IoT-OT Segmentation
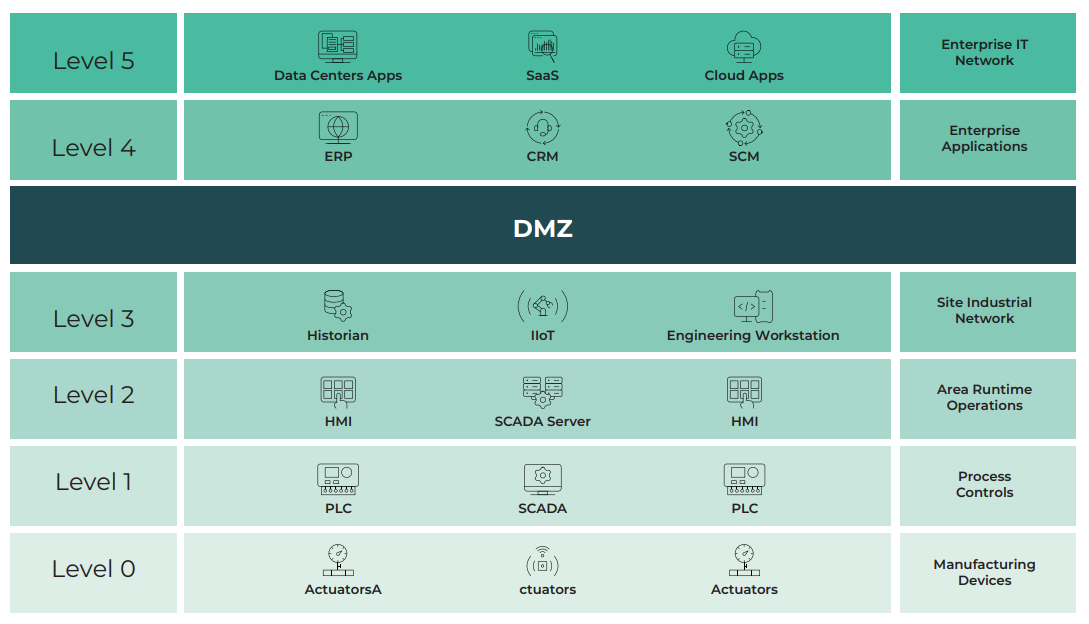
Technological progress in operational technology (OT), industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems have produced unparalleled industrial productivity increases in recent decades. Their ability to monitor and manage operations with automation has increased efficiency and agility. To protect this new technology architecture, an industrial network configuration design called the Purdue Enterprise Reference Architecture (Purdue Model) was conceived, as shown in figure 1, below. It was meant to keep organizations’ vital industrial control systems segregated from the enterprise Information Technology systems, as well as having discrete layers of separation within the OT network itself. It assumed that the industrial control systems were the crown jewels of the enterprise and that they would be disconnected and inaccessible to both internal networks and the outside world.
Layered Architectures and Perimeter Defense Are Not Enough
However, in recent years the trends of digital transformation and convergence have been pursued so that organizations can fully leverage their enterprise data and IT applications in combination with Operational Technology systems to achieve cost savings, increase productivity and gain the ability to react to market needs with agility. In addition, lateral movement of attacks can occur within the Operational Technology layers along the so-called east-west axis. An infected OT device can propagate ransomware or malware throughout the industrial network, and to the connected IT environment. All of this presents new challenges to IT infrastructure managers, CISOs and Risk Officers. Intellectual property can be stollen, and critical manufacturing processes can be interrupted or compromised.
Traditional methods of securing the network perimeter using firewalls and anti-virus detection seek to protect against attacks from the external internet. The challenge with this approach is that the adversary needs only to be successful once; the defender must be right every time. All successful ransomware or malware attacks in the past have, by definition, penetrated the perimeter defenses. It’s a question of when, not if. Particular Vurnerablities of Operational Technoloy Systems Operational Technology devices are often considered the soft underbelly for cyber attacks due to several inherent characteristics and challenges associated with their design, deployment, and management. Some key reasons include:
- Limited security measures because of resource constraints and minimal security controls such as robust encryption, secure boot etc.
- The long lifespan of OT devices means they are most likely to contain outdated software and missing security patches.
- The OT and IoT ecosystem is complex as there are a large array of manufacturers, communication protocols, and standards. This diversity introduces complexity, making it challenging to implement consistent and comprehensive security measures across the entire landscape.
- The interconnectedness of OT with IT systems increases attack surface because of lateral movement of breaches that compromise other critical systems.
- Many OT or IoT systems are easy to access physically and contain USB or network ports, interfaces that can make it easier for malicious actors to gain direct physical access to the devices to tamper with them and make unauthorized modifications.
- Limited monitoring and visibility of IoT and OT devices makes it difficult or impossible to track and detect anomalous activity or traffic patterns that are the telltale signs of a potential security breach.
- Many OT / IoT systems are rushed to market, such that security-by-design practices are not followed.
Additionally, in many organizations, infrastructure evolved over time and IT and IoT/OT devices may share the same network. OT devices may have been introduced withouth a Purdue Reference Architecture separation at all. This poses another security challenge as these systems are fundamentally different in their design, priorities, and maintenance lifecycle. The following are some of the security challenges that arise when intermixing IT and OT systems:
Divergent Priorities
While OT systems focus on reliability and availability, IT system focus more on data confidentiality, integrity, and availability. This difference in priority leads to neither objective being met.
Securing Legacy IT Systems
Many legacy IT systems were implemented before cybersecurity concerns became a top priority. As a result, these older systems often lack robust security protections and are not regularly patched to address the latest vulnerabilities. This poses a significant risk not only to the legacy systems themselves, but also to the broader IT and OT (operational technology) infrastructure due to the potential for lateral movement of threats. Disruptions to legacy systems can also lead to substantial downtime and serious business impacts, as these mission-critical systems are deeply integrated into core operations. To address these challenges, the Xshield Gateway appliance provides a solution to help protect legacy systems. By segmenting these older systems, the Xshield Gateway can minimize the risk they pose to themselves and the surrounding IT environment.
Increased Attack Surface
The convergence of IT and OT systems expands the attack surface as more devices and systems become interconnected. Any vulnerability in either OT or IT systems could potentially be exploited to compromise the integrated network. Differing Regulatory Requirements OT and IT systems may be subject to different regulations and compliance standards. Integrating these systems makes it difficult to comply with diverse regulations.
Extended Supply Chains
The convergence of IT and OT systems often extends the supply chain risk as you have a much larger set of vendors and partners. So, security risks in one part of the OT supply chain can propagate to affect the entire integrated IT/OT deployment.
The Solution
Microsegmentation for OT Systems
In contrast to the traditional perimeter defense strategy, the zero-trust security model assumes the adversary is already inside your environment; internal users, programs and devices are not to be trusted by default. Microsegmentation is a fundamental method of zero trust security. It allows you to protect devices with a micro-perimeter that stops the spread of malware or ransomware in its tracks. The Xshield Enterprise Microsegmentation Platform protects your network resources in a much more granular way than traditional VLAN based segmentation. The blast radius of an attack using traditional network segmentation is too large to provide the necessary resilience for your systems. The journey to zero trust microsegmentation begins with a map. As shown in the figure below, Xshield discovers and visualizes all your network assets, devices, applications, and their dependencies.
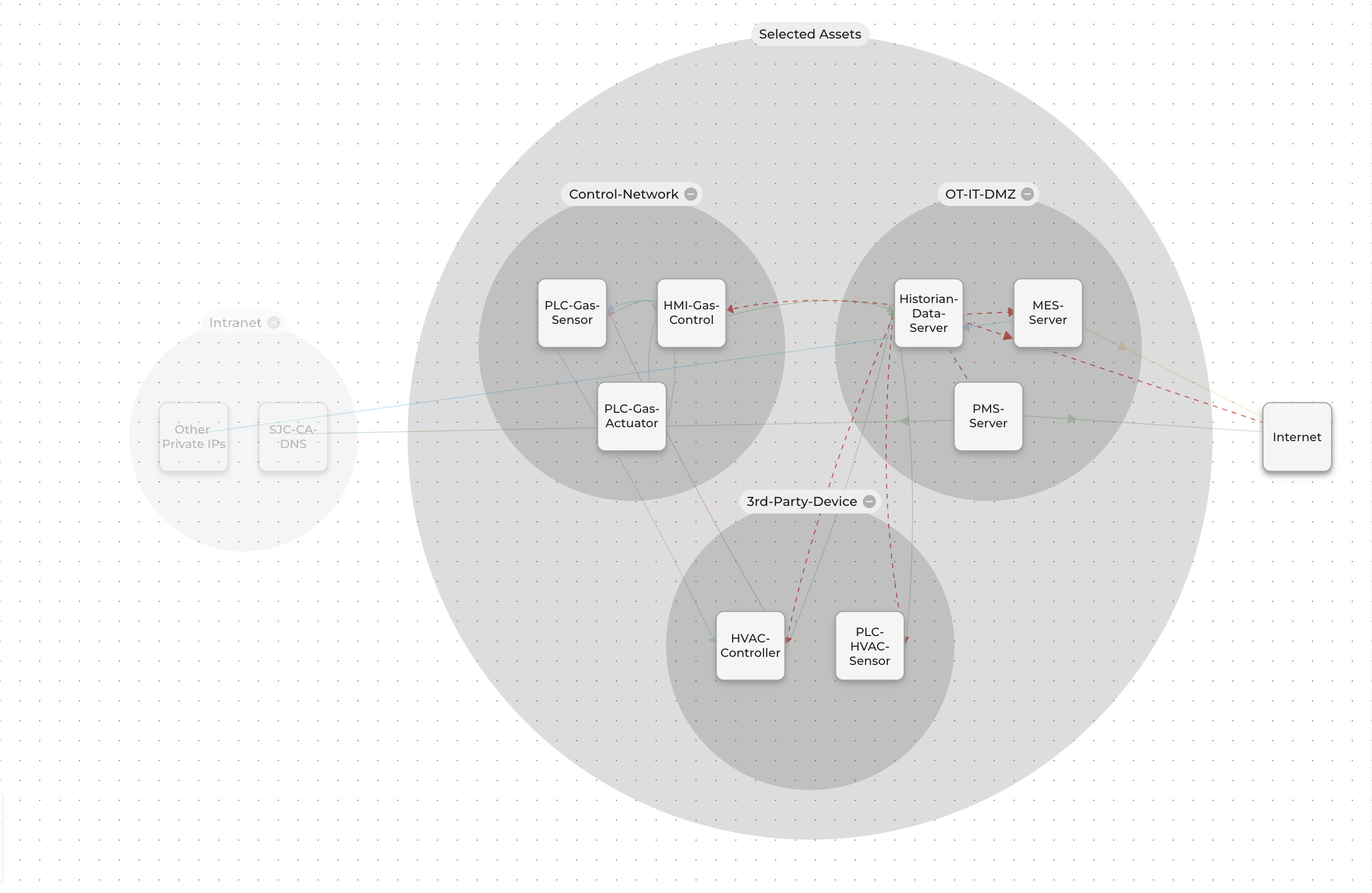
After visualization the Xshield administration console lets you set access and traffic policies to protect your network from lateral movement of malware. Xshield’s policy autosuggestion and reusable policy templates facilitate your policy authoring phase.
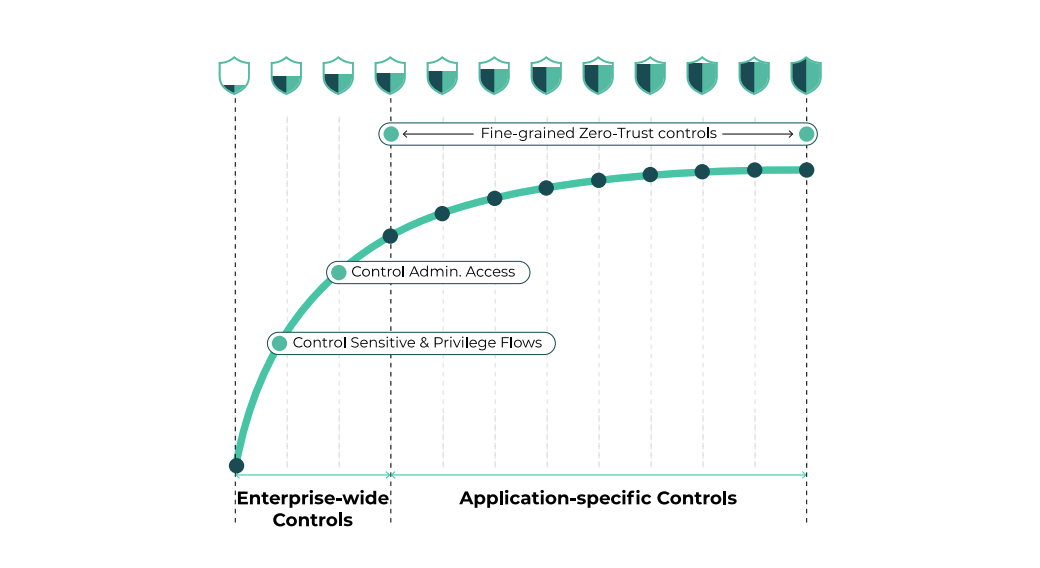
The Xshield Enterprise Microsegmentation platform lets you manage multiple types of policy enforcement points, both agent-based and agentless, from the central policy decision point. There is no need to maintain different tools to protect today’s diverse network topology which includes data center servers, cloud workloads, Kubernetes containers, OT/ IoT and user endpoints. This simplifies administration and saves on staffing and training. Supported policy enforcement points include: Xshield uses an innovative approach to microsegmentation implementation: it immediately improves your security posture by giving you risk-appropriate enterprise-wide control of risky ports and sensitive or privileged flows. Then it progresses to continuous improvement with fine-grained application-specific zero-trust controls, as shown in the figure below. • The Xshield Agent software for controlling the hundreds (or thousands) of host-based OS firewalls in your environment. • Out-of-the-box integrations with your existing deployed EDR agents • ·Service mesh sidecar proxies for securing Kubernetes containerized microservice applications at the API level. • ·The agentless Xshield Gatekeeper Appliance for securing OT, IoT and legacy operating system devices.
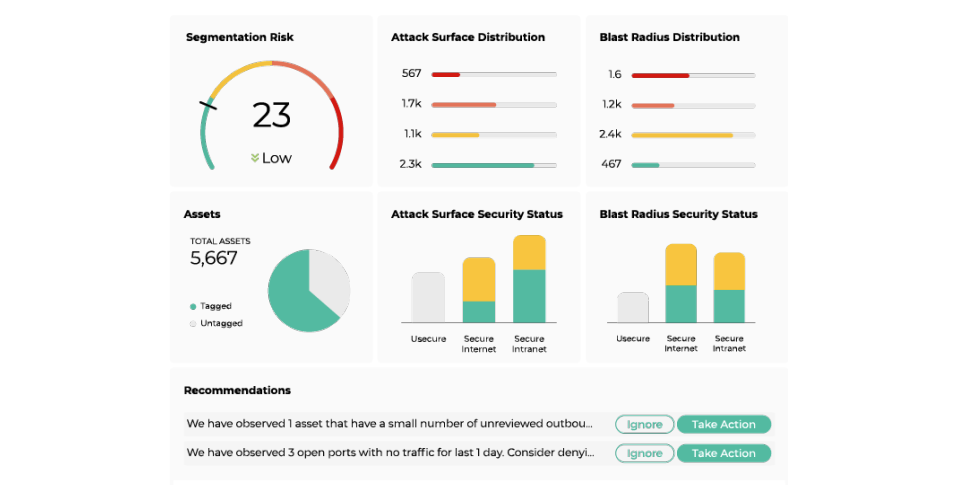
Risk and security leaders need to monitor, measure, and communicate security improvements to their stakeholders—the C-suite, their line-of-business managers, their Board of Directors—to justify budget for their initiatives and satisfy regulatory mandates. Xshield lets you measure risk and communicate the immediate and on-going improvements in your security with dashboard visualizations.
The Xshield Gatekeeper Appliance
The Xshield Gatekeeper Appliance is used for preventing unauthorized traffic to and from OT devices and preventing lateral movement between them. It does this without the need to install any agent software on the devices.
Deployment Flexibility
The Gatekeeper Appliance has a small form factor: it can be deployed as a wall mount, desktop, or DIN rail mount. It is fanless, with a wide temperature range and low latency and jitter for real-time applications. It is also useful in the case of legacy operating system devices in your data center on which an agent cannot be installed, such as HP-UX, AIX and Widows Server 2003. In this use-case, the appliance software can be installed in the data center as a Virtual Machine, instead of a discrete hardware device. Likewise, device configurations such as MS Windows-based medical device servers that cannot be patched or updated because of regulatory oversight compliance can be protected using the agentless Gatekeeper.
The Xshield Gatekeeper Appliance is designed to seamlessly integrate into diverse network topologies, providing a versatile and non-disruptive solution for securing both static and
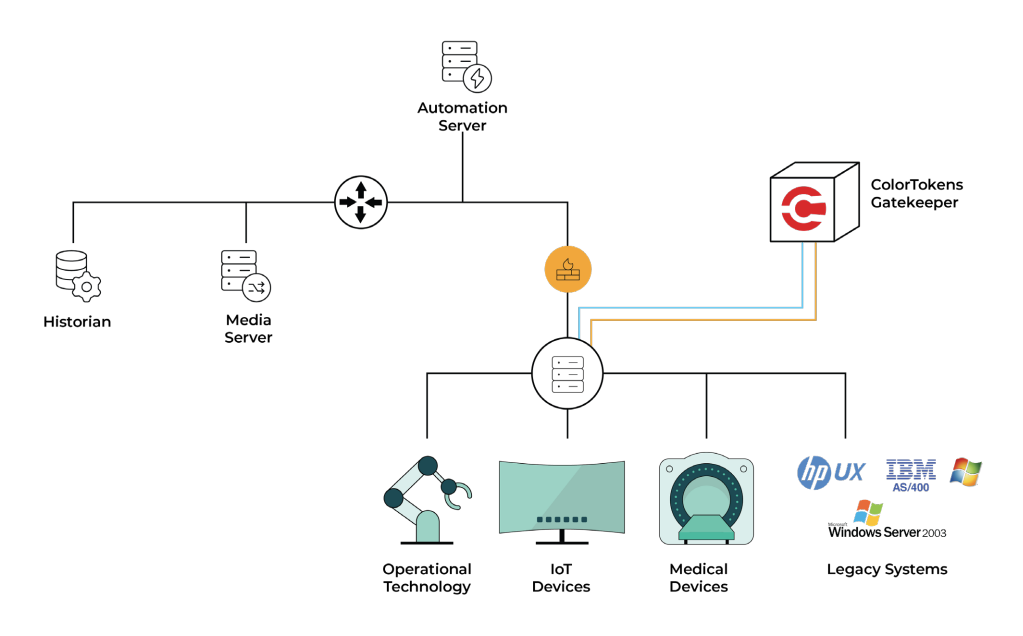
DHCP-enabled devices. Its flexible deployment options and ability to function at both Layer 3 and Layer 2 make it ideal for a wide range of network architectures. Alternatively, the appliance can be introduced into an existing subnet without the need for extensive reconfiguration. This means organizations can incrementally enhance their security posture without disrupting the operation of existing devices. As shown in figure 4, below, the Gatekeeper Appliance is deployed alongside an existing access or distribution switch. If the devices to be protected are configured using static IP addresses, they are reconfigured with a subnet mask of 255.255.255.255 and the Gatekeeper address set to the LAN IP of the gatekeeper. If the devices are configured using DHCP, the gatekeeper is configured to as the DHCP relay for the address range of the devices. No reconfiguration of the devices is required in this case.
Automated Device Discovery and Management
Once placed within a subnet, the Xshield Gatekeeper Appliance dynamically discovers devices by monitoring and analyzing the traffic flowing through the subnet. This ensures that all devices, both static and DHCP-enabled, are identified without manual intervention.
Non-Disruptive Implementation
No Disruption to Existing Devices: the deployment of the Xshield Gatekeeper Appliance is engineered to be non-disruptive to existing devices within a network. Its introduction does not impact the performance or connectivity of devices, ensuring business continuity during the integration process. Minimal Configuration Changes: the appliance is designed to minimize the need for extensive configuration changes. Its ability to seamlessly integrate and discover devices without disrupting existing operations simplifies the implementation process.
Compatibility with LANs and VLANs
LAN and VLAN Support: The Xshield Gatekeeper Appliance seamlessly integrates with both Local Area Networks (LANs) and Virtual LANs (VLANs), ensuring compatibility with various network segmentation strategies. This adaptability enables organizations to implement security measures tailored to their network architecture.
Enhanced Device Support and Integration
The Gatekeeper Appliance is engineered to provide robust security for a wide spectrum of devices, including IoT, OT, and legacy IT systems such as mainframes and out-of-support applications and operating systems. Its versatile architecture ensures comprehensive protection across the evolving landscape of connected devices. The Gatekeeper Appliance seamlessly integrates into the Xshield Enterprise Microsegmentation Platform, forming a cohesive and powerful security solution. This integration enables centralized management and control, allowing organizations to efficiently secure and monitor their entire network infrastructure.
Auto-Tagging and Contextualization
Leveraging the integrated Xshield Network Segmentation Platform, the Gatekeeper Appliance supports auto-tagging of newly discovered devices. This capability, coupled with integration features with solutions such as Claroty and CrowdStrike, ensures quick and accurate contextualization of devices within the network. This not only aids in rapid identification but also enhances the platform’s ability to respond effectively to emerging threats.
Templatized Policy Management
The Gatekeeper Appliance harnesses the templatized policy management feature within the Xshield platform to facilitate efficient and uniform policy enforcement across all connected devices. This templated approach ensures consistency and ease of management while delivering robust security measures tailored to the unique requirements of each device type.
Conclusion
As organizations navigate the complex landscape of IoT and OT security, the ColorTokens Xshield Enterprise Microsegmentation Platform with the Xshield Gatekeeper Appliance emerges as a robust solution. The significance of securing operational technology cannot be overstated, and the Xshield Gatekeeper Appliance stands as a comprehensive security solution, seamlessly extending its protective capabilities to diverse devices within IT, IoT, and OT environments.
It supports robust security measures that facilitate efficient management, auto-tagging, and context-aware policies making it possible to respond to emerging threats. Its templatized policy management and comprehensive firewalling capabilities empower organizations to maintain granular control over all connected devices, enhancing their cybersecurity posture in an ever-evolving threat landscape. Xshield Gatekeeper appliance supports both static and dynamic IPs, and all network topologies by offering multiple choices for deployment. It serves as a comprehensive and practical choice for safeguarding industrial processes by aligning with the Purdue Enterprise Reference Architecture (PERA) model, organizations can proactively address the challenges of IoT/OT security, prevent lateral movement vulnerabilities, and fortify their critical infrastructure against evolving cyber threats.