Handling Large Path Counts
Question
The tenant Path dashboard is showing a very high number of paths for an asset. What are the reasons for it and how can the count be reduced so that the actual paths are less in count and more meaningful.
Answer
When large number of paths are reported by an asset on the platform, it is usually hard for a user to consume that information to build proper policies. Most of application servers have a very distinct and finite set of communications. When large numbers of paths are detected, it is usually indicative of a mis-configuration on the platform to make that data more concise.
This article will explain the different situations in which path count can be high and how to reduce it.
Outbound Traffic Example
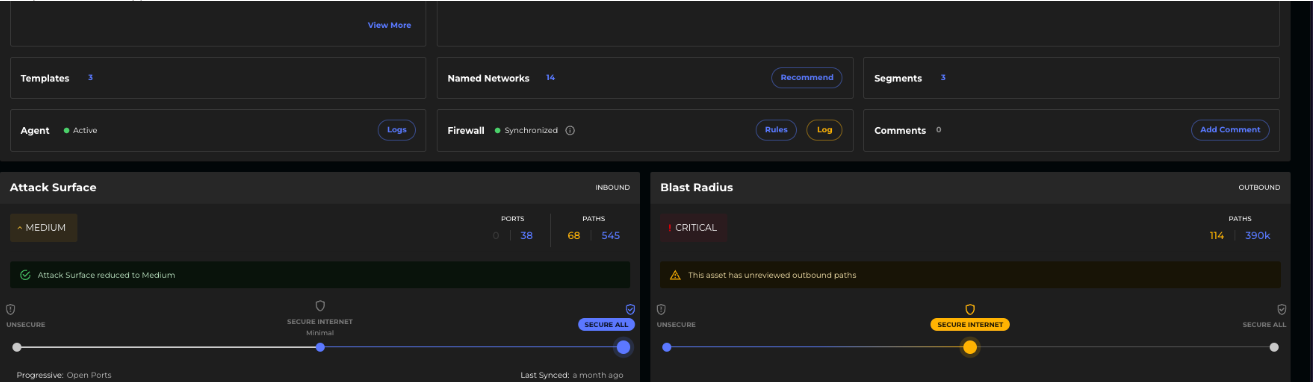
Generally, for Outbound traffic, this occurs in servers hosting scanners or applications like SolarWinds.
Example: SolarWinds Application
Sample Paths
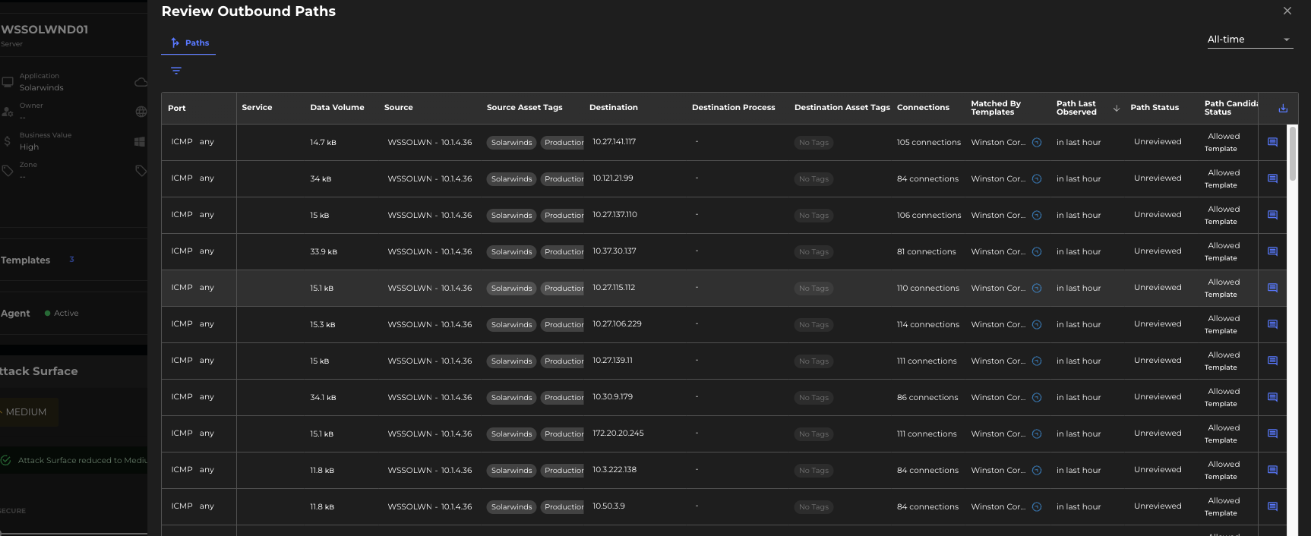
In the above example, it is performing ICMP outbound traffic across the intranet and possibly the internet as well.
Until proper Named Networks (NNs) are defined for the intranet, we can add a policy like:
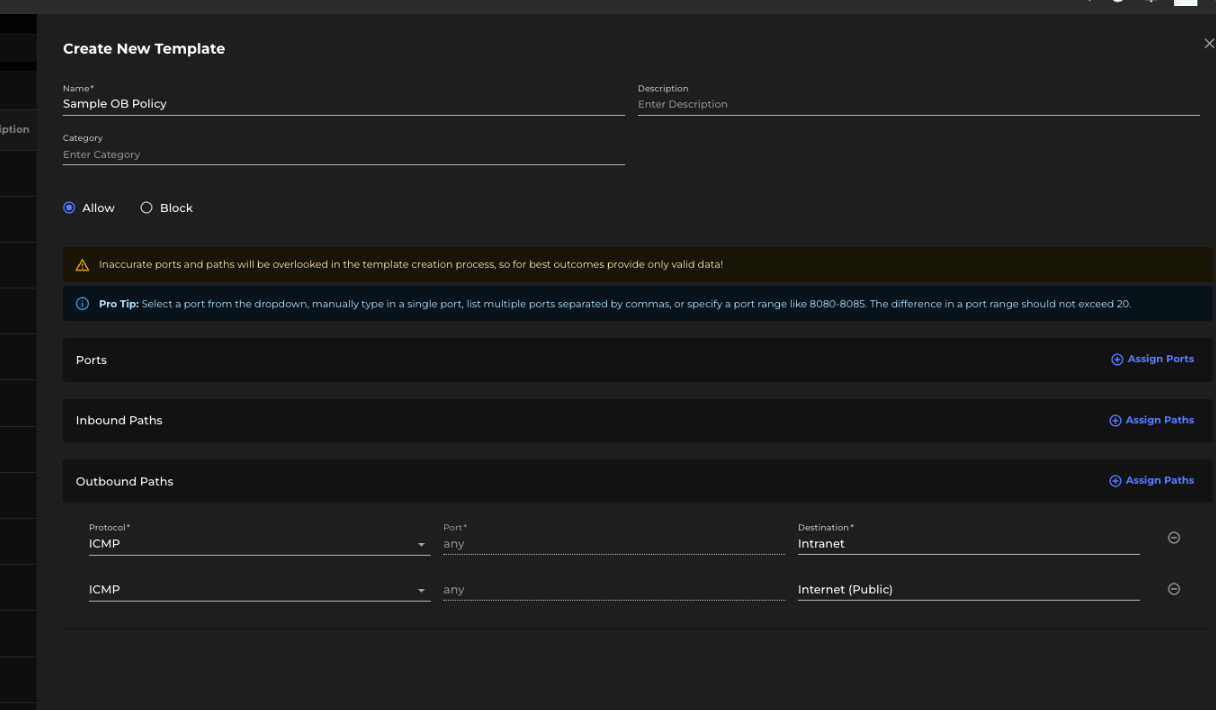
This can be generalized for other ports.
In the worst-case scenario, if a scanner is making outbound connections on all ports (1-65K) to all assets in the intranet, it will still result in 65K paths. However, this is still a significant reduction from the initial 390K paths to 65K worst case.
Inbound Traffic Example
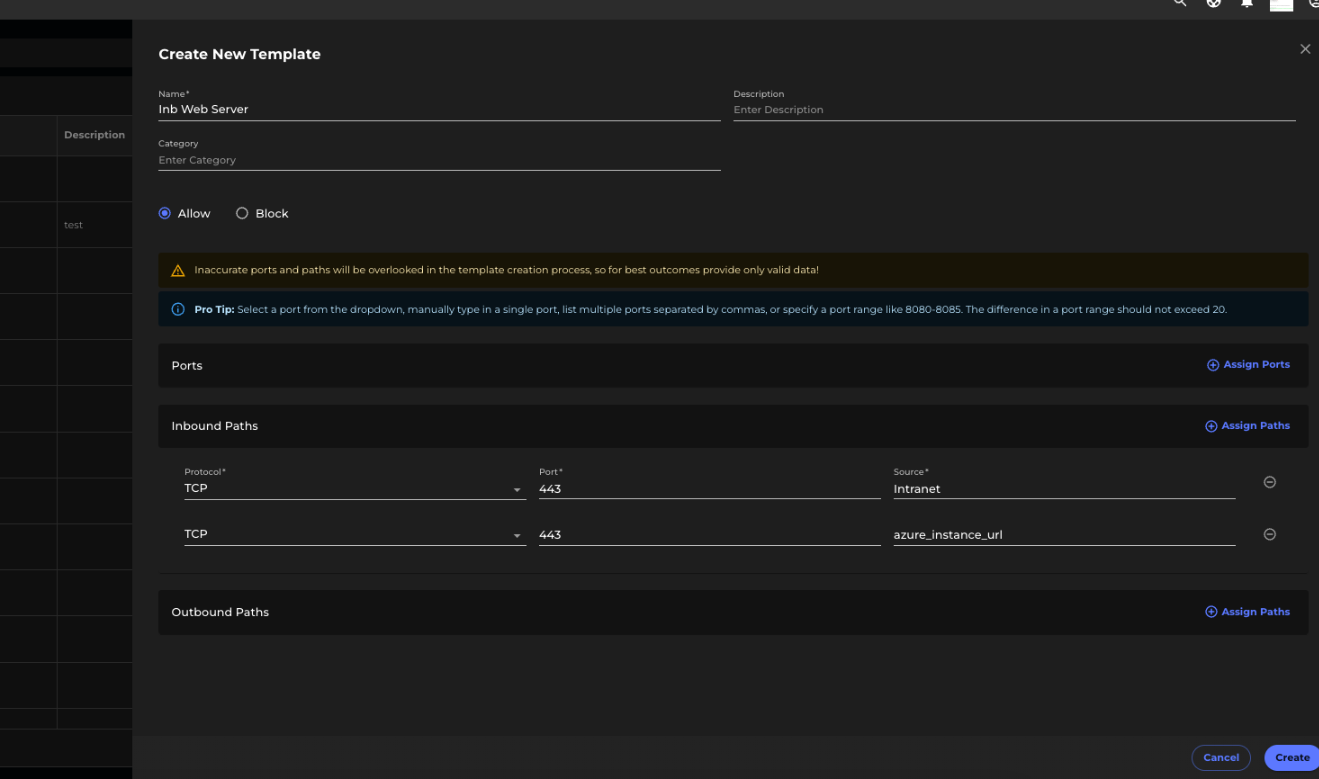
For inbound traffic, let's take an example of AD Server, LDAP Server, DNS Server, Web Server, App Server, or DB Server, where we may observe a high number of inbound paths.
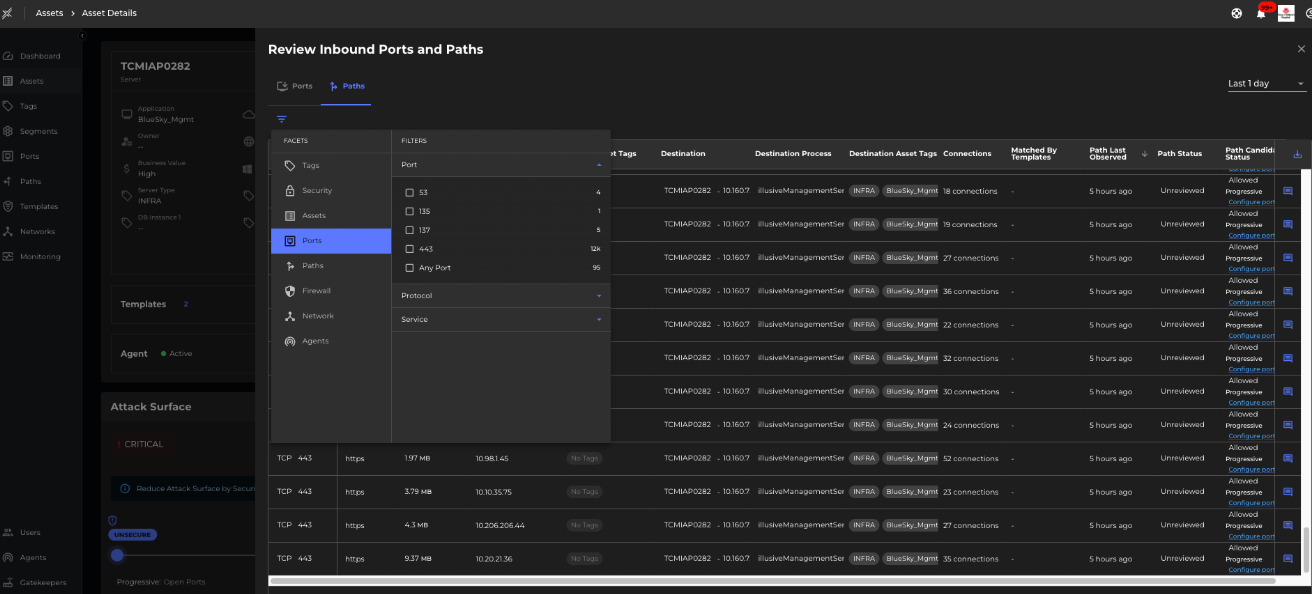
In the example above, we observe inbound traffic on port 443 from across the intranet.
Until we define proper NNs, we can apply a policy like:
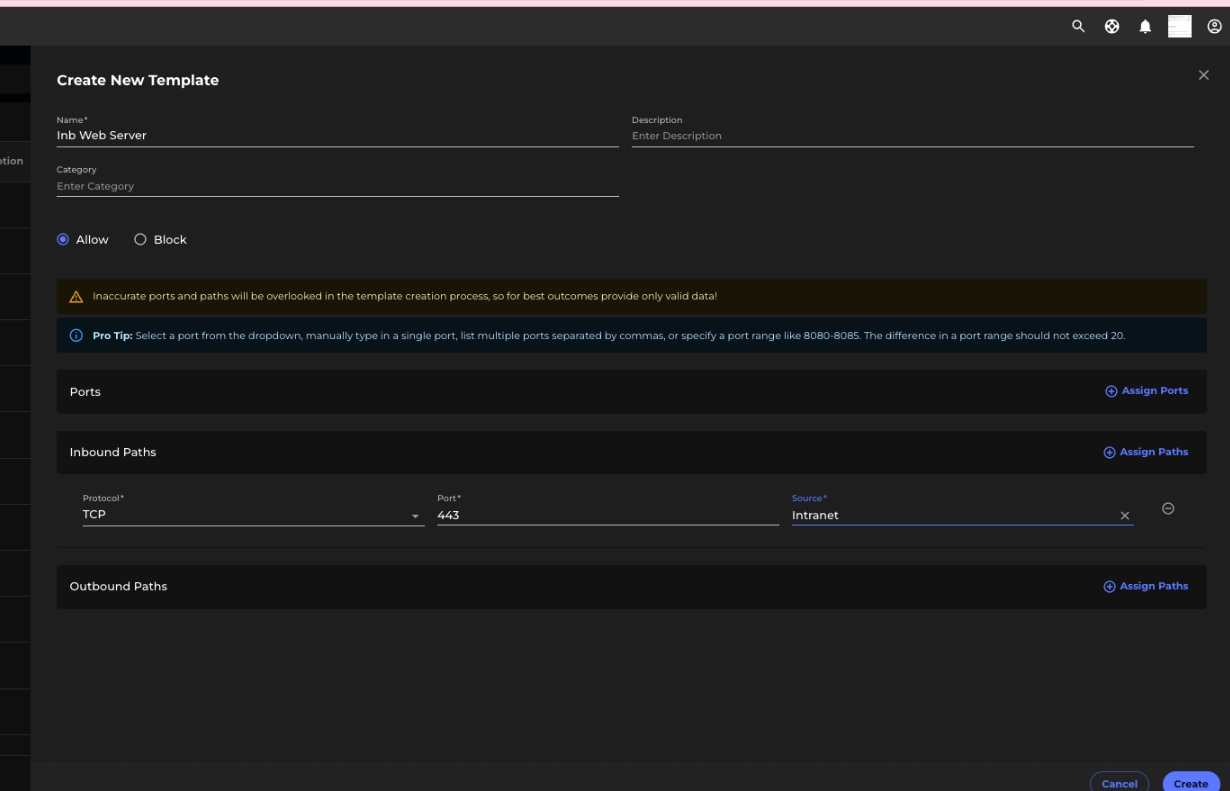
As we gain a better understanding of NNs, we refine and define more granular policies, continually enhancing our templates.
Example of Refining Policies with Named Networks