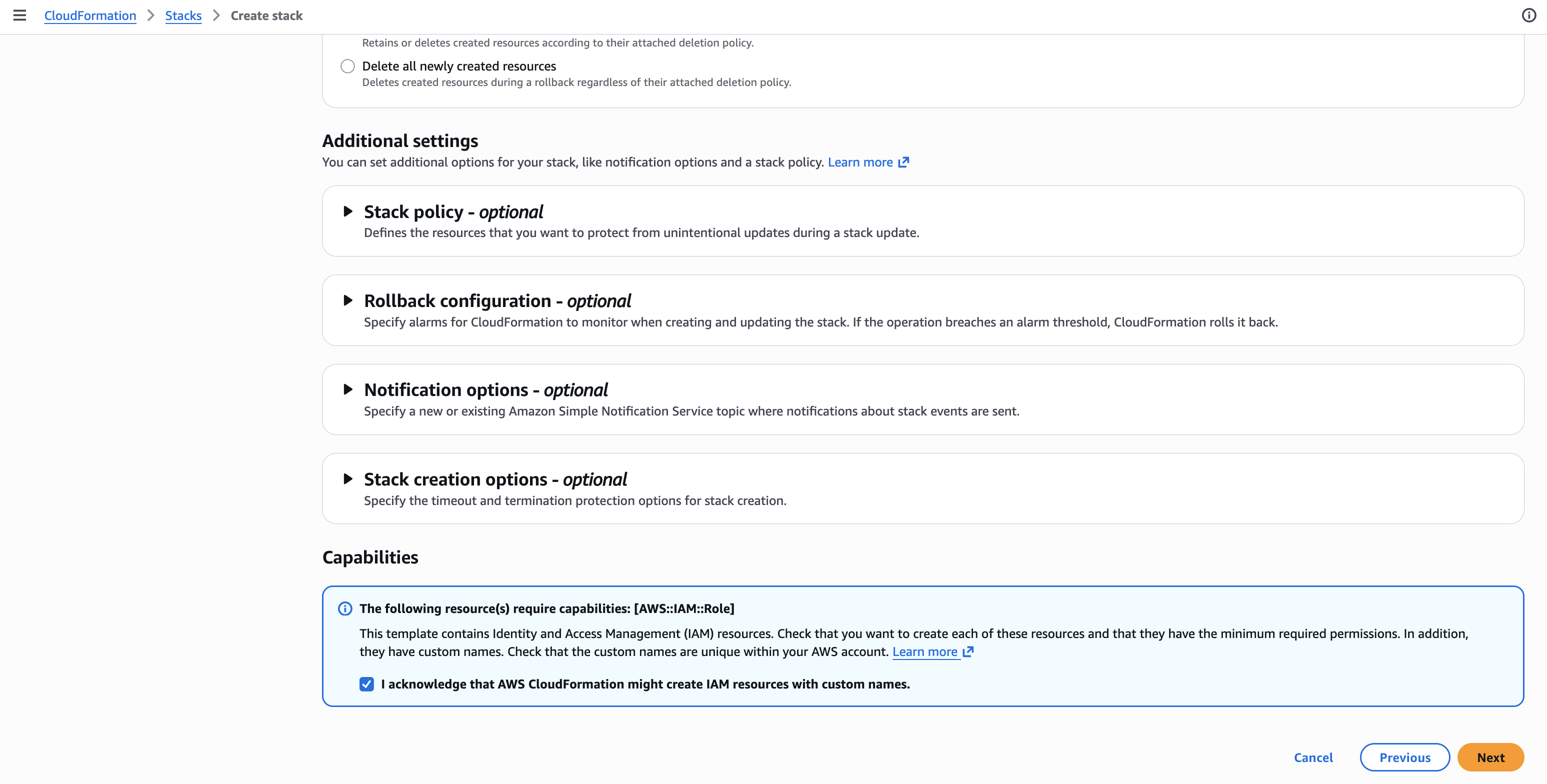
-
-
Review the stack details, then click Submit.
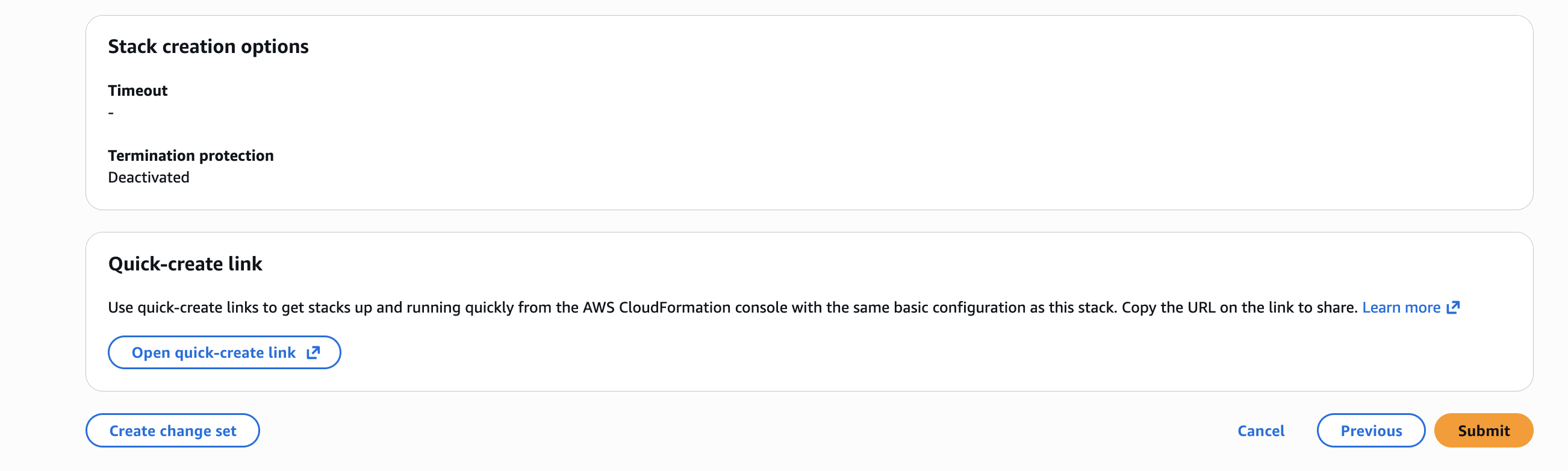
After the stack is created successfully, go to Step 3: Enter Account Details.
Path B: Create the IAM role and permissions manually
Use this path when you want to skip the CloudFormation template and create the cross-account IAM role and policies yourself in the AWS Console. The role and permissions must match what Xshield expects so that verification and connection in the portal succeed.
Overview: What happens with Path B (no CloudFormation)
With Path B there is no CloudFormation stack in your account:
-
No automatic registration: ColorTokens does not receive a stack-creation or role-registration signal. You do not provide an SNS topic ARN; notifications are only used with the CloudFormation path (Path A).
-
No pre-registered role: Xshield does not know your role ARN until you complete Step 3: Enter Account Details in the portal. There you enter your Account ID and Account Name, then click Verify. Verification is the same for both paths: ColorTokens checks whether it can assume the cross-account role in that account (for Path B, it finds the role by name, e.g.
ColorTokensCrossAccountAccessRole). No CloudFormation stack is required for verification. -
Manual confirmation in the portal: After Verify succeeds, you click Connect. Xshield then associates your account with your tenant and starts syncing resources by assuming the role you created.
So the flow is: create the role and attach policies in AWS → go to the Xshield portal → Enter Account Details → Verify → Connect.
Step B.1: Create the cross-account IAM role
-
In the AWS Console, go to IAM → Roles → Create role.
-
For Trusted entity type, choose Custom trust policy.
-
In Custom trust policy, paste the following. This allows only the ColorTokens AWS account to assume the role (same as in the CloudFormation template):
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::XXXXXXXXXXXX:role/ColorTokensCloudSecurityServiceRole"
},
"Action": "sts:AssumeRole"
}
]
} -
Click Next.
-
Do not attach any policies yet; click Next again, then set the Role name to
ColorTokensCrossAccountAccessRole(or the role name shown in the Xshield portal for manual setup). Click Create role.
Xshield assumes this role from the ColorTokens AWS account (XXXXXXXXXXXX, role ColorTokensCloudSecurityServiceRole). The trust policy must allow that principal. The role name is used by Xshield to find and assume the role when you Verify and Connect; use the name above or the one indicated in the portal, or you may need to configure a custom name (if supported) or contact support.
Step B.2: Attach the required permissions policy
-
Open the role you created in Step B.1 (ColorTokensCrossAccountAccessRole).
-
On the Permissions tab, click Add permissions → Create inline policy.
-
Open the JSON tab and replace the default policy with the permissions Xshield needs for discovery and monitoring. The policy below matches the CloudFormation template (read-only access to S3, Lambda, DynamoDB, EC2, RDS, ELB, API Gateway, and X-Ray). Copy and paste it, then click Next.
If you need to grant or revoke access to specific S3 buckets after onboarding, see Storage Access (Manual).
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "ColorTokensS3FullReadAccess",
"Effect": "Allow",
"Action": [
"s3:ListAllMyBuckets",
"s3:GetBucketLocation",
"s3:GetBucketAcl",
"s3:GetBucketPolicy",
"s3:GetBucketVersioning",
"s3:GetBucketPublicAccessBlock",
"s3:GetBucketNotification",
"s3:GetBucketTagging",
"s3:ListBucket",
],
"Resource": "*"
},
{
"Sid": "ColorTokensLambdaReadAccess",
"Effect": "Allow",
"Action": [
"lambda:ListFunctions",
"lambda:GetFunction",
"lambda:GetFunctionConfiguration",
"lambda:GetPolicy",
"lambda:ListTags",
"lambda:ListEventSourceMappings"
],
"Resource": "*"
},
{
"Sid": "ColorTokensDynamoReadAccess",
"Effect": "Allow",
"Action": [
"dynamodb:ListTables",
"dynamodb:DescribeTable",
"dynamodb:ListTagsOfResource"
],
"Resource": "*"
},
{
"Sid": "ColorTokensEC2ReadAccess",
"Effect": "Allow",
"Action": [
"ec2:DescribeInstances",
"ec2:DescribeTags",
"ec2:DescribeSecurityGroups",
"ec2:DescribeNetworkAcls",
"ec2:DescribeSubnets",
"ec2:DescribeVpcs",
"ec2:DescribeVolumes",
"ec2:DescribeSnapshots",
"ec2:DescribeAddresses",
"ec2:DescribeNetworkInterfaces",
"ec2:DescribeRegions",
"ec2:DescribeAvailabilityZones",
"ec2:DescribeFlowLogs"
],
"Resource": "*"
},
{
"Sid": "ColorTokensRDSReadAccess",
"Effect": "Allow",
"Action": [
"rds:DescribeDBInstances",
"rds:DescribeDBClusters",
"rds:DescribeDBClusterEndpoints",
"rds:DescribeDBSecurityGroups",
"rds:DescribeDBSubnetGroups",
"rds:DescribeDBParameterGroups",
"rds:ListTagsForResource"
],
"Resource": "*"
},
{
"Sid": "ColorTokensNetworkResourceReadAccess",
"Effect": "Allow",
"Action": [
"ec2:DescribeNatGateways",
"ec2:DescribeInternetGateways",
"ec2:DescribeTransitGateways",
"ec2:DescribeVpcEndpoints",
"ec2:DescribeVpcEndpointServices"
],
"Resource": "*"
},
{
"Sid": "ColorTokensELBReadAccess",
"Effect": "Allow",
"Action": [
"elasticloadbalancing:DescribeLoadBalancers",
"elasticloadbalancing:DescribeTags",
"elasticloadbalancing:DescribeTargetGroups",
"elasticloadbalancing:DescribeListeners",
"elasticloadbalancing:DescribeTargetHealth"
],
"Resource": "*"
},
{
"Sid": "ColorTokensAPIGatewayReadAccess",
"Effect": "Allow",
"Action": [
"apigateway:GET"
],
"Resource": "*"
},
{
"Sid": "ColorTokensPrefixListReadAccess",
"Effect": "Allow",
"Action": [
"ec2:DescribeManagedPrefixLists",
"ec2:GetManagedPrefixListEntries"
],
"Resource": "*"
},
{
"Sid": "ColorTokensXRayReadAccess",
"Effect": "Allow",
"Action": [
"xray:GetTraceSummaries",
"xray:BatchGetTraces"
],
"Resource": "*"
}
]
} -
Name the policy (e.g. ColorTokensAccessPolicy) and click Create policy.
If the CloudFormation template in the Xshield portal (Cloud Connectors → AWS → Manual → View CloudFormation Template) is updated with new actions or services, replicate those changes in your inline policy so discovery and monitoring stay complete.
After the role exists with this trust policy and permissions, go to Step 3: Enter Account Details below. Enter your Account ID and Account Name, click Verify (Xshield will confirm the role in your account), then click Connect to complete onboarding.
Step 3: Enter Account Details
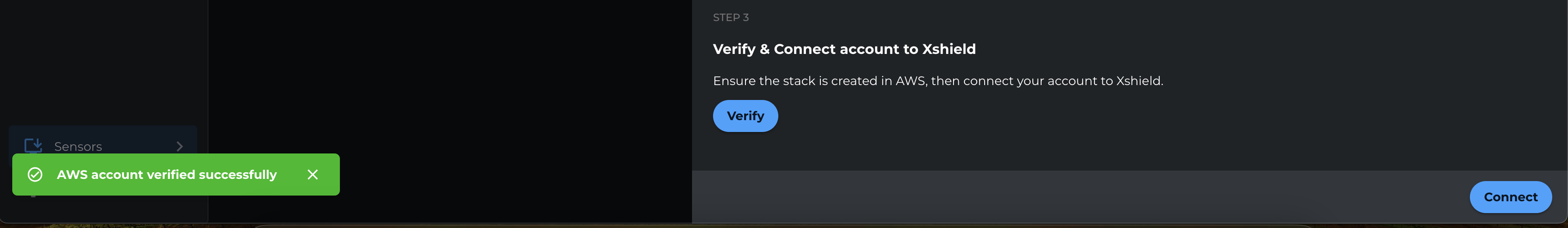
Why we ask for Account Name and Account ID: Xshield uses the Account ID to identify the AWS account and to verify the connection. For both Path A and Path B, Verify checks whether ColorTokens can assume the cross-account role in that account (role-assumption check). The Account Name is a label you choose for this account in the Xshield portal. Once Verify succeeds, Connect completes the onboarding and starts syncing resources.
-
Enter your Account Name and Account ID, then click Verify.
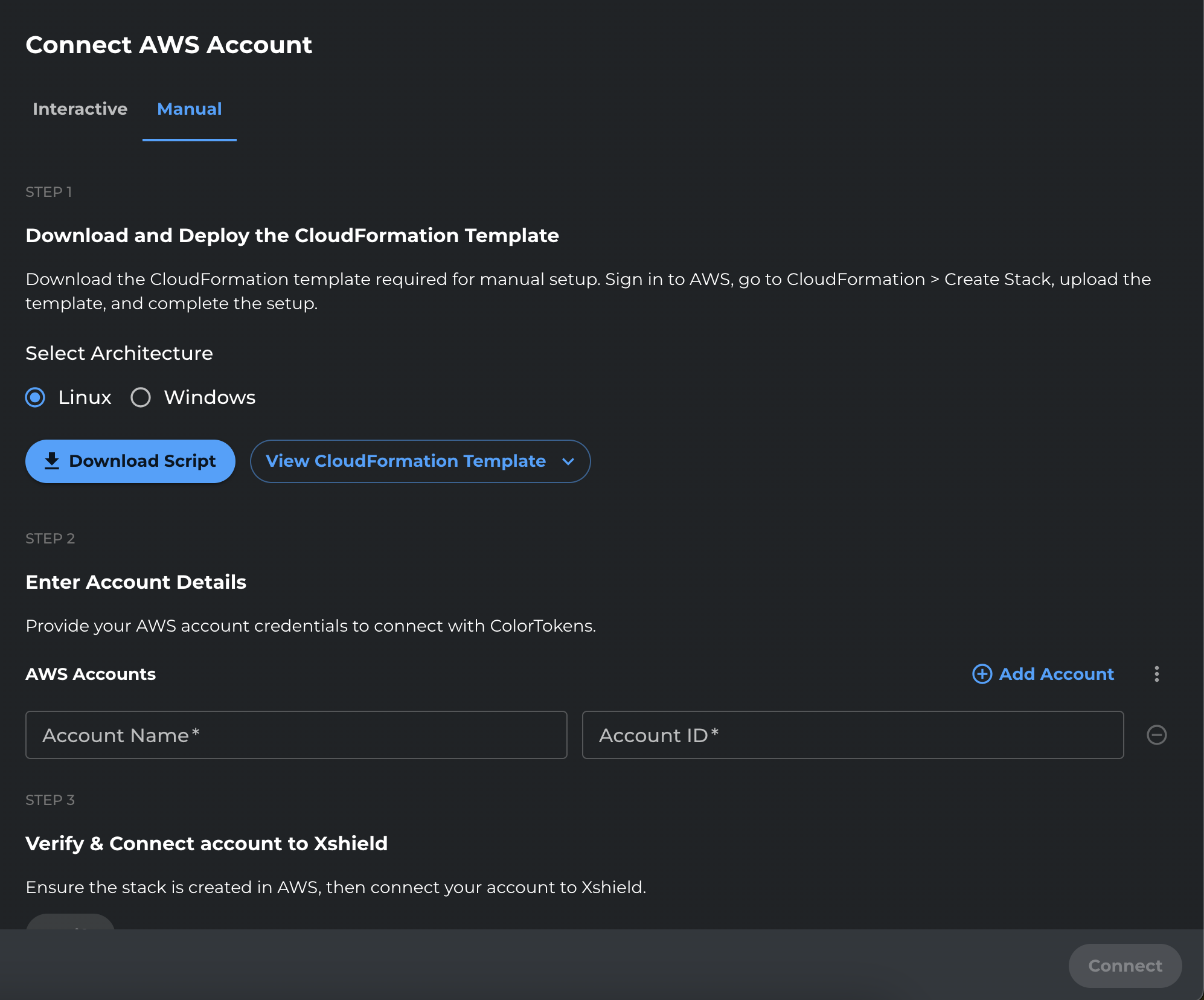
-
Click Verify.
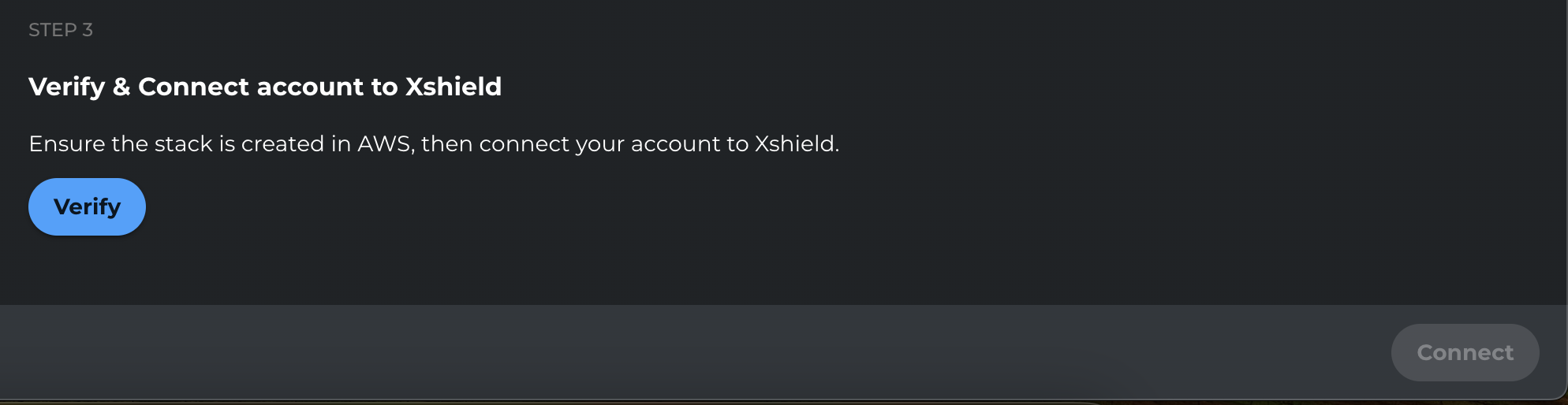
-
After verification completes, click Connect.
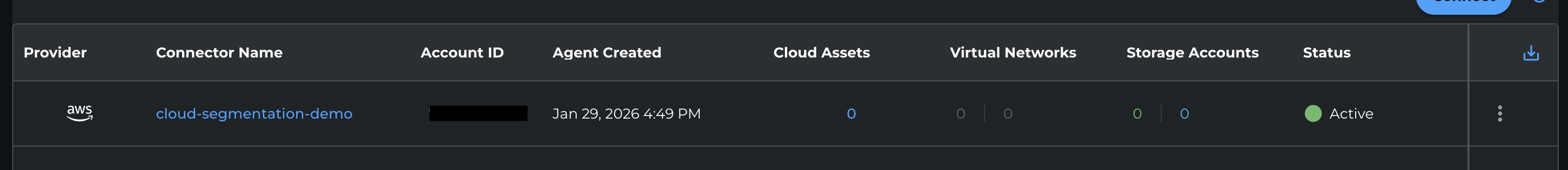
Step 4: Confirm Account Connection
Confirm that the AWS account is connected and appears in the Xshield platform. Resources from the account will begin syncing; enable VPC Flow Logs (and optionally AWS X-Ray) for full visibility as described in the Next Steps below.
Next Steps
After the AWS account is connected:
-
Your AWS resources will begin appearing in the Xshield platform
-
Network traffic analysis will be available when VPC Flow Logs are enabled and accessible
-
Application trace visibility will be available when AWS X-Ray is enabled and accessible
A sample Terraform configuration (AWS) is provided for convenience: terraform-sample-aws.zip (download). It creates the cross-account IAM role and permissions described in this guide. This is only a sample—you may need to modify it for your environment (e.g. naming, tags, or scoping resources). Replace the placeholder account ID (XXXXXXXXXXXX) with the value from the Xshield portal before running terraform apply.
Reference: IAM permissions for the cross-account role
The cross-account role that Xshield assumes (created by the CloudFormation template in Path A or manually in Path B) must have the following IAM permissions. Use this table to build Terraform, CloudFormation, or other IaC—grant these actions on the role's policy with Resource: "*" (or scope to the resources your organization allows).
| Service | IAM actions | Resource |
|---|---|---|
| S3 | s3:ListAllMyBuckets, s3:GetBucketLocation, s3:GetBucketAcl, s3:GetBucketPolicy, s3:GetBucketVersioning, s3:GetBucketPublicAccessBlock, s3:GetBucketNotification, s3:GetBucketTagging, s3:ListBucket, s3:GetObject | * |
| Lambda | lambda:ListFunctions, lambda:GetFunction, lambda:GetFunctionConfiguration, lambda:GetPolicy, lambda:ListTags, lambda:ListEventSourceMappings | * |
| DynamoDB | dynamodb:ListTables, dynamodb:DescribeTable, dynamodb:ListTagsOfResource | * |
| EC2 (instances, networking, flow logs) | ec2:DescribeInstances, ec2:DescribeTags, ec2:DescribeSecurityGroups, ec2:DescribeNetworkAcls, ec2:DescribeSubnets, ec2:DescribeVpcs, ec2:DescribeVolumes, ec2:DescribeSnapshots, ec2:DescribeAddresses, ec2:DescribeNetworkInterfaces, ec2:DescribeRegions, ec2:DescribeAvailabilityZones, ec2:DescribeFlowLogs | * |
| EC2 (NAT, gateways, VPC endpoints) | ec2:DescribeNatGateways, ec2:DescribeInternetGateways, ec2:DescribeTransitGateways, ec2:DescribeVpcEndpoints, ec2:DescribeVpcEndpointServices | * |
| EC2 (prefix lists) | ec2:DescribeManagedPrefixLists, ec2:GetManagedPrefixListEntries | * |
| RDS | rds:DescribeDBInstances, rds:DescribeDBClusters, rds:DescribeDBClusterEndpoints, rds:DescribeDBSecurityGroups, rds:DescribeDBSubnetGroups, rds:DescribeDBParameterGroups, rds:ListTagsForResource | * |
| Elastic Load Balancing | elasticloadbalancing:DescribeLoadBalancers, elasticloadbalancing:DescribeTags, elasticloadbalancing:DescribeTargetGroups, elasticloadbalancing:DescribeListeners, elasticloadbalancing:DescribeTargetHealth | * |
| API Gateway | apigateway:GET | * |
| X-Ray | xray:GetTraceSummaries, xray:BatchGetTraces | * |
The role must also have a trust policy that allows the ColorTokens AWS account to assume it. Principal: arn:aws:iam::XXXXXXXXXXXX:role/ColorTokensCloudSecurityServiceRole, Action: sts:AssumeRole. Replace XXXXXXXXXXXX with the ColorTokens account ID from the Xshield portal. See Path B Step B.1 for the full JSON.