SCIM Integration
Overview
The Xshield Security Platform supports integration with external Identity Providers (IdPs) using the SCIM (System for Cross-domain Identity Management) protocol. This integration enables automated user and group data synchronization from the IdP to Xshield, allowing security policies to be created and enforced based on group membership. These policies can then be applied to all assets associated with users in those groups.
Use Case
- Automate the import of user and group information from your enterprise IdP.
- Continuously synchronize updates from the IdP such as user additions, deletions, or group changes.
- Define access policies in Xshield at the security group level, enhancing manageability and Zero Trust enforcement.
Prerequisites
Before starting the integration, ensure the following:
- A valid IdP that supports SCIM 2.0 (e.g., Azure AD, Okta, PingIdentity).
- Administrative access to the IdP for configuring SCIM endpoints and bearer tokens.
- Access to the Xshield Security Platform with appropriate configuration permissions.
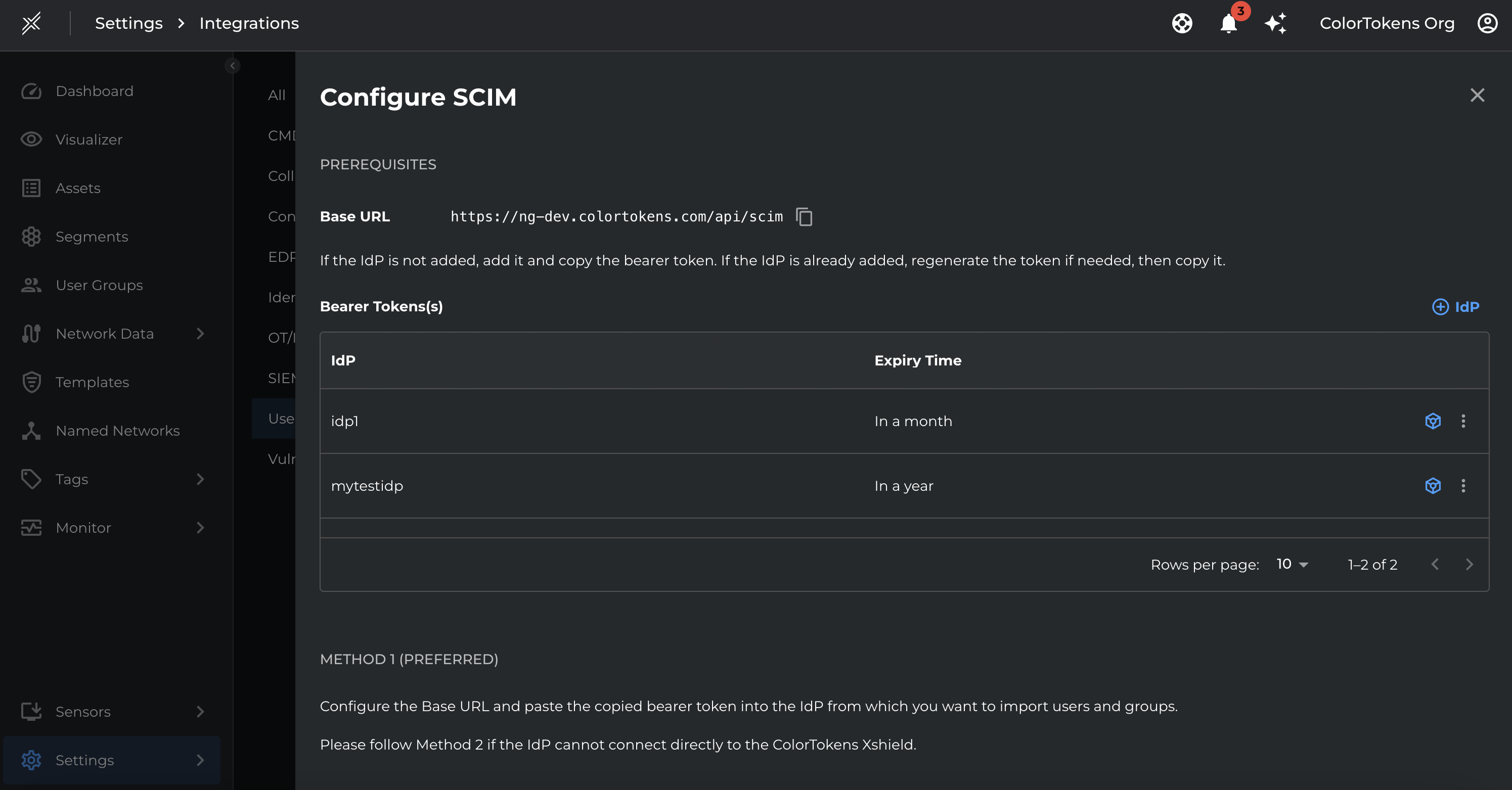
SCIM Endpoint Configuration in Xshield
To configure SCIM integration in the Xshield Platform:
-
Navigate to:
Settings→Integrations→SCIM Configuration. -
Base URL: Copy the SCIM base URL from the Xshield UI. Example:
https://demo.colortokens.com/api/scim -
Add Identity Provider (IdP): Click on the "+" icon next to “IdP” to add a new Identity Provider. This action generates a Bearer Token which must be used by the IdP to authenticate SCIM calls to the Xshield platform.
Note: If the IdP is already configured but the token has expired or needs regeneration, a new token can be generated and copied.
-
Bearer Token Usage: The generated token must be configured on the IdP side to enable authenticated SCIM calls. Each token is associated with a specific IdP and has an expiry date.
IdP-Side Configuration (Generic Steps)
On the Identity Provider portal:
-
Configure SCIM Application:
- Set the SCIM Base URL to the one copied from Xshield.
- Set the Authentication Method to Bearer Token.
- Paste the token copied from the Xshield UI.
-
Enable SCIM Provisioning:
- Ensure that SCIM provisioning is enabled.
- Configure automatic user and group synchronization frequency (if supported).
- Map IdP user attributes to Xshield-required fields, if applicable.
Methods of Integration
Method 1 (Preferred)
Use the direct SCIM connection between the Identity Provider and Xshield using the provided base URL and bearer token. This is suitable when:
- The IdP can reach the Xshield Platform over the internet.
- Real-time or periodic synchronization is needed.
Method 2 (Alternative)
If the Identity Provider cannot directly reach the Xshield Platform (e.g., due to network restrictions), alternative methods such as Connector or intermediate synchronization agents may be used.
Token Expiry and Management
- Each IdP added to the Xshield SCIM configuration receives a Bearer Token.
- The token comes with an expiry date, shown in the integration UI.
- Tokens can be regenerated as needed to maintain connectivity.
- Old tokens must be revoked on the IdP side to avoid stale or unauthorized access.
Security Policy Application
On activation of the integration, the Xshield Security Platform will sync with the IdP to import all the groups and the users associated with the group. Operator can selectively activate the user groups that they desire to use for micro-segmentation. Once the groups are selected then the users that are members of the selected groups are imported and stored on the platform. User login events notified from the Xshield agents will be used to map the endpoint (where user is logged in) to the segments mapped to the corresponding security groups
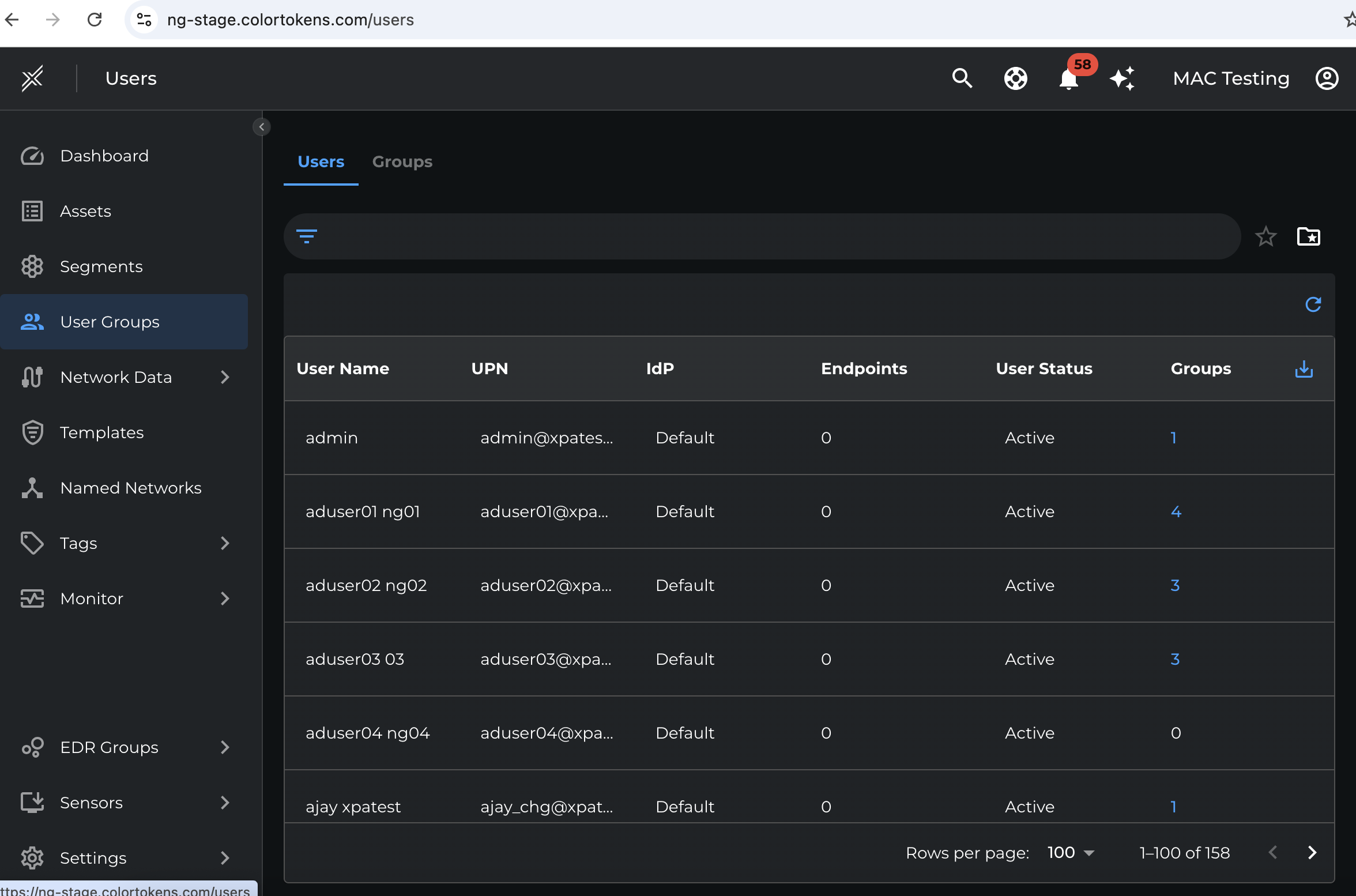
Once users and their group memberships are imported into Xshield:
- Xshield maps users to security groups.
- Policies can be defined and enforced at the group level.
- When a user logs in or accesses protected assets, the system checks their group membership and applies the relevant policy.
This model ensures scalable and role-based policy enforcement across the infrastructure.
Troubleshooting Tips
- Ensure that the bearer token is valid and not expired.
- Verify the IdP is capable of making outbound HTTPS calls to the SCIM endpoint.
- Check logs on both the IdP and Xshield for SCIM-related errors or failed syncs.
- Confirm that attribute mappings in the IdP align with Xshield’s expected schema.
Please note that importing of nested groups is currently not supported.
Summary
The SCIM integration with Identity Providers allows the Xshield Security Platform to maintain a dynamic and real-time user inventory aligned with enterprise identity governance. Through this integration, organizations can apply consistent, scalable, and automated policies based on identity group membership, reinforcing their Zero Trust posture.