Policy Recommendation
Overview
The Xshield Security Platform integrates advanced Machine Learning (ML) to accelerate microsegmentation, streamline policy creation, and enhance enterprise security posture. By learning continuously from internal application behavior and external security intelligence, Xshield generates near real-time recommendations that reduce operational effort and help proactively mitigate threats.
Data Foundation
Xshield analyzes a broad and continuously updated data set that enables accurate policy automation.
Internal Observations
The Xshield Security Platform continuously analyzes near real-time communication and workload context across multiple layers of the stack, including:
-
Network flow telemetry (L3–L7)
- Entity-to-entity communication paths
- Layer-4 connection metadata (ports, protocols)
- Layer-7/API behavior for containerized and cloud-native workloads
-
Host communication surfaces
- Listening and active ports
- Service exposure changes over time
-
Behavioral activity patterns
- Traffic volume trends
- Connection frequency and directionality
- Temporal characteristics (e.g., new, intermittent, or dormant services)
This multilayer observation capability enables accurate understanding of both traditional workload communication and modern API-driven service interactions, forming the foundation of ML-driven policy recommendation.
External Known Data Source
- Known malicious and high-risk TCP/UDP ports
(e.g., 445, 3389, 22) - MITRE ATT&CK Technique mappings related to high-risk ports
- CISA security advisories linked to port/service risk
This combined data foundation drives evidence-based recommendations and exposure analysis.
ML-Based Policy Recommendation Engine
Xshield continuously correlates internal telemetry with external intelligence to identify unsafe communication paths and surface actionable microsegmentation guidance.
How It Works
- Ingests real-time flow and port data
- Identifies unreviewed or unprotected listening ports and communication paths
- Correlates with MITRE, CISA, and known threat data
- Recommends security policies to reduce exposure
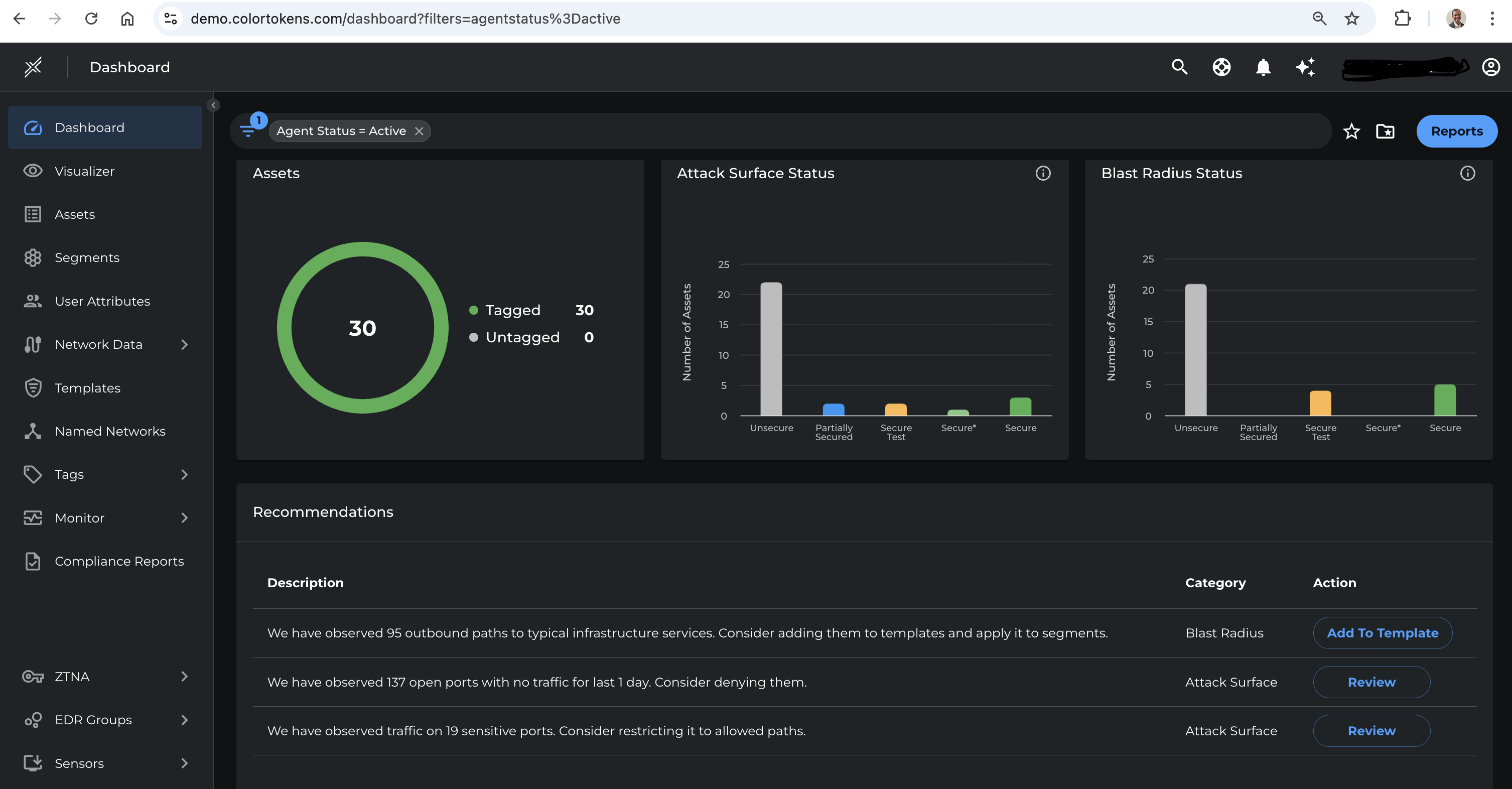
Risk-Driven Recommendation Types
| Recommendation Type | Description |
|---|---|
| Block | High-risk ports or malicious flows |
| Allow (Whitelist) | Known legitimate flows that lack policy coverage |
| Shut Down | Dormant listening ports inactive >24h |
High-Risk Port Awareness
Xshield continuously learns and catalogs high-risk ports such as:
- TCP/UDP 445
- TCP/UDP 3389
- TCP/UDP 22
- + many others associated with ransomware or lateral movement
If these ports are exposed without proper restriction, the system highlights them for remediation.
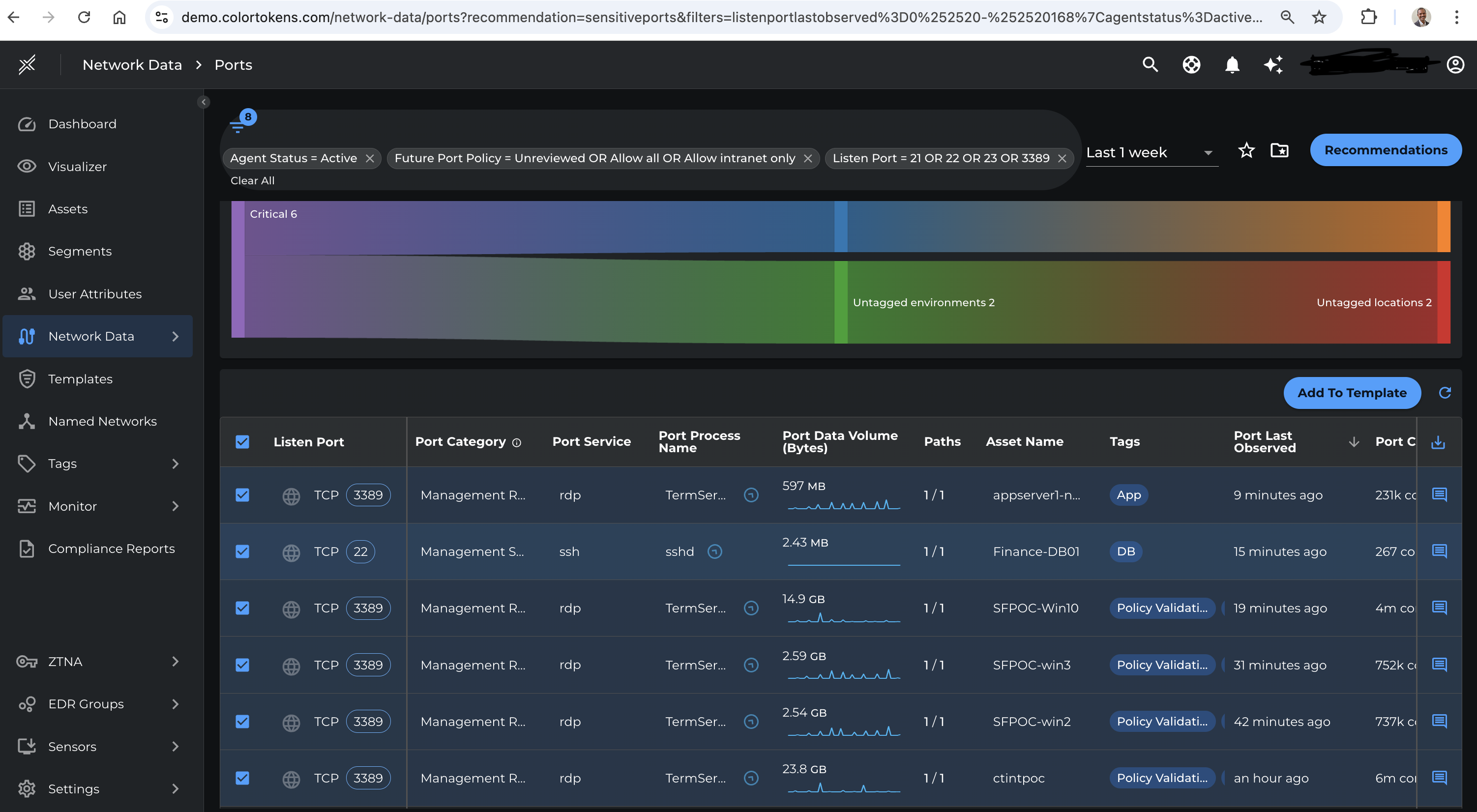
Dormant Port Cleanup
The platform detects listening ports with no activity (volume or connection count) for > 24 hours and recommends disabling or removing access to these ports, shrinking the attack surface.
Positive / Allow Recommendations
Xshield also generates recommendations for valid, benign connections that should be whitelisted to prevent false alarms.
Example:
Outbound HTTPS traffic to
support.microsoft.comon port 443 for software updates
Simulation-Mode-Driven Recommendations
When workloads are placed in simulation mode, Xshield evaluates observed traffic against existing and candidate templates to determine:
- Whether traffic would be permitted or blocked
- Which policies are needed to enable application operation
- Which flows represent violations
This enables operators to refine rules before enforcement, ensuring safe rollout without operational disruption.
End-to-End Policy Automation Flow
Data → ML Modeling → Risk Correlation → Recommendation → Simulation → Operator Review → Enforcement
High-level sequence:
- Telemetry + External Known Data
- Correlation and classification
- Policy gap identification
- Automated policy suggestion
- Dry-run simulation validation
- Operator approval
- Enforcement
Benefits
| Capability | Benefit |
|---|---|
| Near real-time policy recommendations | Faster segmentation rollout |
| Threat-aware exposure mapping | Reduced lateral movement risk |
| Dormant port analysis | Smaller attack surface |
| Positive (whitelist) recommendations | Reduced false alarms |
| Simulation-based validation | Safe operational deployment |
Conclusion
The Xshield Security Platform applies ML-driven analytics and real-time threat intelligence correlation to continuously identify risky communication paths, dormant or exposed services, and legitimate traffic requiring allow-listing. These data-driven recommendations accelerate the policy lifecycle—from discovery to validation and enforcement—helping security teams reduce lateral-movement risk, minimize attack surface, and improve operational efficiency while maintaining application continuity.