Policy Management
Xshield Segmentation - A Simplified, High-Impact Approach
Xshield transforms the traditional segmentation workflow by streamlining implementation and accelerating the realization of security benefits.
Traditional Challenges
In conventional microsegmentation projects, the process typically starts with defining granular, application-specific controls. This approach often requires extensive coordination between security, application, and infrastructure teams to map out dependencies and define precise policies.
In large enterprises—where hundreds of applications may be in scope—this leads to lengthy planning and testing cycles. As a result, the actual enforcement of policies is often delayed by several months or more than a year, during which time the organization remains exposed to lateral movement risks.
Xshield’s Accelerated Strategy
Xshield introduces a more practical and impactful approach by prioritizing enterprise-wide controls from the outset. Instead of beginning with deep application mapping, Xshield enables segmentation to start with policies targeting high-risk, unused, or non-business-critical ports across the environment.
Target High Impact Ports
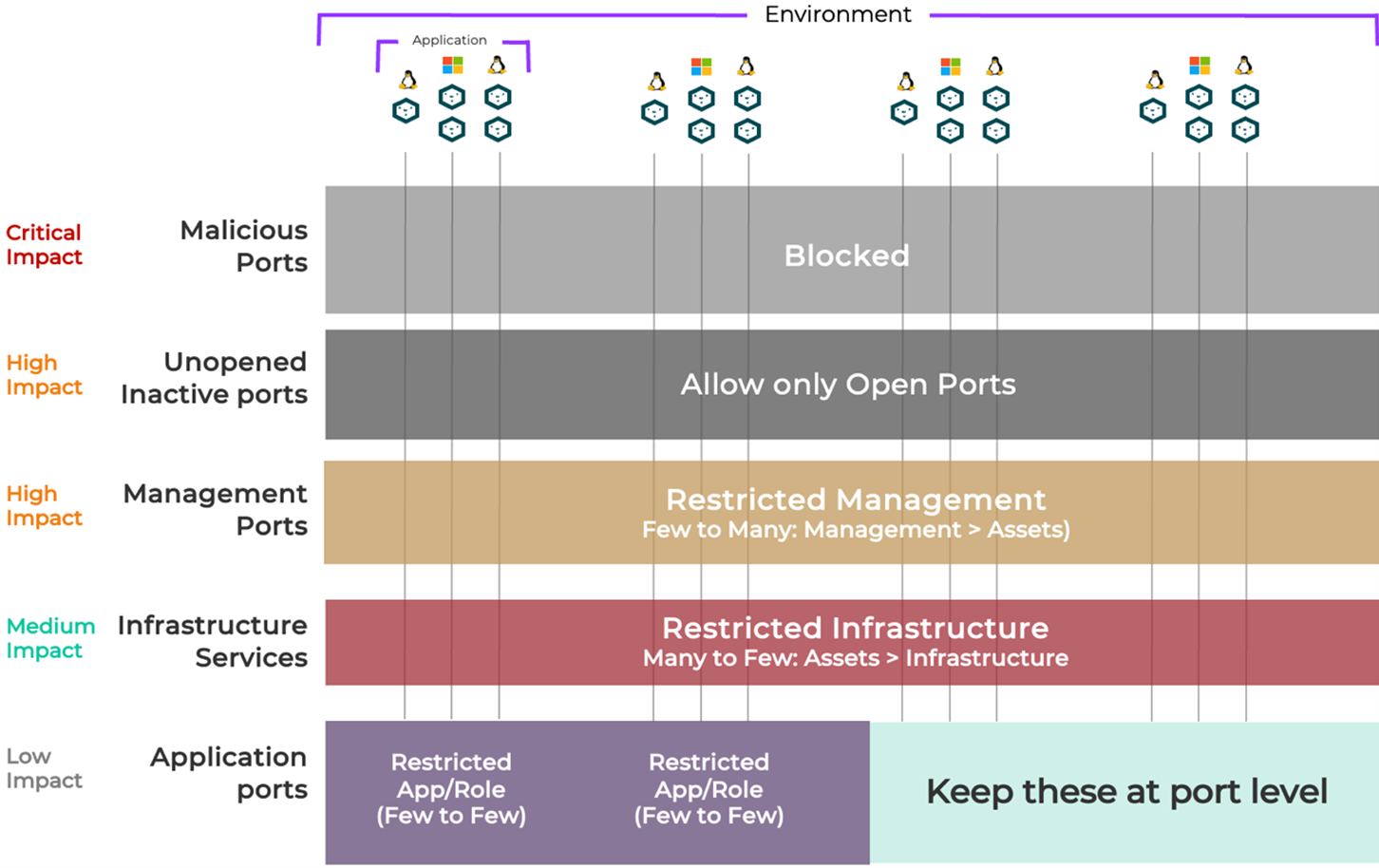
This top-down strategy offers immediate security value by:
- Blocking vulnerable or unnecessary communication paths
- Reducing the surface area for lateral movement and attacks
- Delivering quick wins that demonstrate progress to stakeholders
These initial controls are enforced through pre-defined templates and segment-based policies, enabling security teams to gain control quickly without waiting for full application discovery.
Some of the pre-defined templates
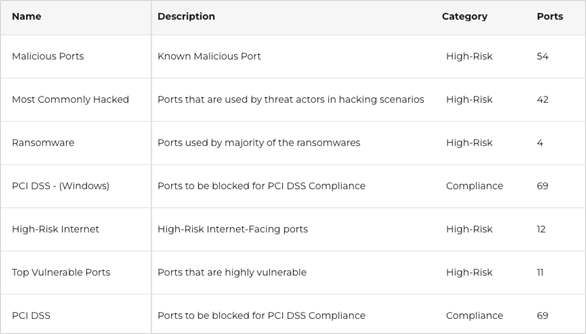
Once these baseline controls are in place, organizations can incrementally refine policies at the application level—ensuring a smooth, phased rollout that balances security and operational continuity.
Port and Path Recommendations
Enterprise environments are often dynamic and diverse, with unique application needs and network communication patterns. As a result, the specific ports and paths that must be allowed or blocked can vary significantly across environments.
Xshield simplifies policy creation by analyzing historical traffic patterns and recommending ports and paths based on actual observed activity. This intelligent discovery mechanism helps administrators understand which services are in use and what communication flows are critical to business operations.
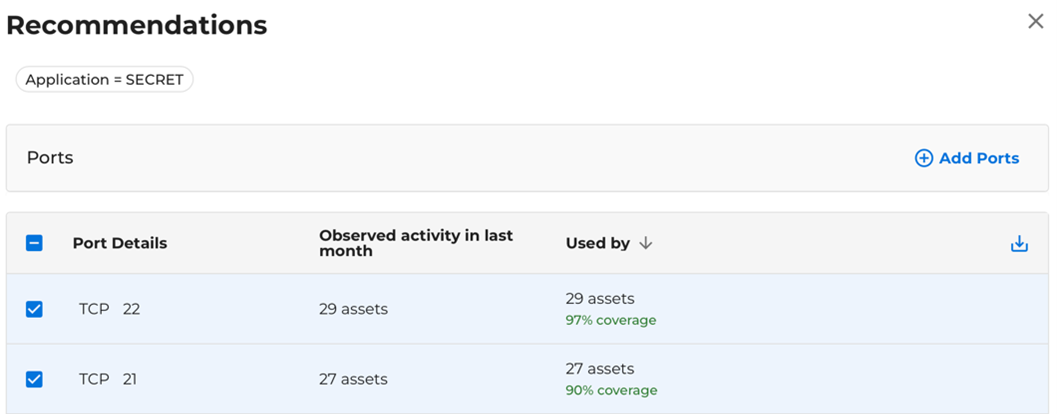
By following this guided workflow, security teams can make informed decisions, ensure policy relevance, and accelerate Zero Trust enforcement with significantly reduced effort.
Benefits include:
- Traffic-Aware Recommendations: Xshield provides actionable insights by highlighting communication paths and ports that have been used in the past, helping reduce the guesswork in policy design.
- Simplified Policy Building: Administrators can easily incorporate recommended ports and paths into templates, reducing manual effort and configuration errors.
- Identification of Unaccounted Traffic: The platform flags newly observed or unusual connections that are not yet covered by existing templates—allowing teams to take a proactive approach to securing them.
Why It Matters
- Faster Time to Value: Achieve measurable security gains soon after deployment
- Reduced Operational Overhead: Minimize delays caused by lengthy application mapping efforts
- Scalable for Enterprise Environments: Aligns well with environments managing hundreds or thousands of workloads
- Supports Breach Containment Goals: Reduces exposure and lateral movement risks even before deep-dive enforcement is complete