Generate API Credentials for Integrating Microsoft Defender for Endpoint with Xshield platform
1. Overview
This document outlines the manual steps required to generate API credentials in Azure and configure Microsoft Defender for Endpoint (MDE) to enable secure programmatic integration with the Xshield Security Platform.
These credentials are necessary for Xshield to perform authorized API calls to MDE and access Host information.
2. Summary Table: Microsoft Defender for Endpoint with Xshield
| Step Name | Why it’s Required | Outcome After Completing the Step |
|---|---|---|
| Register Entra Application | Creates an identity for Xshield in Azure AD to authenticate with Microsoft Defender for Endpoint APIs | A new Entra application is registered |
| Generate Client Secret | Provides secure programmatic access; acts as a password for the registered application | Entra application client secret is generated |
| Assign API Permissions | Grants the necessary access rights (like Machine.Read.All) to allow Xshield to query Defender APIs | API permissions are assigned to the Entra application |
ColorTokens provides a terraform script to automate the manual steps outlined in this document. To use the terraform script, please follow the instructions in Generate API Credentials for Integrating Microsoft Defender for Endpoint with Xshield platform using Terraform
- Use the provided output values (
client_id,tenant_id,client_secret,storage_account_name, andqueue_name) to configure the integration in the Xshield platform.
3. Configuration Steps
The following sections guide you through setting up the required Azure resources and permissions to allow Xshield to retrieve network telemetry from Microsoft Defender for Endpoint:
1. Register Entra Application and Generate Credentials
Register a new application in Microsoft Entra ID and create the necessary client secrets. This application will be used to authenticate and authorize Xshield to access MDE.
1.1 Register Application
-
Navigate to: entra.microsoft.com
-
Go to App registrations > New registration
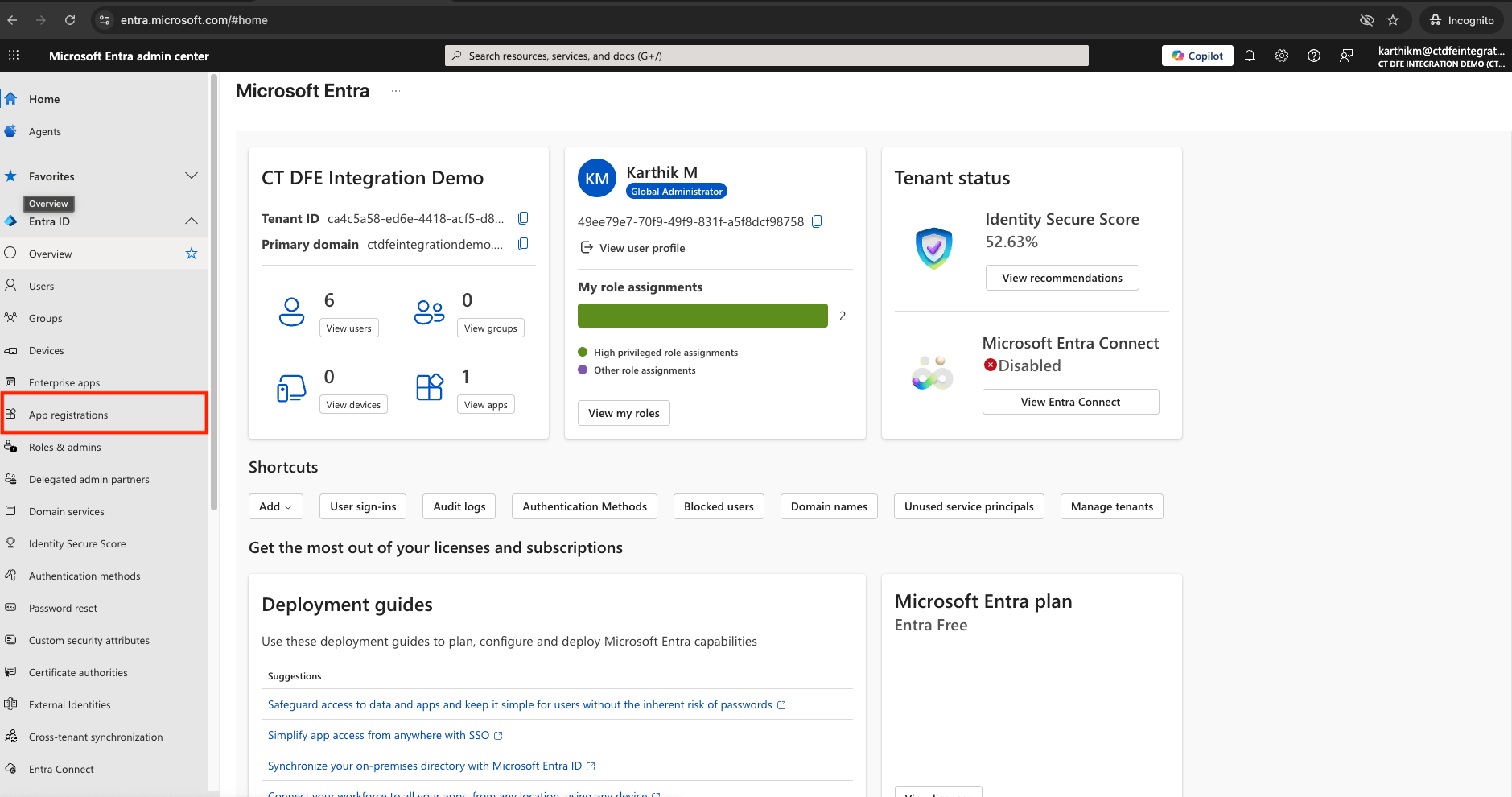
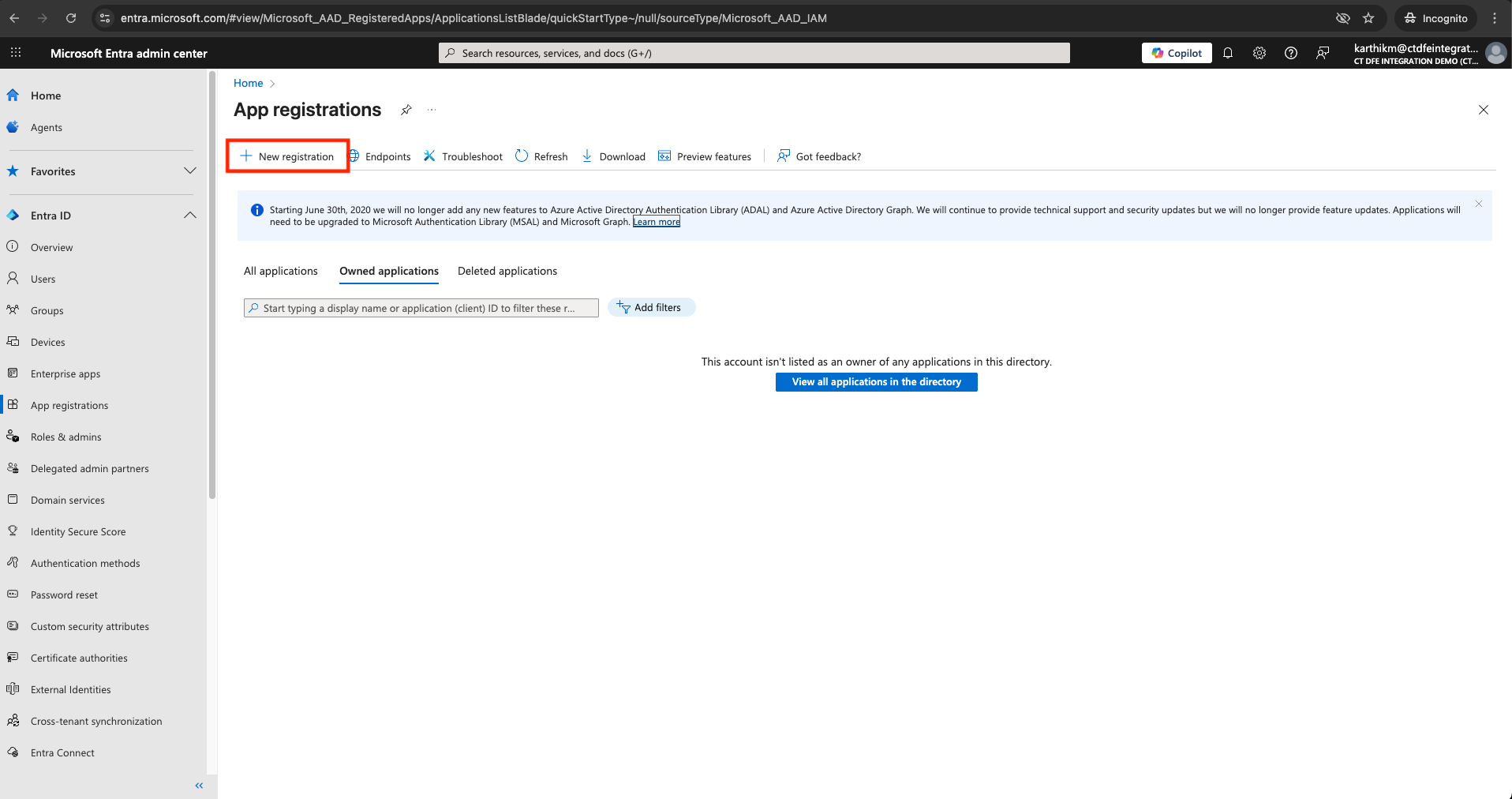
-
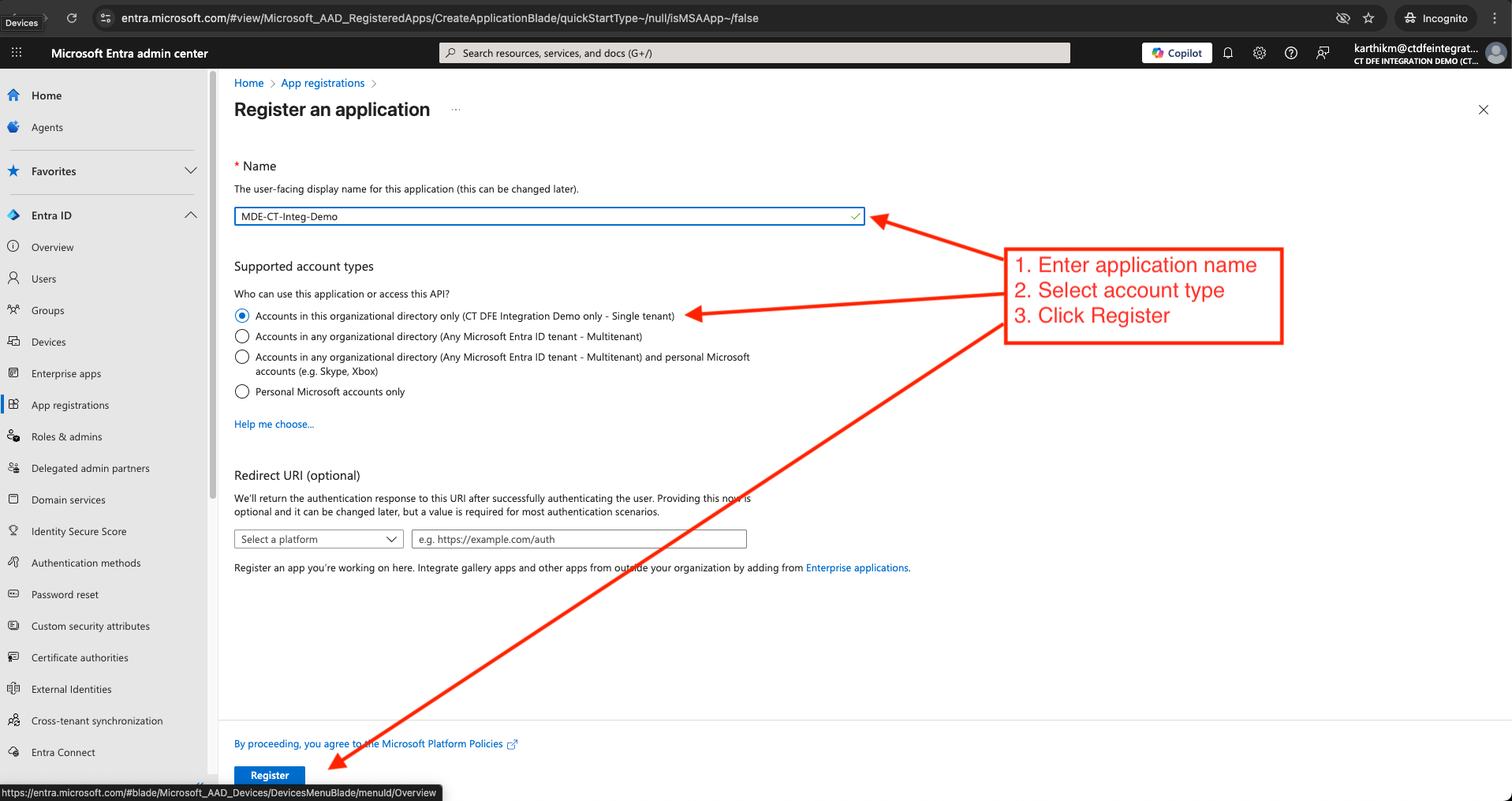
Provide a name, select “Accounts in this organizational directory only” for "Supported account types", and click Register
-
From the Overview, copy:
-
Directory (tenant) ID
-
Application (client) ID
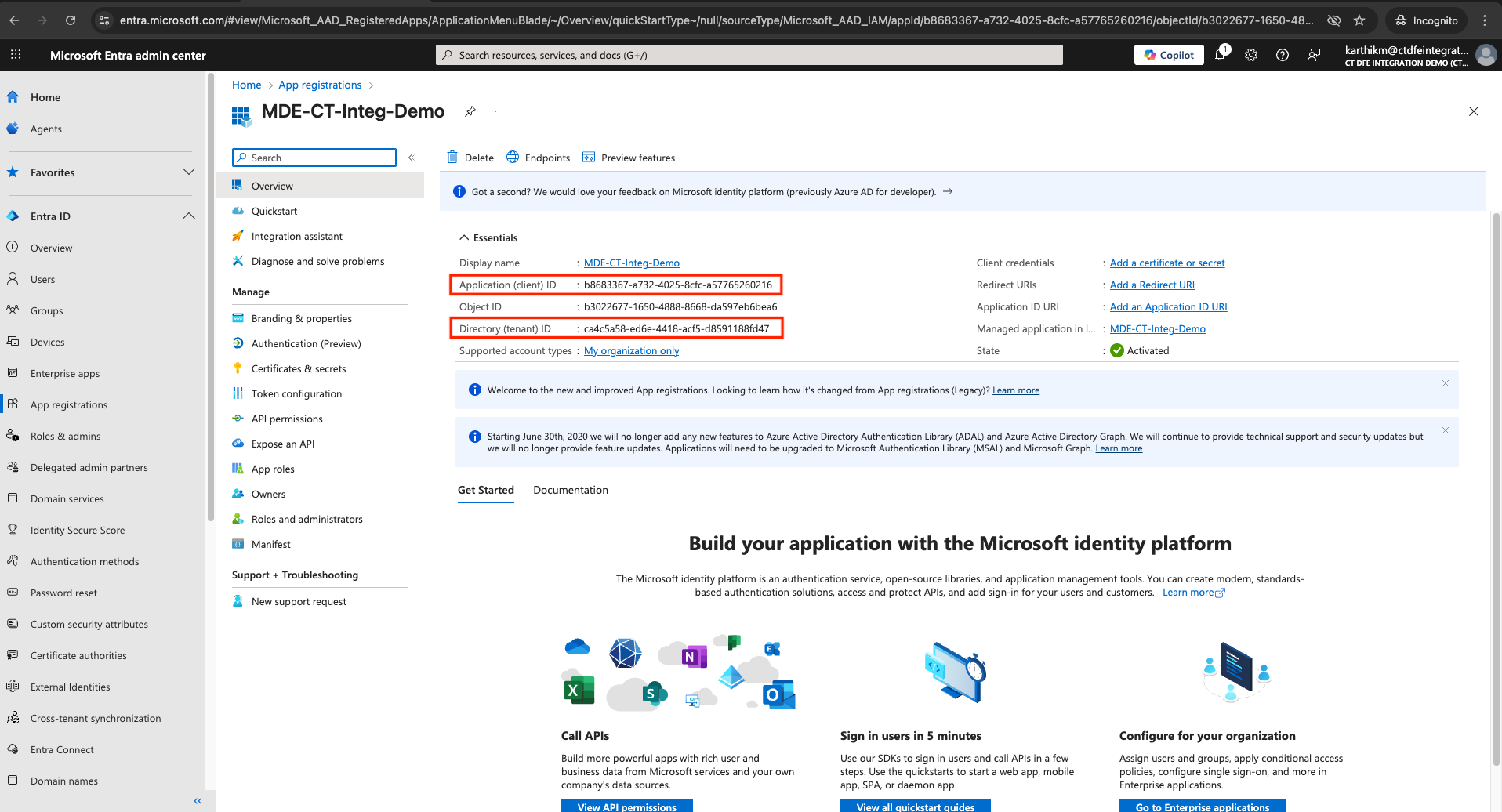
These two values represent the Tenant ID and Client ID that must be provided while activating the integration in Xshield platform.
1.2 Generate Client Secret
-
Click on the newly registered entra application and navigate to Certificates & secrets > New client secret
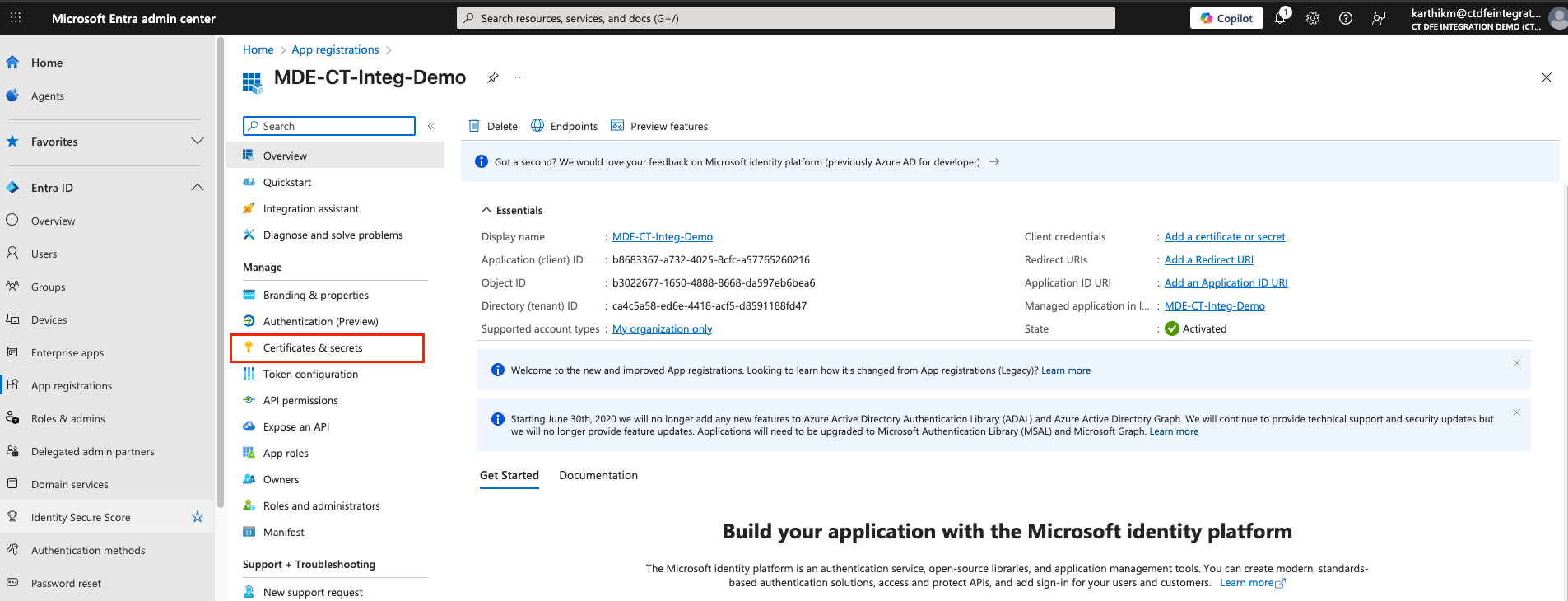
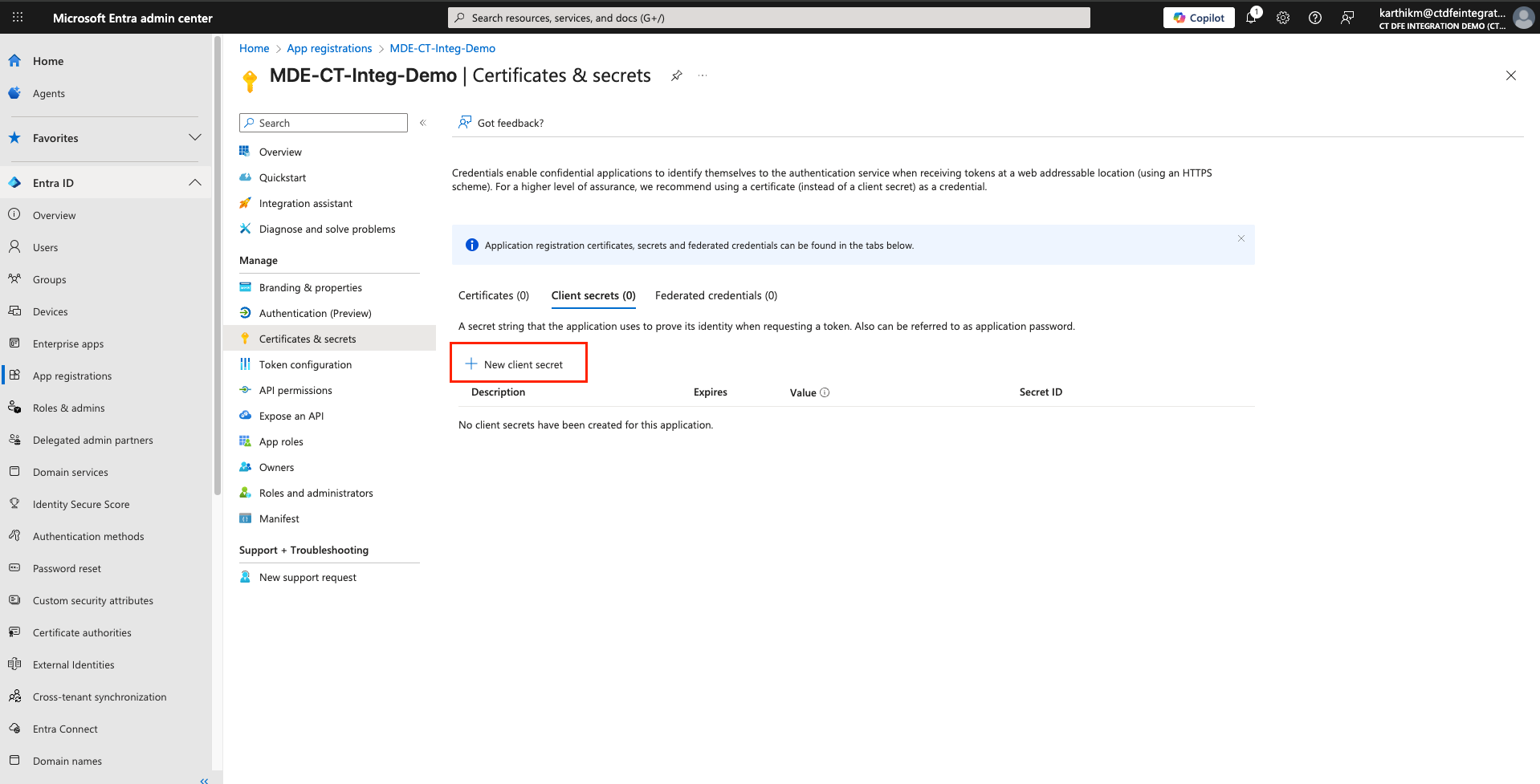
-
Enter a description, set the expiration to 24 months, and click Add
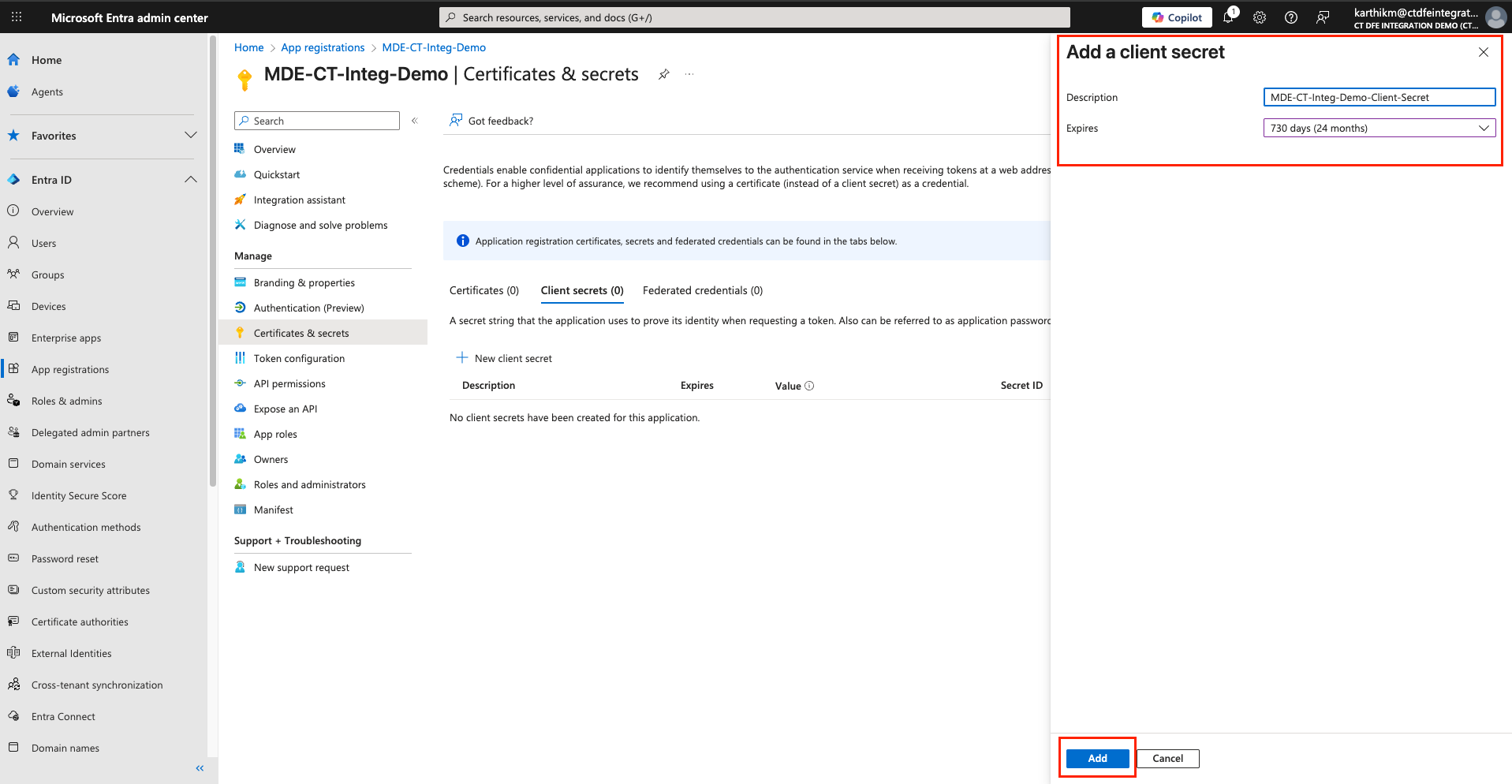
-
Copy the value from the Value field in the Client secrets section
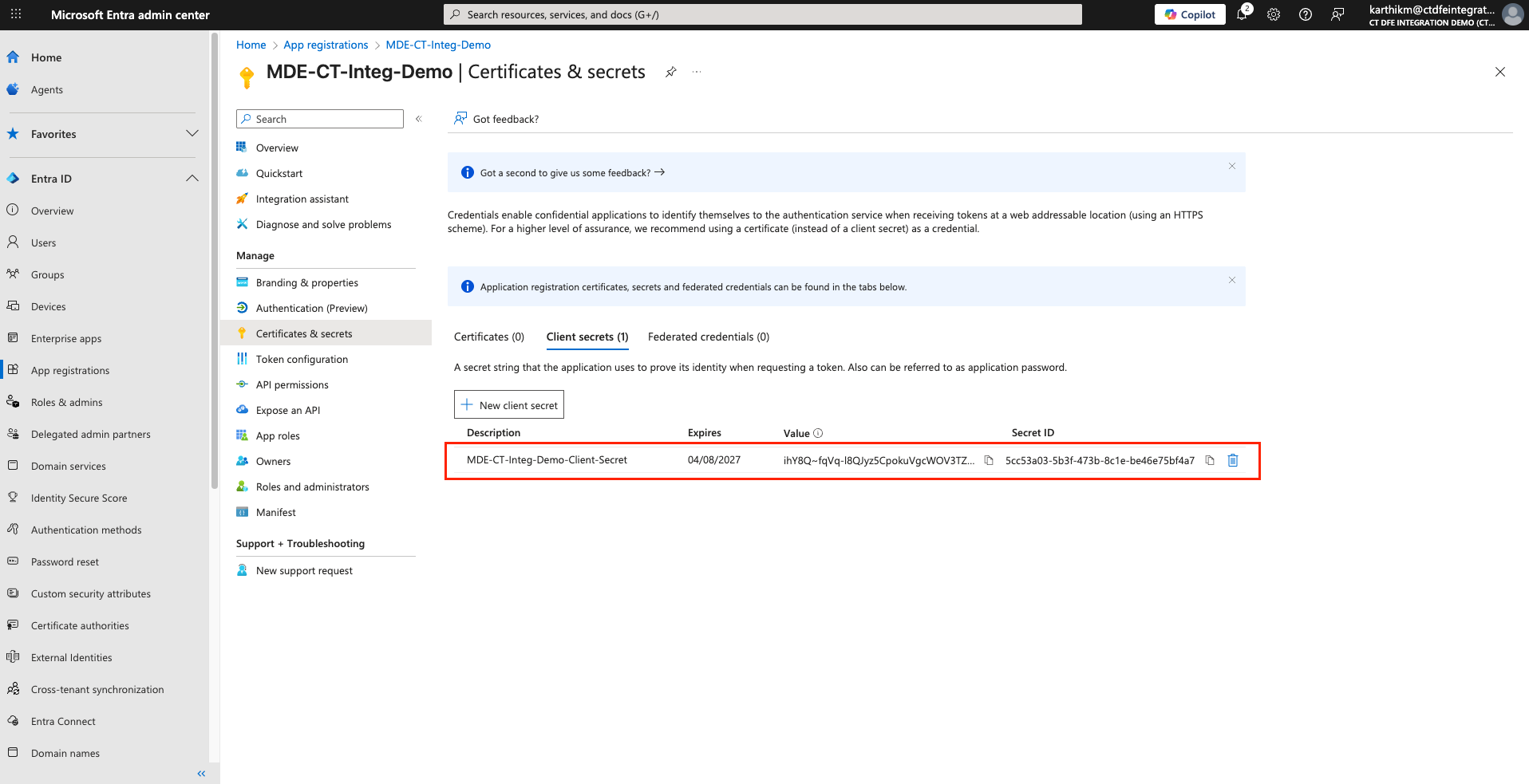
⚠️ This value represents the client secret (not the Secret ID). Store it securely, you will not be able to retrieve the secret value again after this.
- The copied value is the Client Secret that must be used when activating the integration in the Xshield platform.
- Once the secret expires, you will need to generate a new one and update it in the Xshield platform.
7. Create Event Subscription for Blob Notifications
Configure Event Grid Event Subscription on the Azure storage account with Endpoint Type Storage Queue to let Xshield know about new blob creation events.
Follow the below steps to create Event Grid Event Subscriptions:
- Go to Storage Account > Events > + Event Subscription
- In the Basics tab:
- Provide an appropriate value for Name
- Provide an appropriate value for System Topic Name
- We only want to monitor Blob Created Events:
- Under Filter to Event Types in the EVENT TYPES section, select only Blob Created
- To send a notification to the storage queue when a blob is created:
- Select Storage Queue as the Endpoint type
- Click on Configure an Endpoint, then select the desired storage queue
- In the Filters tab:
- We only want to raise notification events when blobs are created in the container
insights-logs-advancedhunting-devicenetworkevents:- Enable Enable subject filtering
- Set Subject Begins With to:
/blobServices/default/containers/insights-logs-advancedhunting-devicenetworkevents/
- Finally, click on the Create button to create the Event Subscription
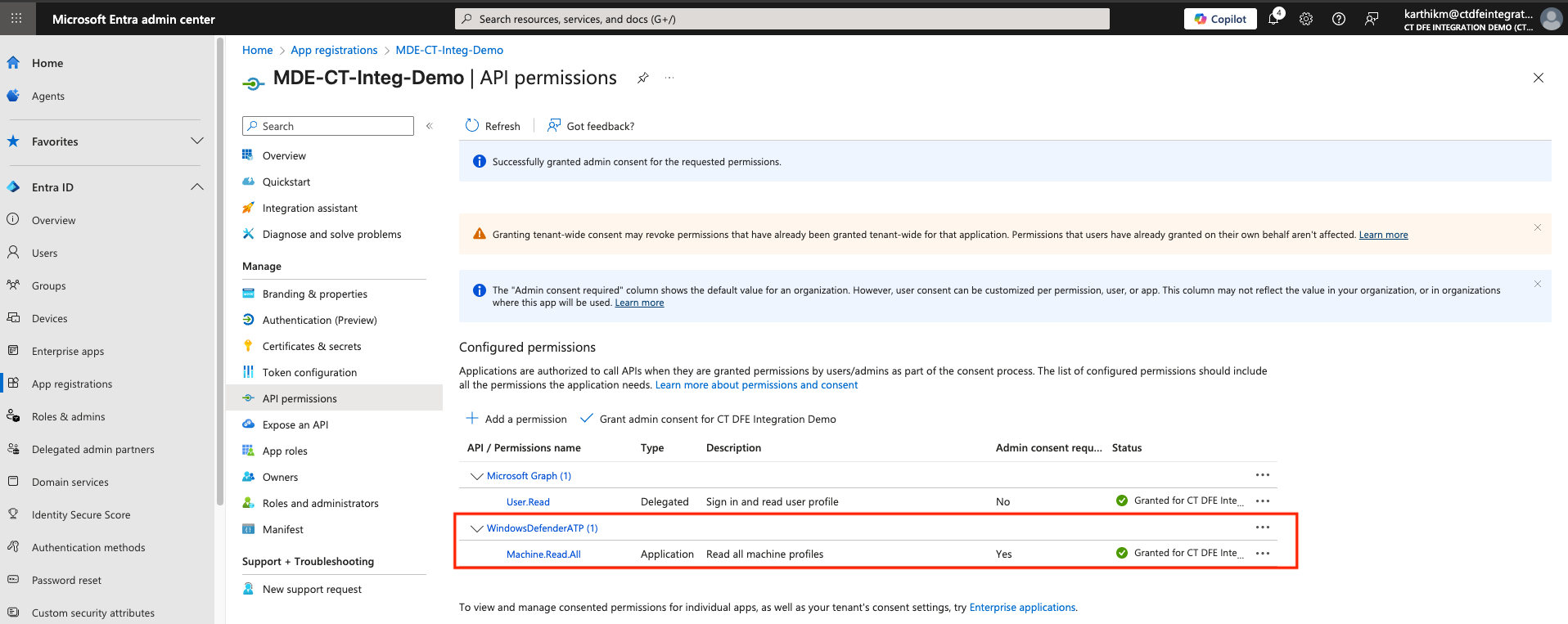
The registered application must be granted Machine.Read.All permission to allow the Xshield platform to make required API calls.
-
Go to API permissions in the Applications page
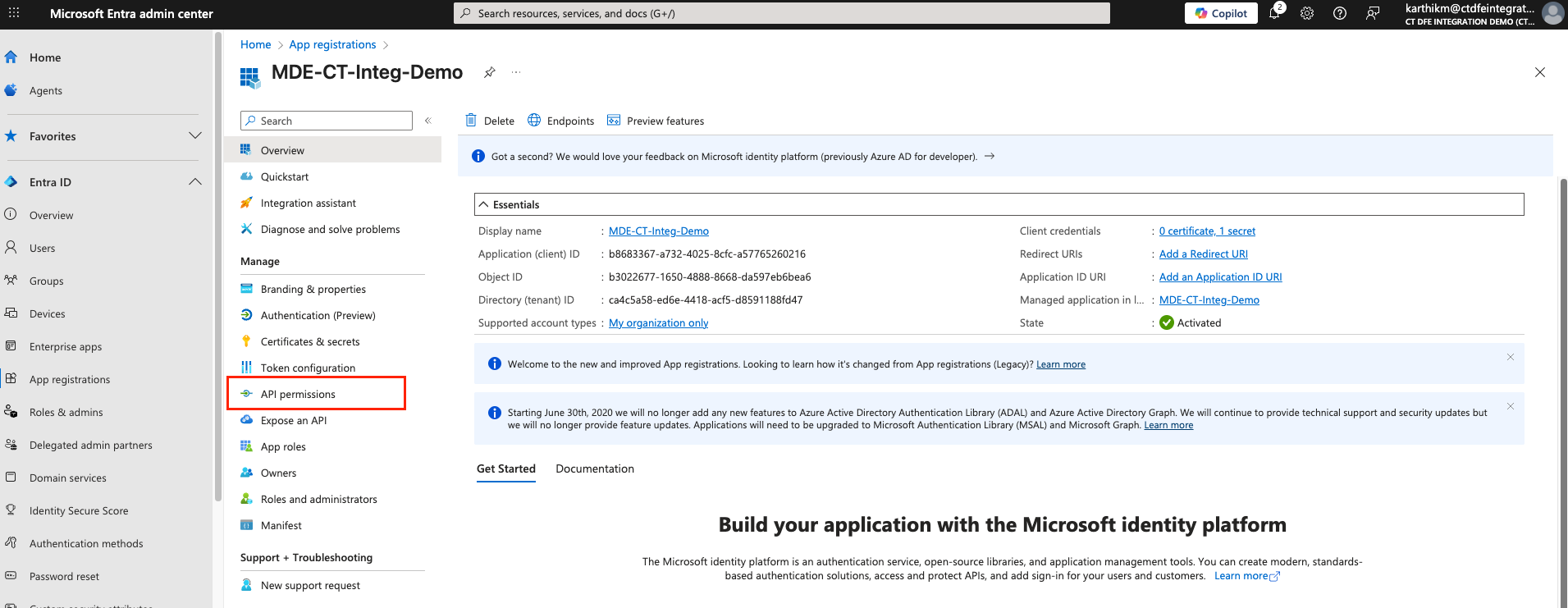
-
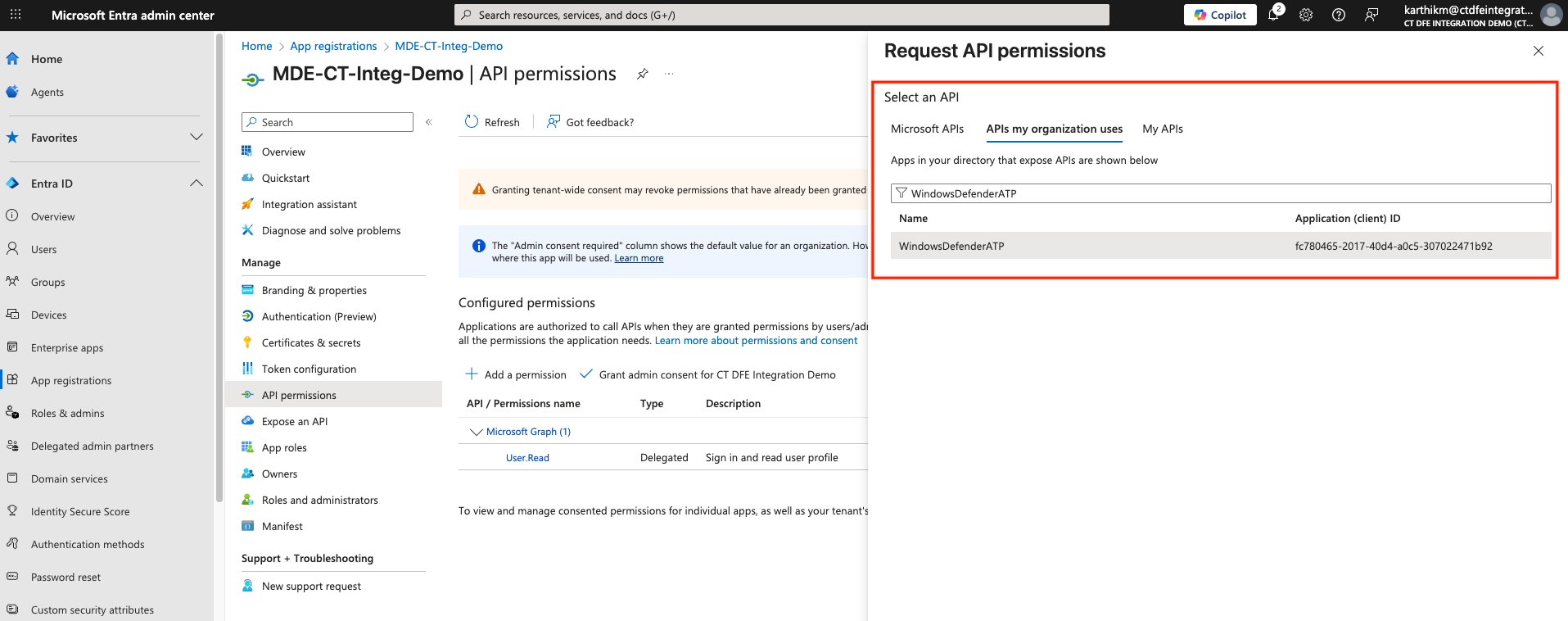
Click Add a permission > APIs my organization uses > Search for and add
WindowsDefenderATP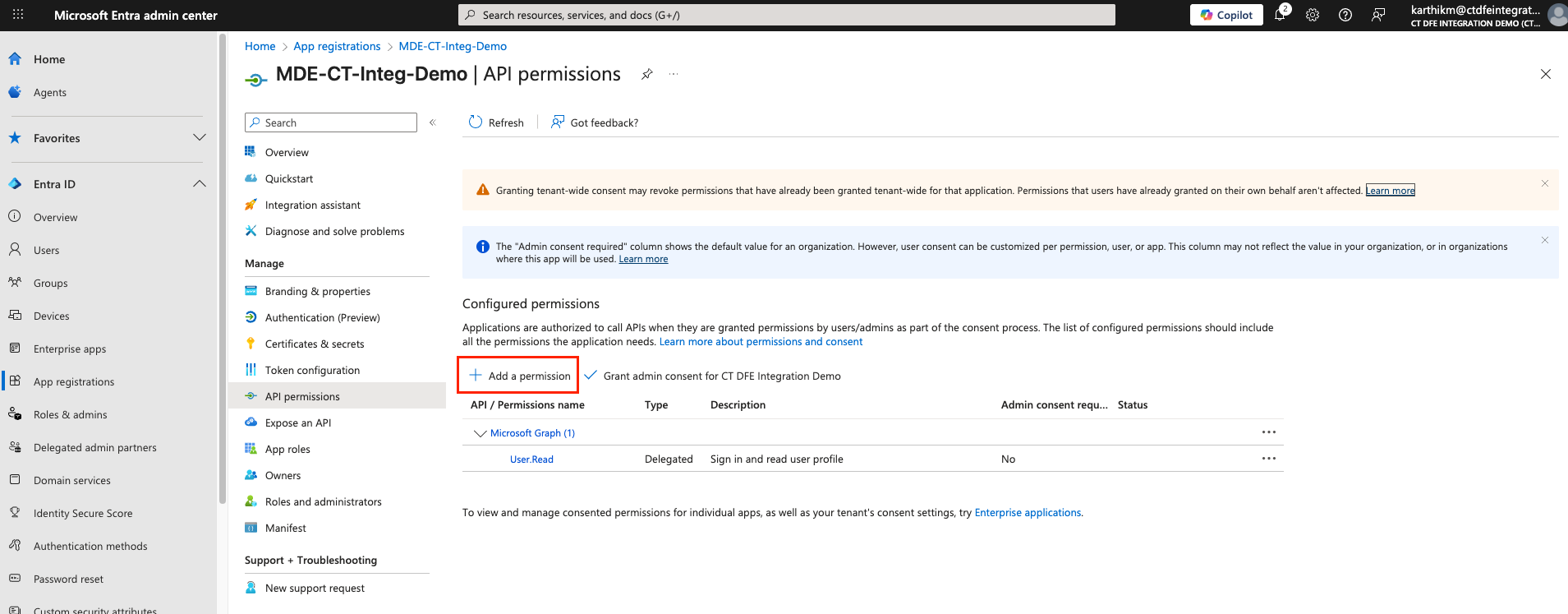
-
Select Application permissions
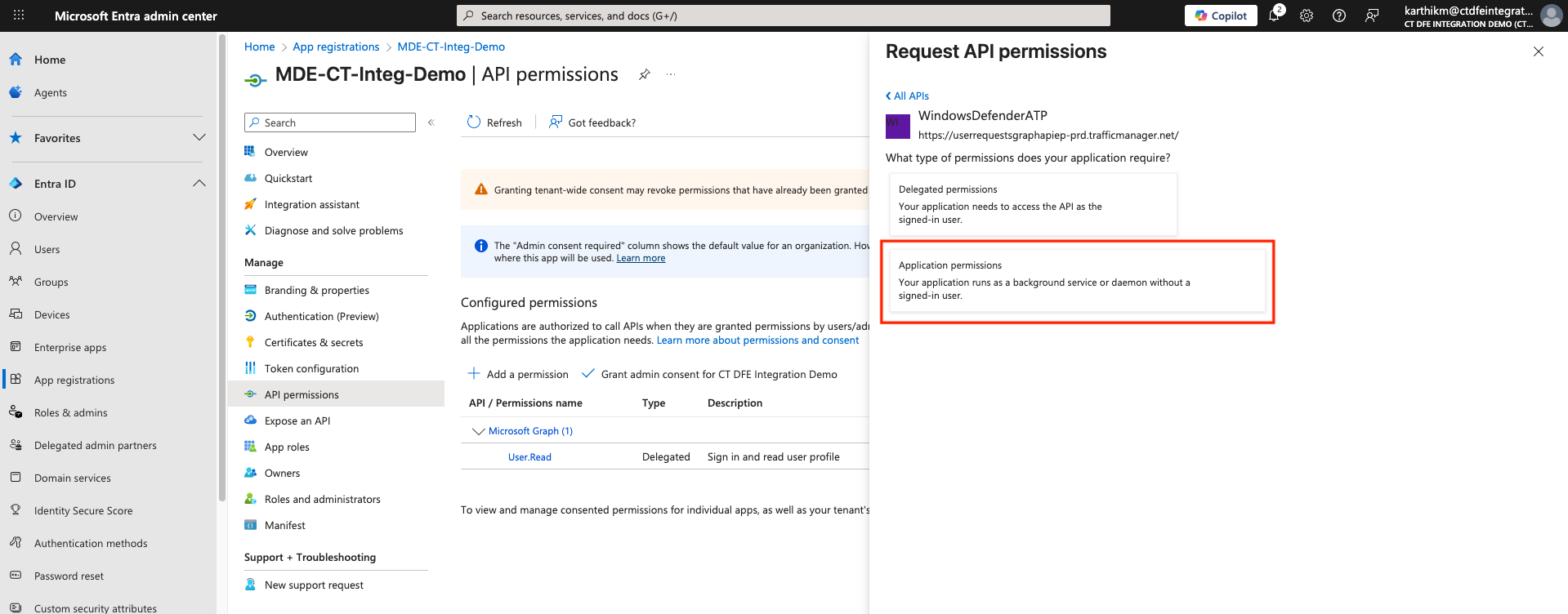
-
In the Request API Permissions panel, select
Machine.Read.All(under Machine section) and click Add permissions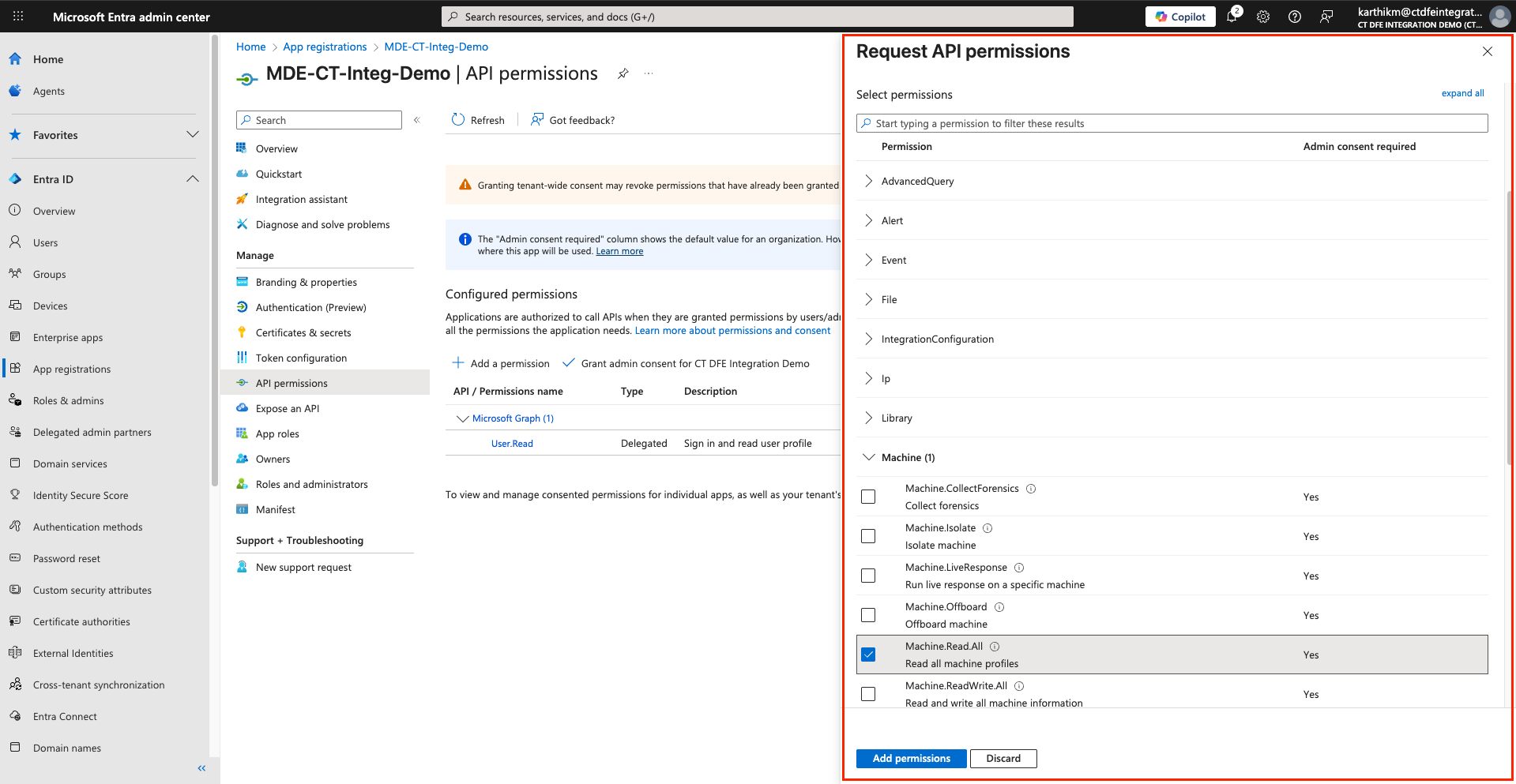
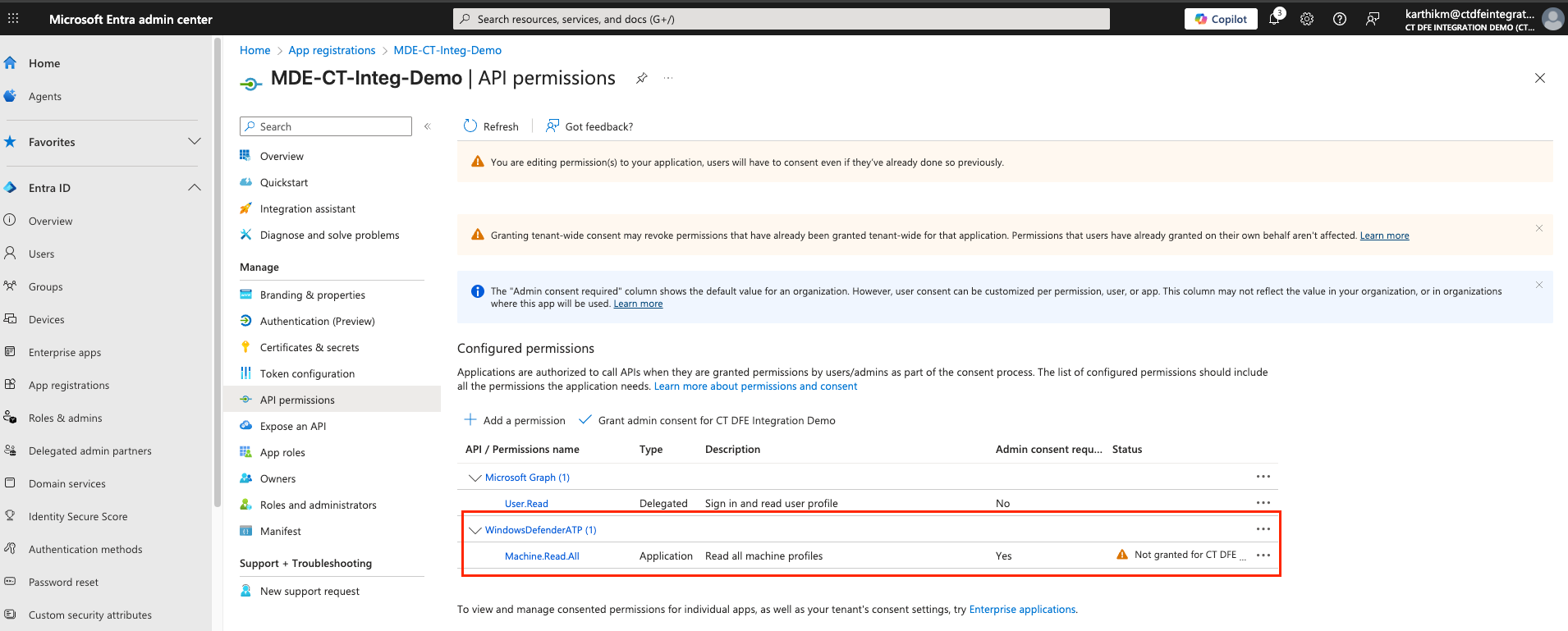
9. Grant access from ColorTokens SaaS platform to Storage Account
To enable the ColorTokens SaaS platform to retrieve network flow records from your Azure Storage Account, run the following command with the required parameters to authorize access.
az storage account network-rule add --resource-group "<storage-account-resource-group>" --account-name "<storage-account-name>" --subnet /subscriptions/<ColorTokens-Subscription>/resourceGroups/<ColorTokens-Resource-Group>/providers/Microsoft.Network/virtualNetworks/<ColorTokens VNET>/subnets/<ColorTokens-subnet>
Note: Please contact ColorTokens Support for ColorTokens subscription, resource group, vnet and subnet details.
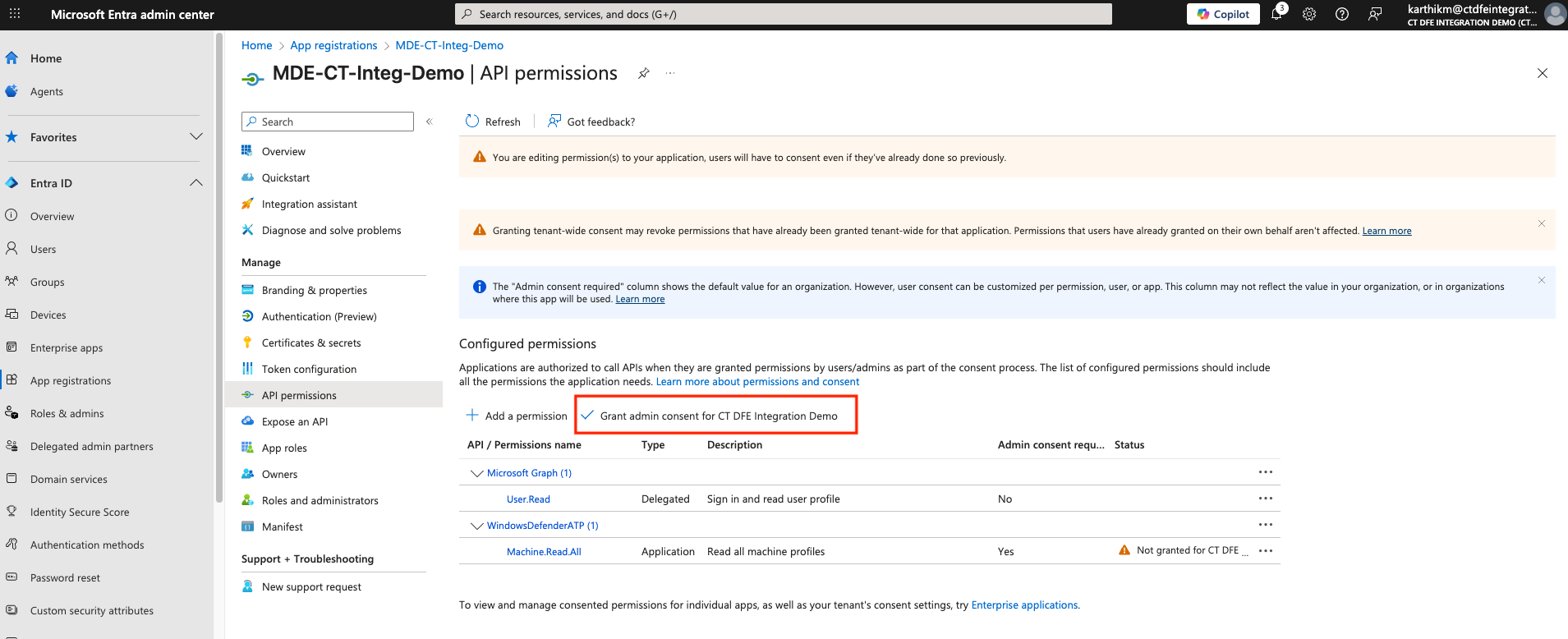
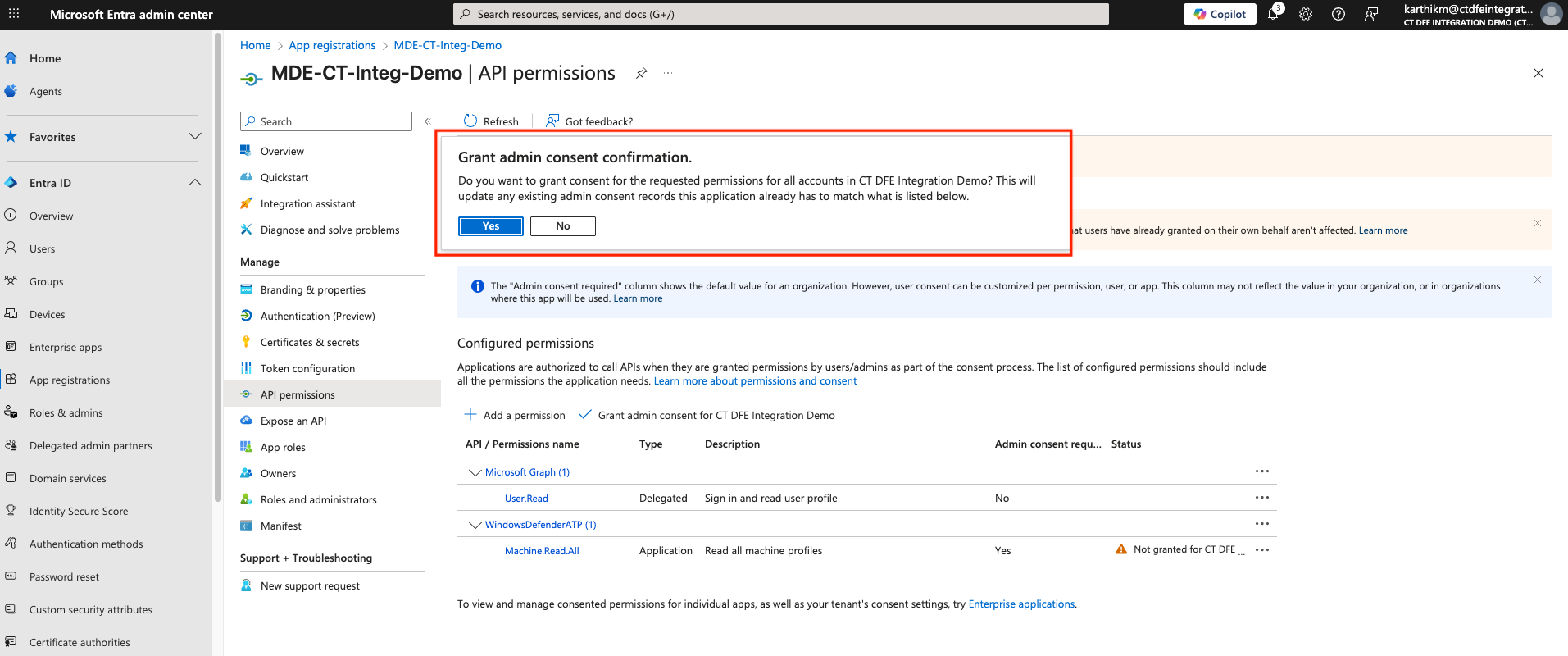
10. Activate Integration
Once the above steps are successful, you can Activate the Integration in Xshield
-
Admin must click Grant admin consent
Once the above steps are completed, you can proceed to Configure Storage Account and Storage Queue for Microsoft Defender for Endpoint
References and Support
- Register Entra Application Register Entra Application
- Create Client Secrets Create Client Secrets
- Streaming API Setup Streaming API Setup
- Event Subscription for Blob Notifications Event Subscription for Blob Notifications
For assistance, please contact ColorTokens Support.