Tampering Protection
The Xshield agent is a low-compute software that is running on the servers and endpoints in a customer's enterprise. It is responsible for collecting hardware, operating systems and network telemetry. Additionally, it is responsible for programming zero trust microsegmentation policies on the host firewalls of these devices.
The Xshield agent is distributed in standard package format (for each operating system) and is installed using the native installers (MSI, RPM etc). Typically, anyone with administrative privileges can install/uninstall the Xshield agent software using these mechanisms.
Since Xshield agent provides a security function, it is important that it not be stopped or uninstalled by any unauthorized user (but having the necessary privilege). This can happen when multiple users with different responsibilities have privileged access to the server or desktop.
The Xshield agent includes robust anti-tampering mechanisms to ensure continuous protection and integrity. This tampering protection mechanism ensures that only the IT security team that installed the Xshield agent also have the ability to stop the agent service or uninstall the agent.
The Xshield agent is built with a passoword based protection mechanism that prevents agent tampering and ensures that the enforced security cannot be compromised. It is important to note that this tampering protection is supporting only for the Xshield agents running on modern Windows operating systems. It is not supported on Linux or other legacy operating systems as the underlying infrastructure does not provide the necessary support.
Configuration
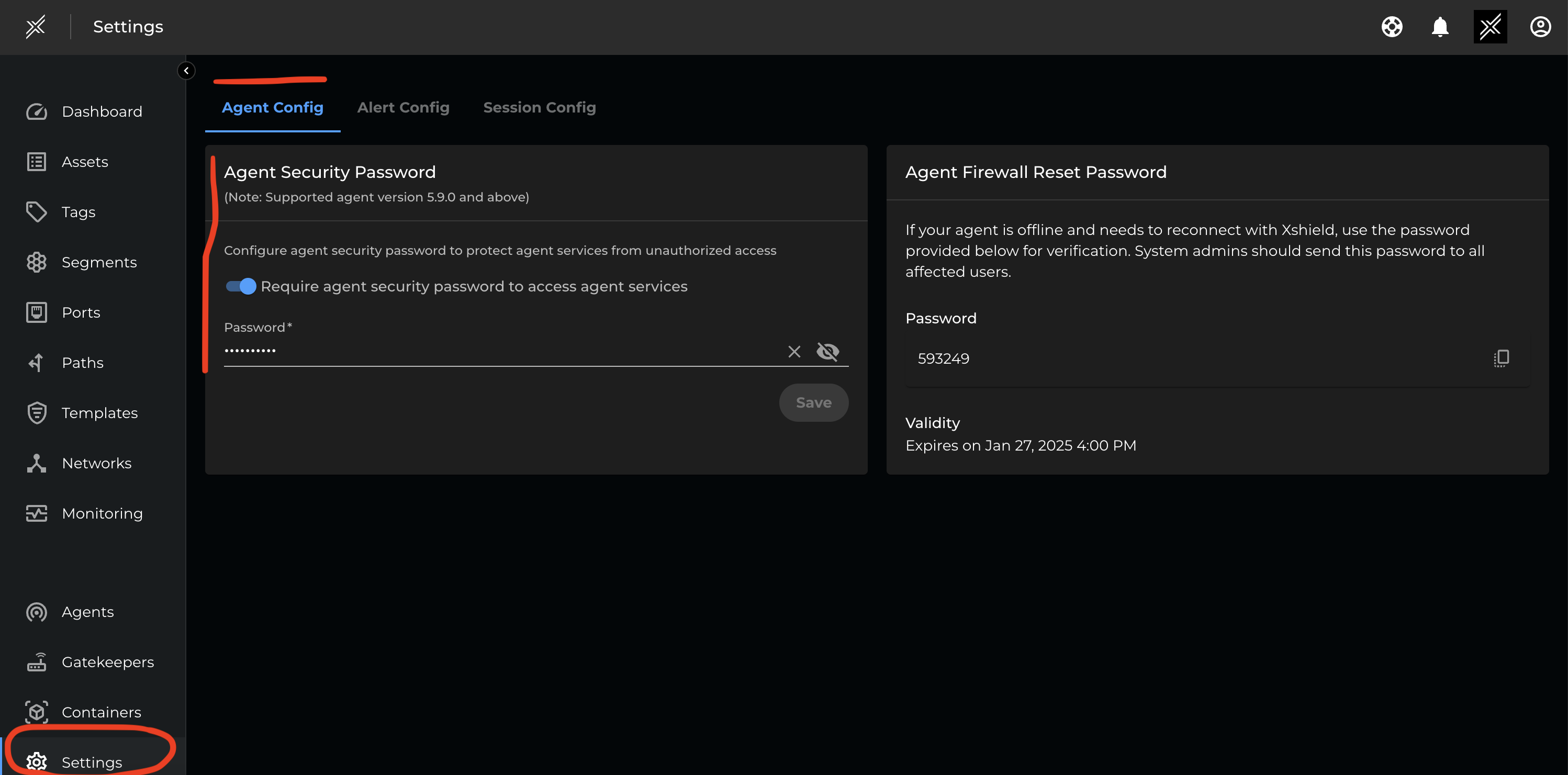
The tampering protection feature can be enabled at the tenant level.
To configure the feature, Select 'Settings' on the main page and click on the 'Agent Config' tab. Within that tab, select the 'Agent Security Password' and turnnon 'Require agent security password to access agent services'. Please enter the password that should be used for agent operations.
This configuration will be applied to all the assets belonging to that tenant (both existing and new assets).
Operations
If Agent Tampering has been enabled, then all administrative commands executed using the Xshield cmd util program will require to use the above configured password. Without the password the operations will not be performed. The following commands are protected by the password.
| Operation | Description |
|---|---|
| stop | Stop the Xshield agent |
| remove | Remove and uninstall the Xshield agent |
| disable | Stop and disable the Xshield agent. Also, reset the host firewall |
Windows
If the Agent Tamper Protection is enabled, then the user will not be able to disable the Xshield agent service from Windows 'Services' panel. The stop and restart service options will be disabled for the Xshield agent. The only way to stop the service will be to use the Xshield command util software which is password protected.
If the MSI Installer is explicitly used to uninstall the Xshield agent software (via the add/remove programs) then again the password option will be prompted to continue the uninstallation. An invalid password will fail the operation.
Linux, MacOS and AIX
In Linux, if the user has admin (sudo) privileges then the user will be able to remove the service using systemctl or sysctl which do not allow to integrate with our password protection scheme.
The password protection applies only if the user tries to remove it using Xshield command util program.
There is no viable solution to block other processes in Linux from bringing down the Xshield agent. Other AV and EDR Agents (such as Crowdstrike) use their own IOA (Indicator of Attack) rules to ensure that they do not allow process creation when process name and arguments contain matching regular expressions.