Configure storage account and storage queue for Microsoft Defender for Endpoint
This document illustrates the steps required for setting up the storage account and a storage queue to configure the integration of Microsoft Defender for Endpoint with Xshield platform.
Summary Table
| Step Name | Purpose of this Step |
|---|---|
| Create Storage Account | Acts as the destination where Defender will send raw telemetry events like DeviceNetworkEvents. |
| Create Storage Queue | Queue stores event notifications (triggers) for new data blobs uploaded by Defender. |
| Configure Event Subscription | Automatically forwards notifications to the queue when new telemetry blobs are created in storage. |
| Assign IAM Role - Blob Data Reader | Allows the Entra application to read blobs from the storage account (for retrieving event data). |
| Assign IAM Role - Queue Message Processor | Allows Xshield (via the Entra app) to read and process messages from the queue (event triggers). |
| Retrieve Storage Account Resource ID | Needed to configure Defender’s Streaming API and tie it to the correct storage account. |
| Setup Defender Streaming API | Ensures only DeviceNetworkEvents are exported to blob storage for network visibility in Xshield. |
ColorTokens provides a terraform script to automate the manual steps outlined in this document. To use the terraform script, please follow the instructions in the Generate API Credentials for Integrating Microsoft Defender for Endpoint with Xshield platform using Terraform document
1. Create Storage Account, Storage Queue and Event Subscription
Follow the below steps to set up Storage Account, Storage Queue and Event Subscription:
1.1 Setup Storage Account
A storage account is required to receive network events from MDE
-
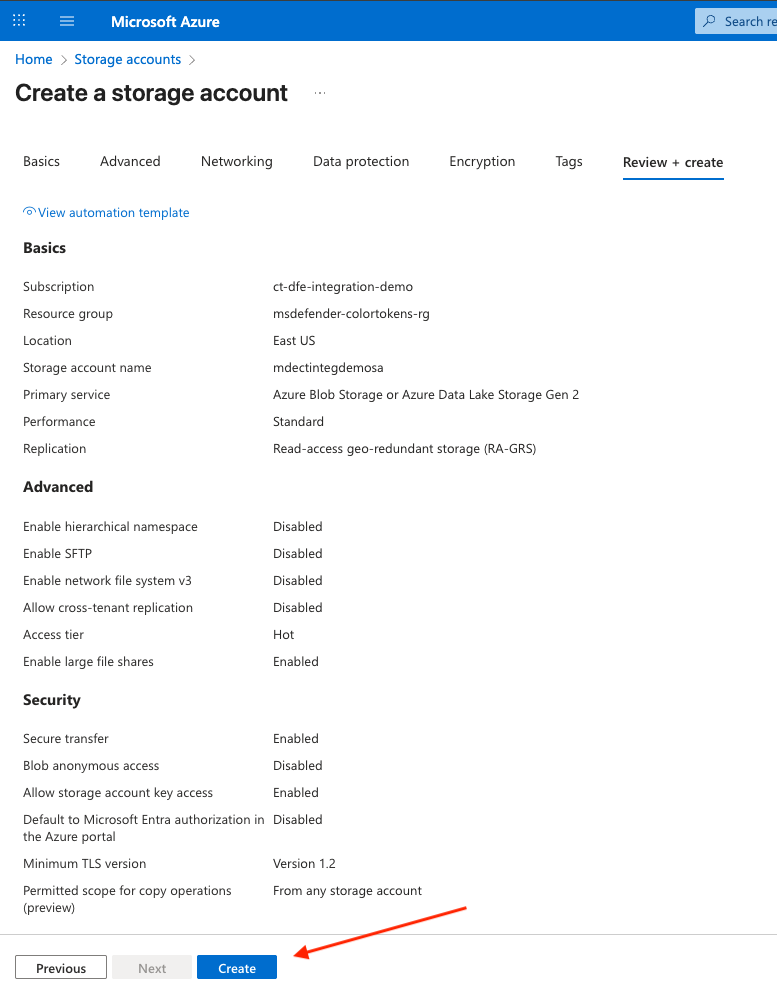
Go to Storage Accounts > Create
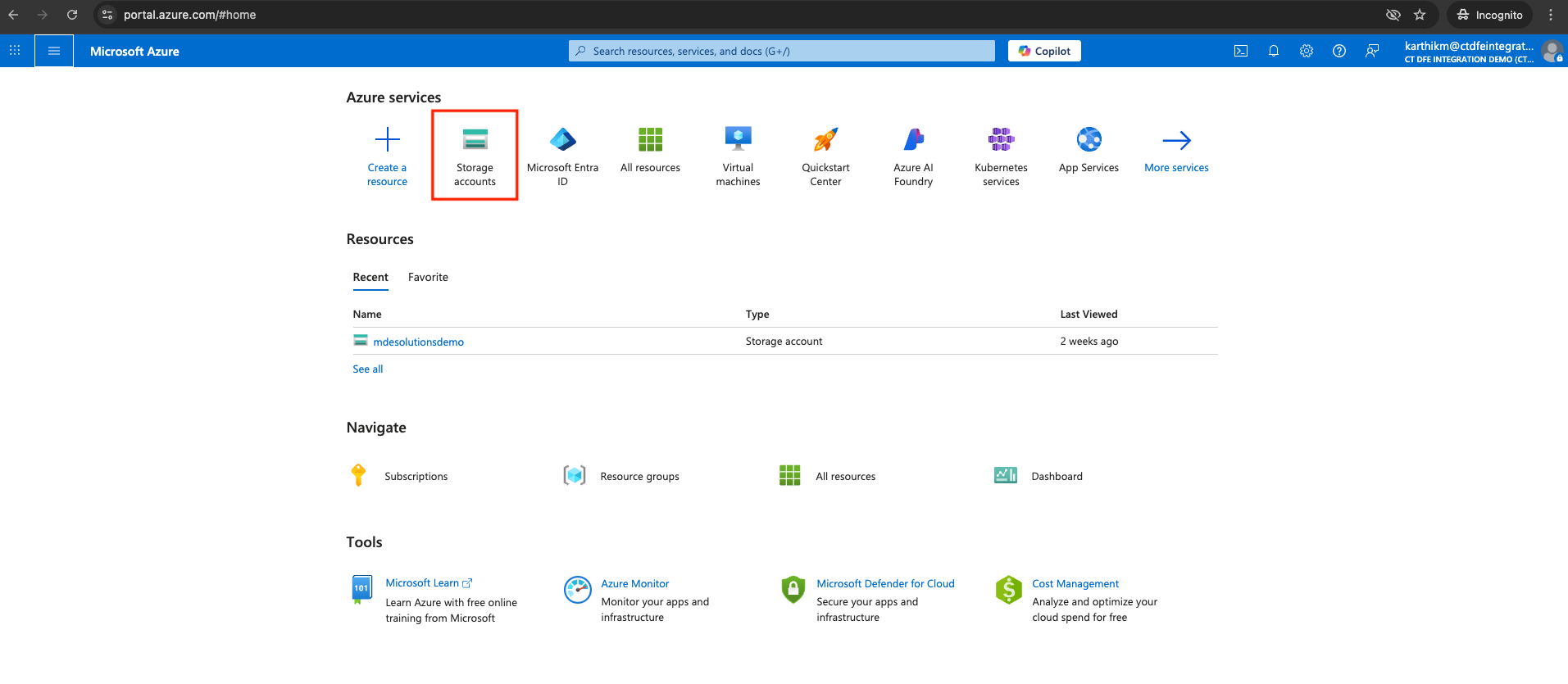
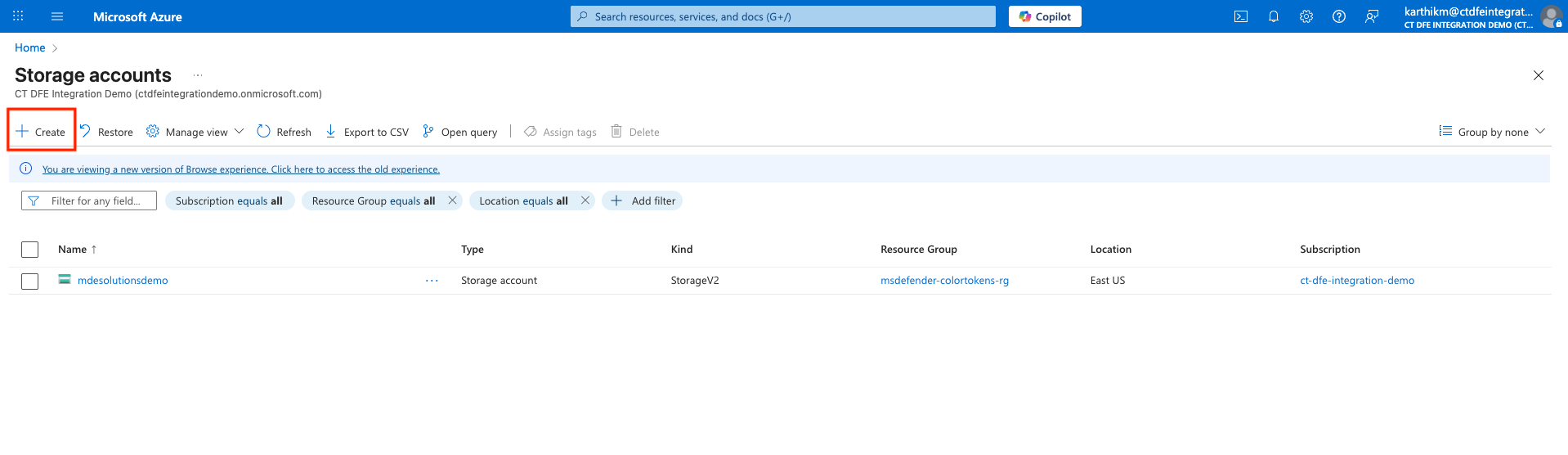
-
Provide a name for the storage account, select the subscription and resource group
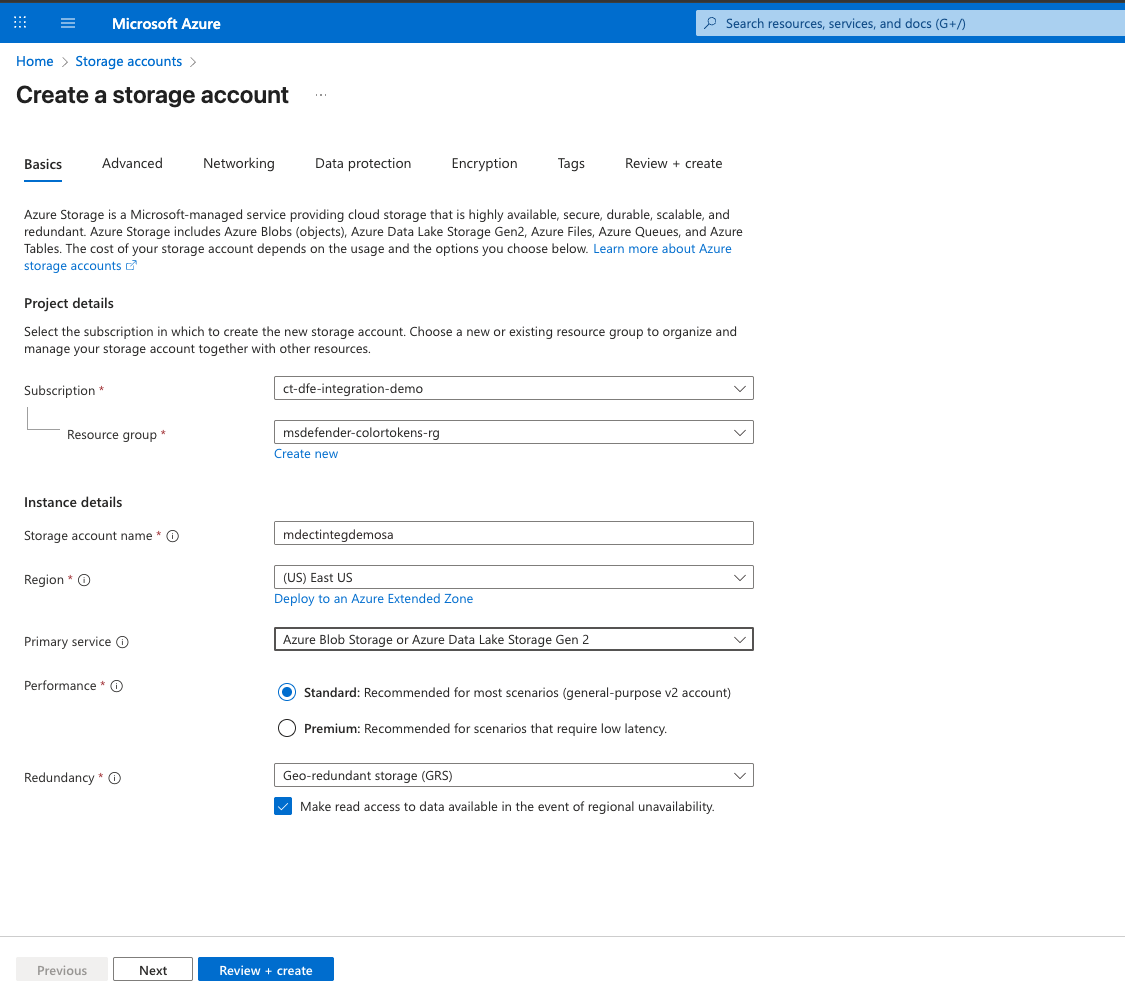
-
Go to the network tab, for Public network access, select Disable . To enable access from Xshield Platform to the storage account, continue with the next steps.
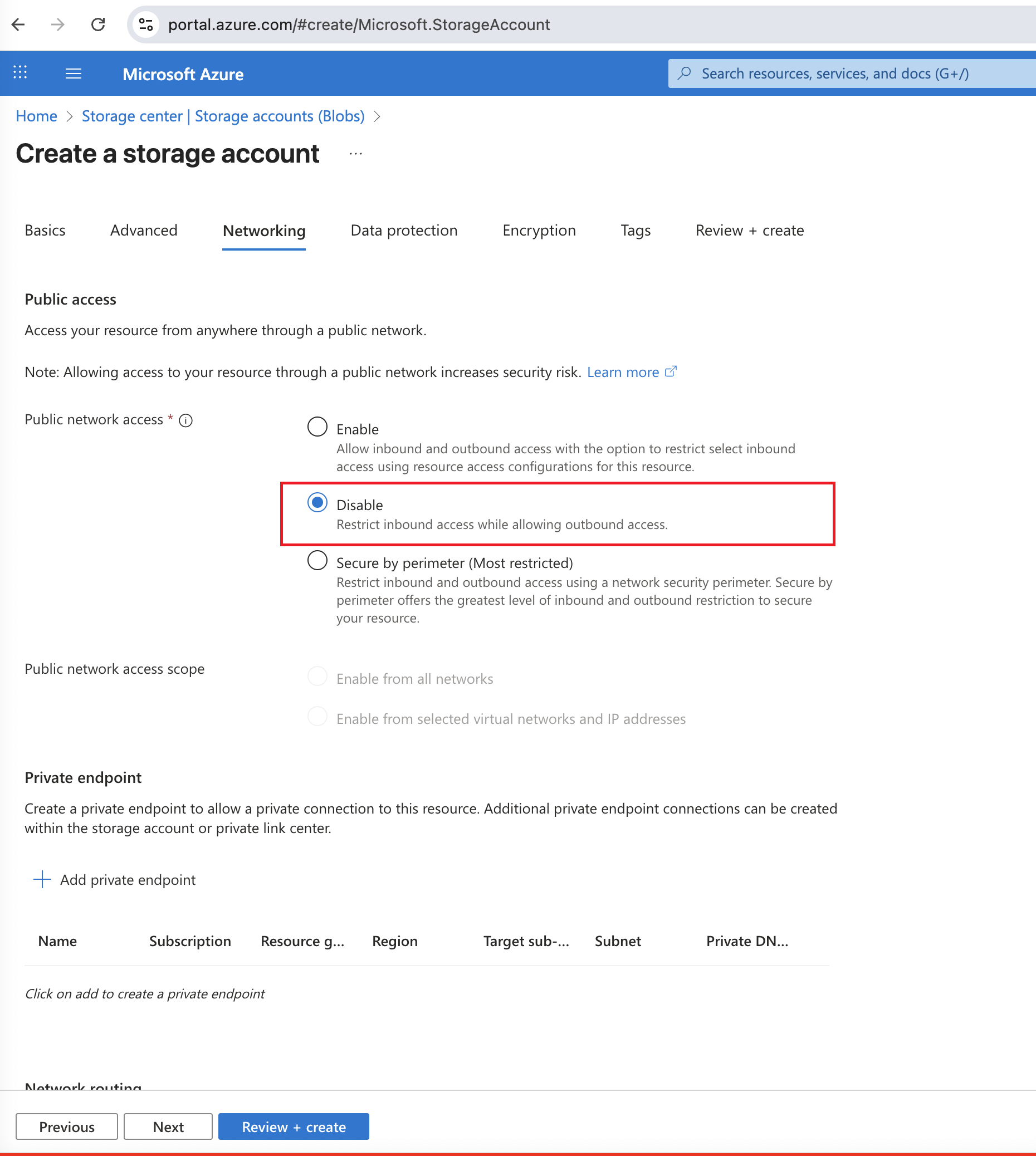
-
Click Review + create and then Create
-
Enable access from ColorTokens SaaS platform to your Azure Storage Account, run the following command with the required parameters to authorize access.
az storage account network-rule add --resource-group "<storage-account-resource-group>" --account-name "<storage-account-name>" --subnet /subscriptions/<ColorTokens-Subscription>/resourceGroups/<ColorTokens-Resource-Group>/providers/Microsoft.Network/virtualNetworks/<ColorTokens VNET>/subnets/<ColorTokens-subnet>
⚠️ Note: Please contact ColorTokens Support for ColorTokens subscription, resource group, vnet and subnet details.
1.2 Setup Storage Queue
Set up a queue in the storage account to capture and store incoming MDE network events.
-
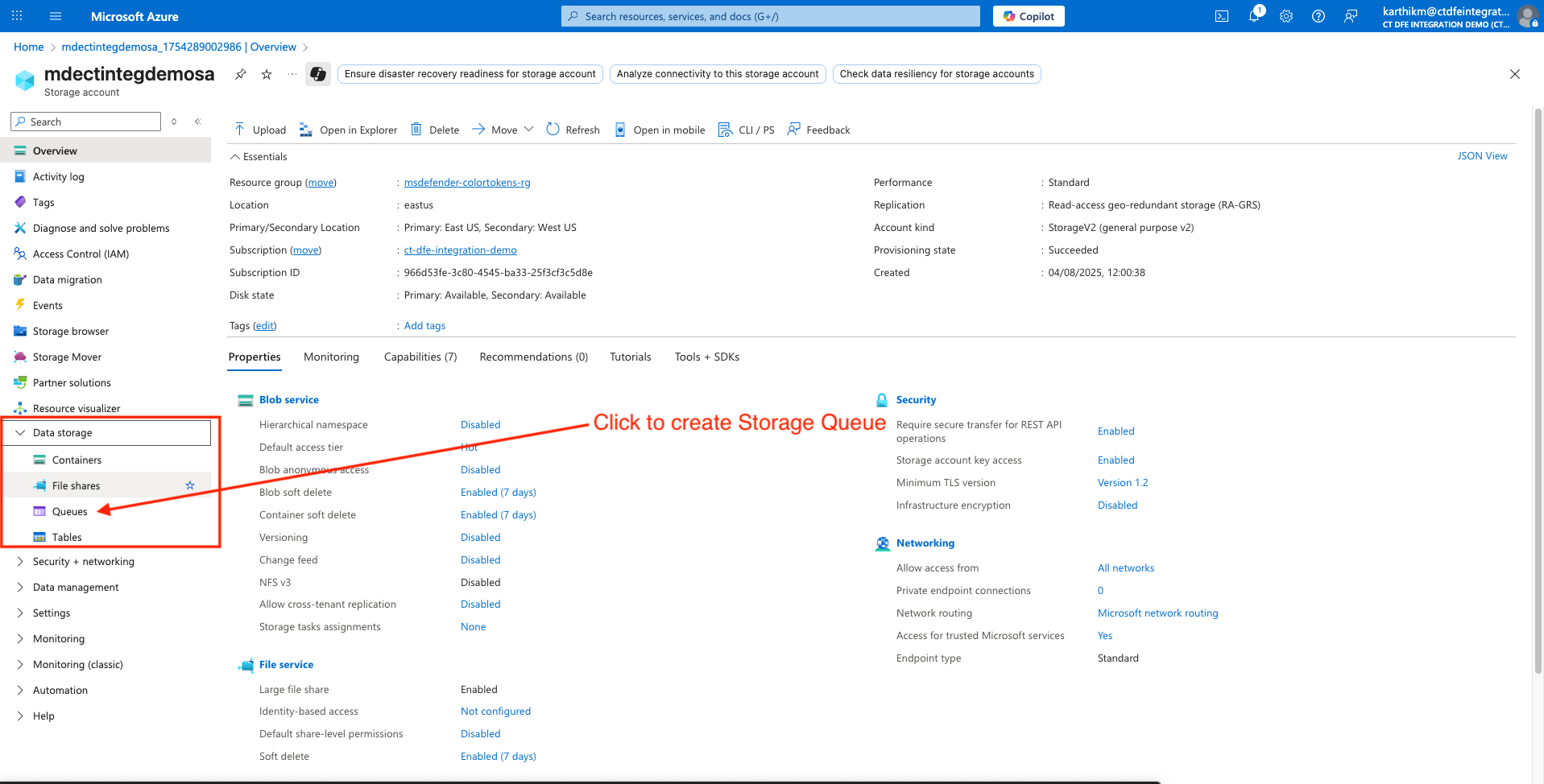
Go to Storage Accounts > Storage Account Name > Data storage > Queues
-
Click +Queue
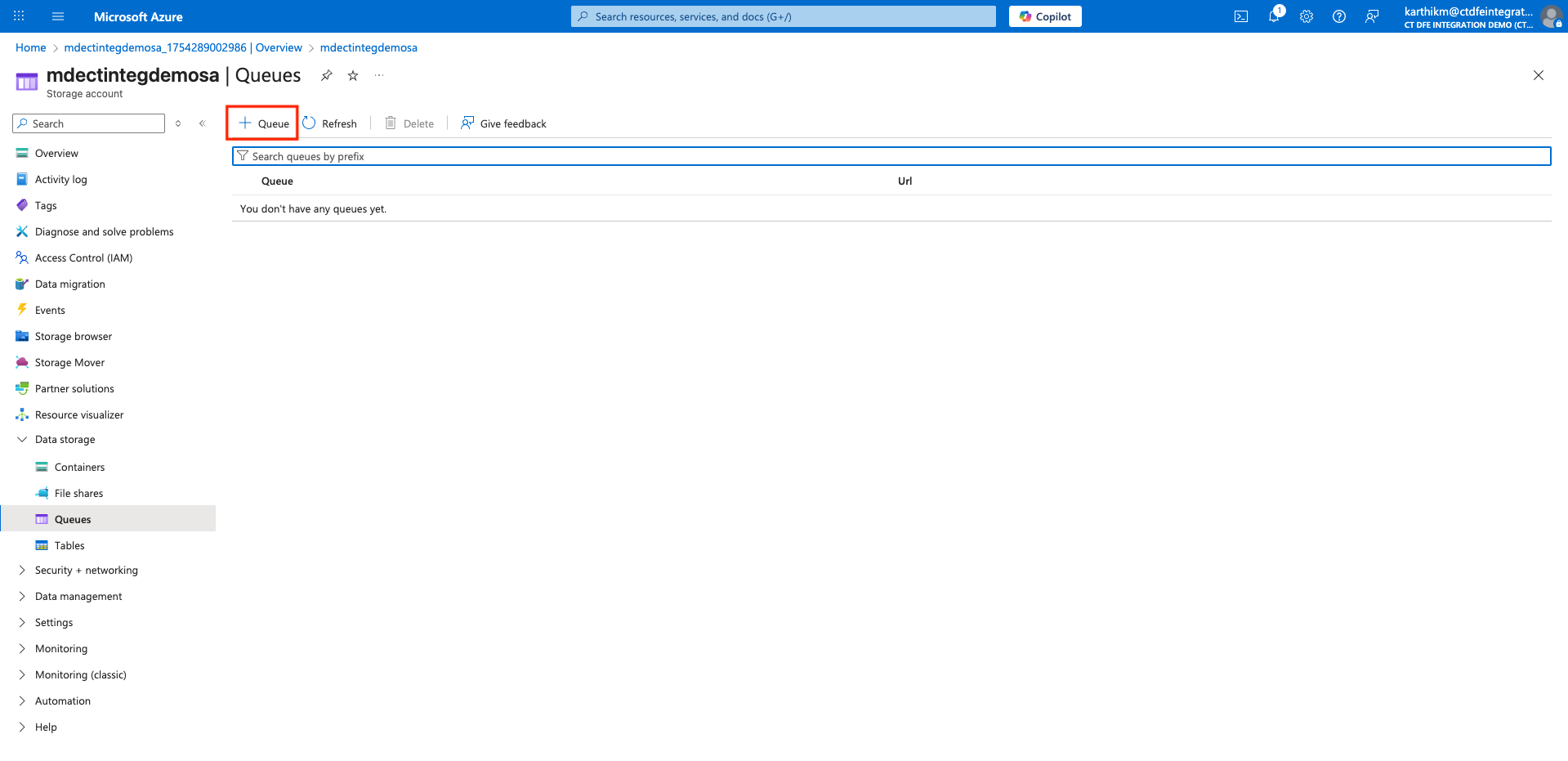
-
Provide a name for the queue and click OK
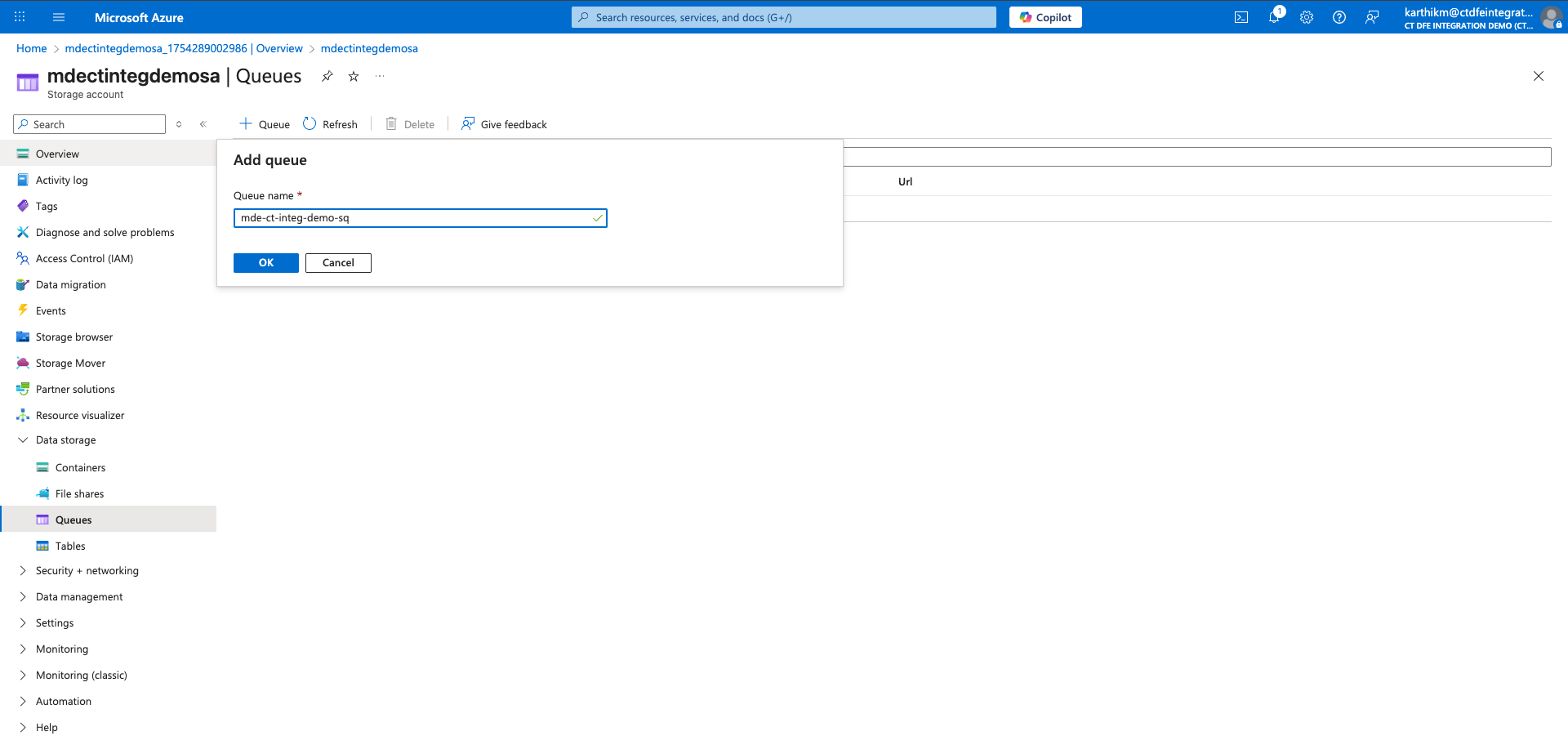
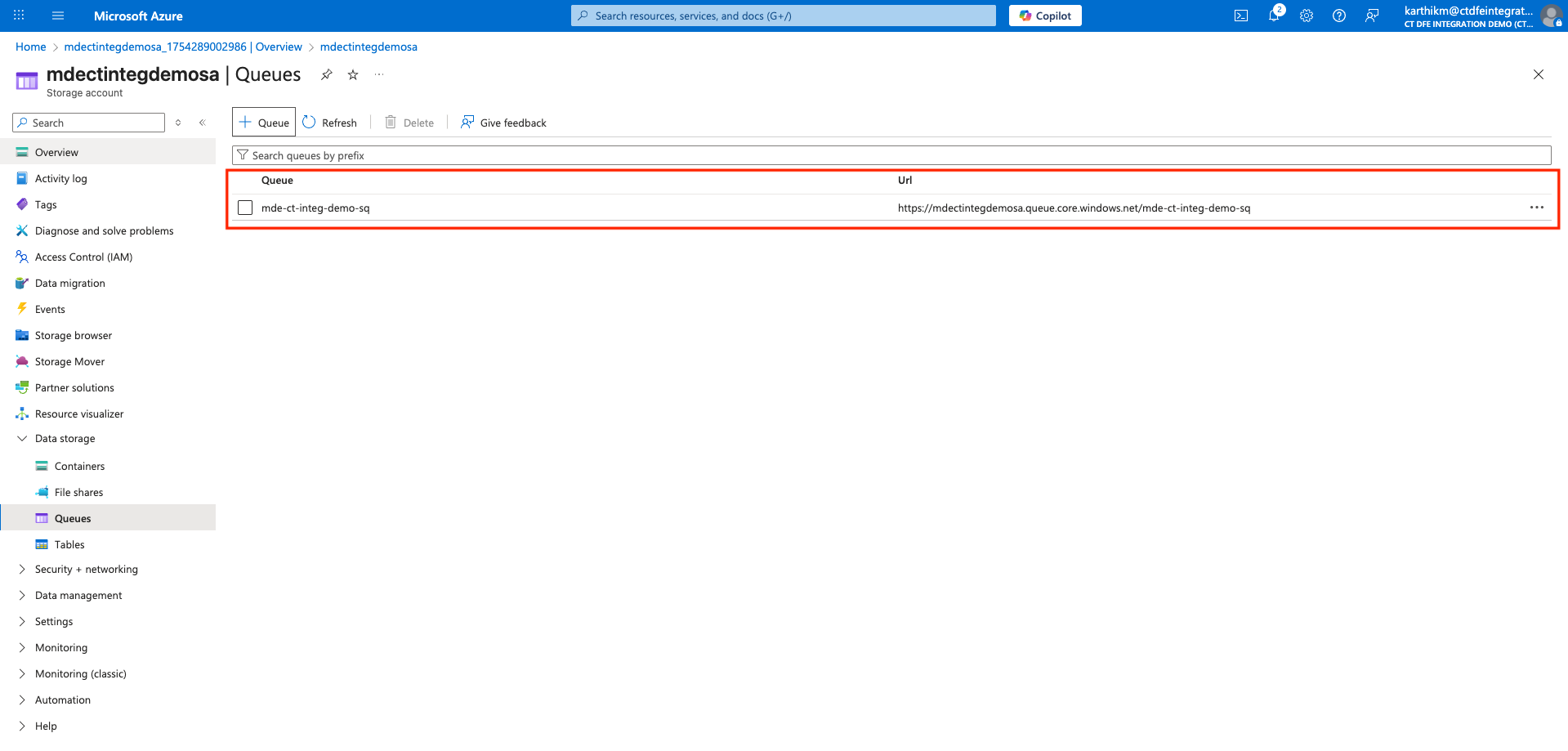
Storage Account name & Storage Queue name is required to configure the integration in Xshield Platform. Please note these down.
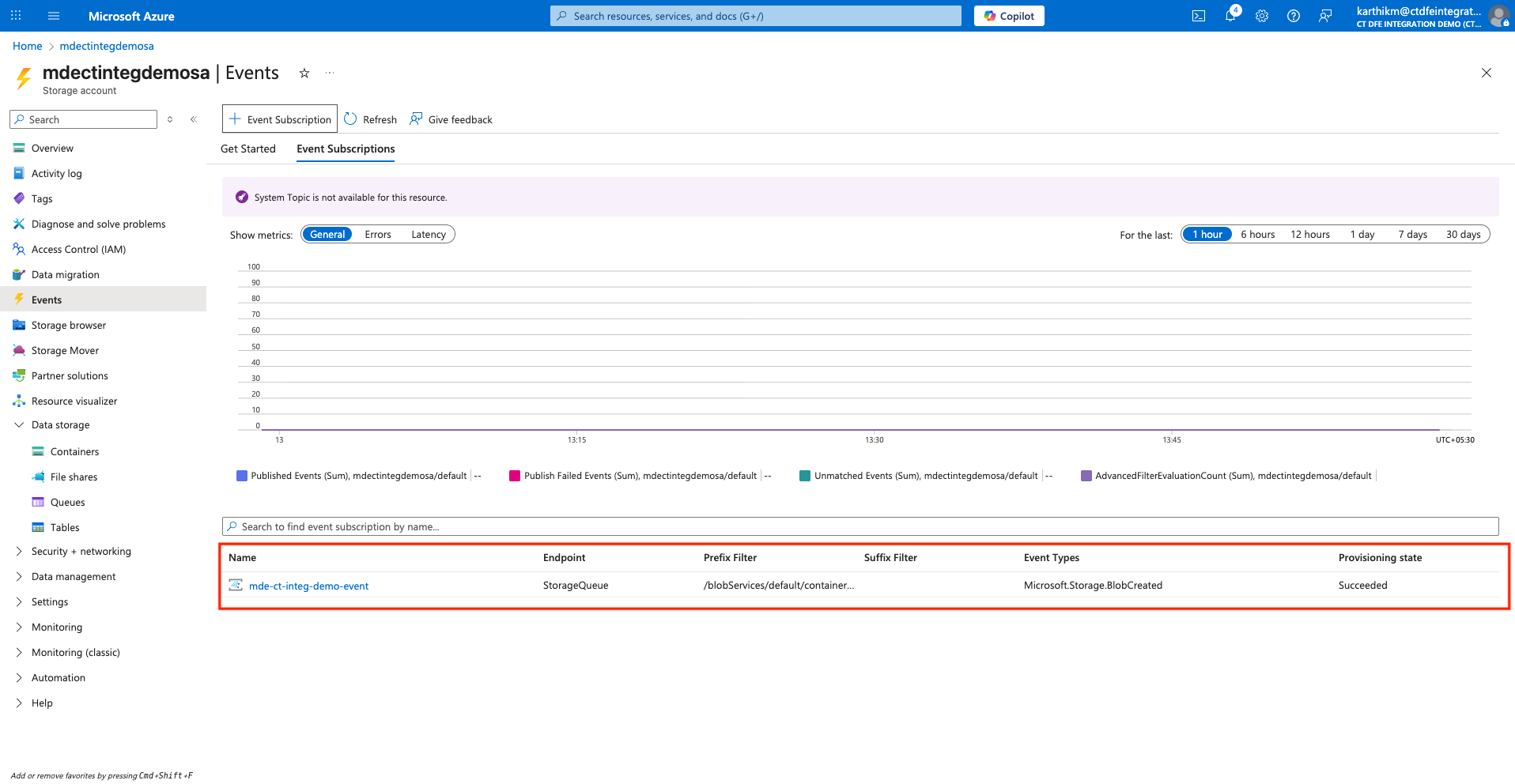
1.3 Create Event Subscription for Blob Notifications
Configure Event Subscription on the storage account with Endpoint Type - Storage Queue to notify Xshield about new blob creation events.
-
Go to Storage Account > Events > + Event Subscription
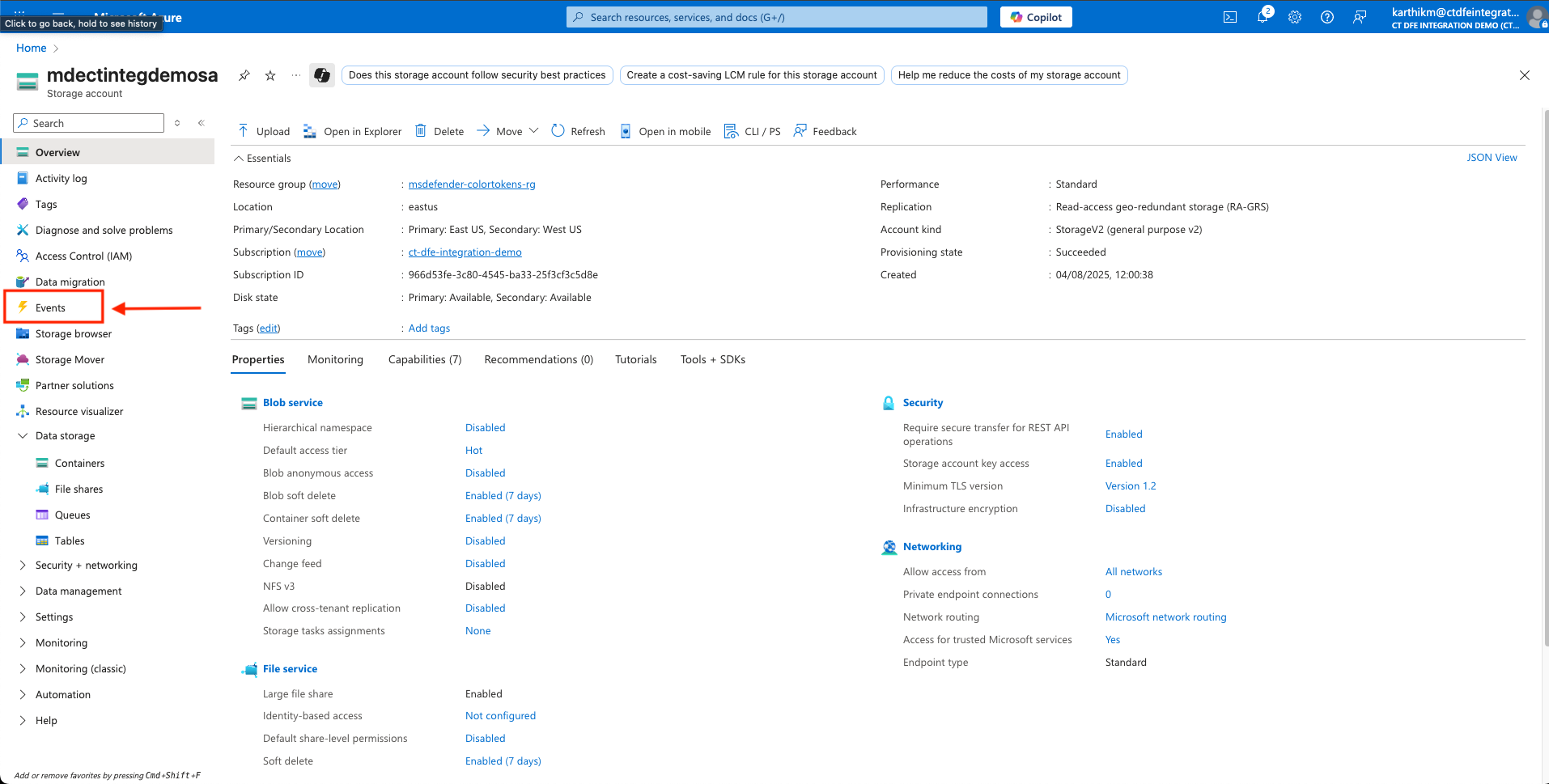
-
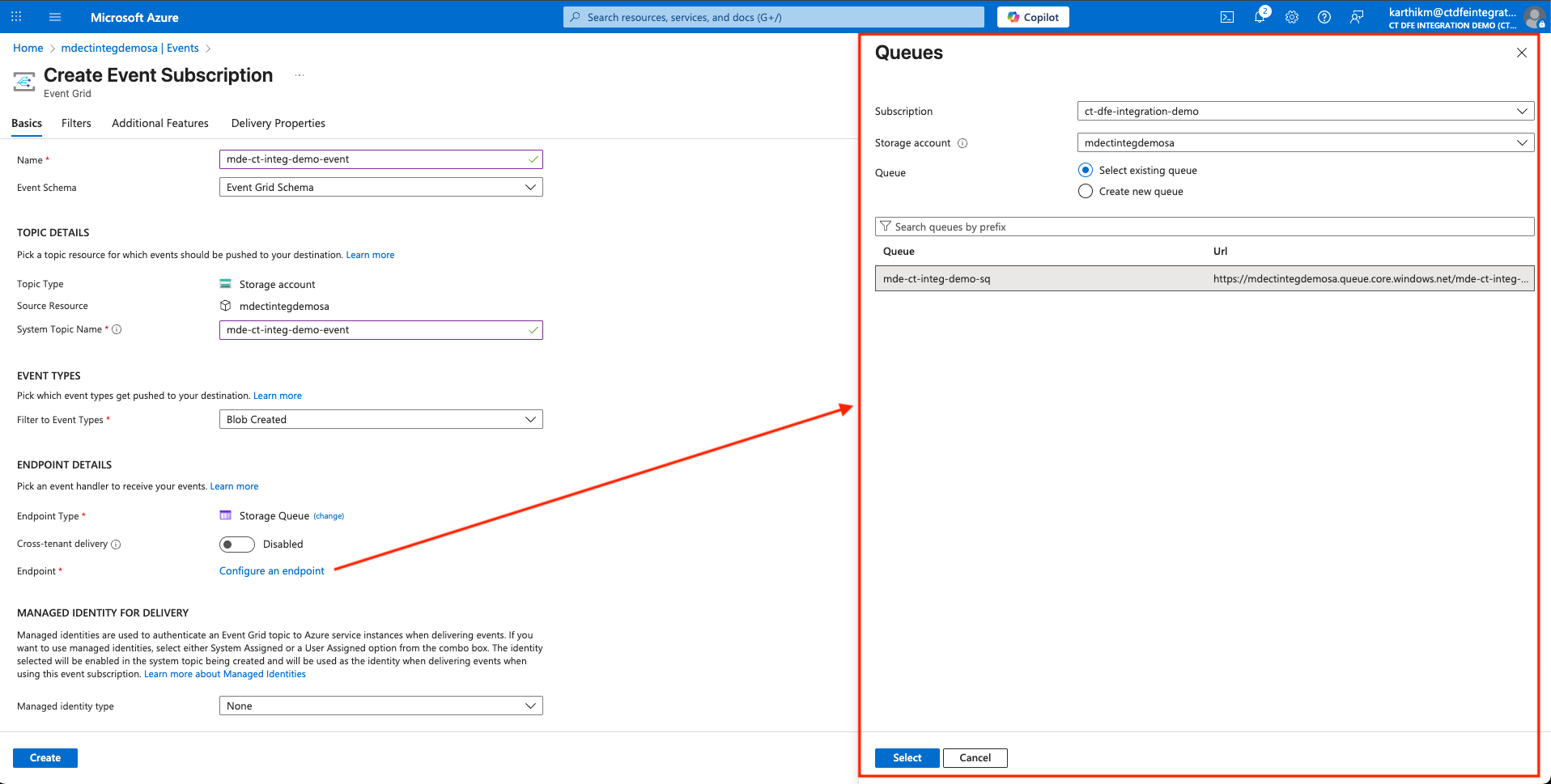
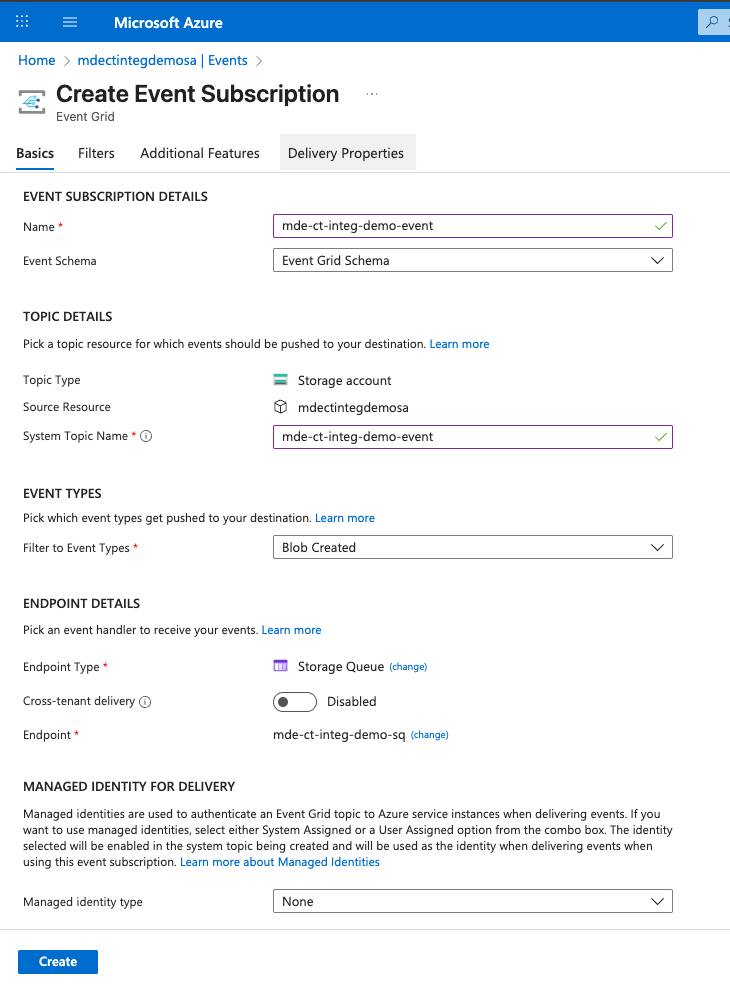
In the Basics tab:
- Provide a Name for the event subscription and System Topic Name
- Under Filter to Event Types in the EVENT TYPES section, select only Blob Created
- Select Storage Queue as the Endpoint type to send a notification to the storage queue when a blob is created
- Click on Configure an Endpoint and select the storage queue created in the previous step
-
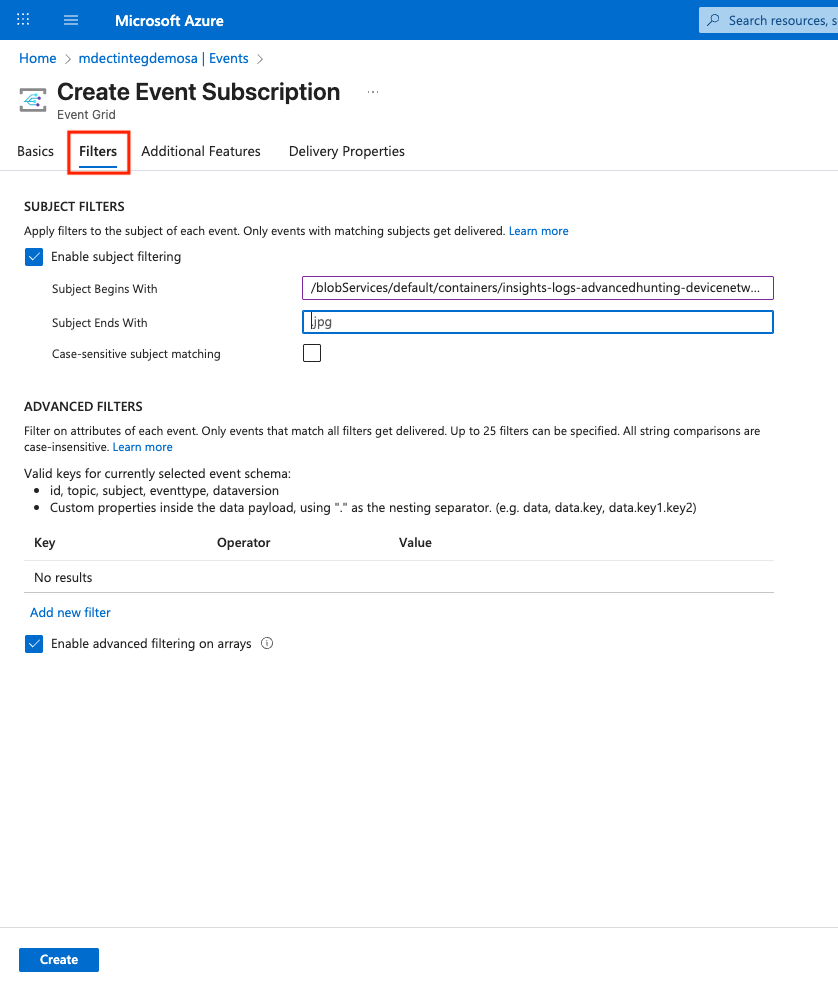
In the Filters tab: To raise notification events only when blobs are created in the container
insights-logs-advancedhunting-devicenetworkevents:- Enable Enable subject filtering
- Set Subject Begins With to:
/blobServices/default/containers/insights-logs-advancedhunting-devicenetworkevents/
-
Finally, click on the Create button to create the Event Subscription
2. Assign IAM Roles to Entra Application
Grant the Entra application permission to access and read blob data from the storage account, enabling it to retrieve event-related information as needed
2.1 Storage Account Access
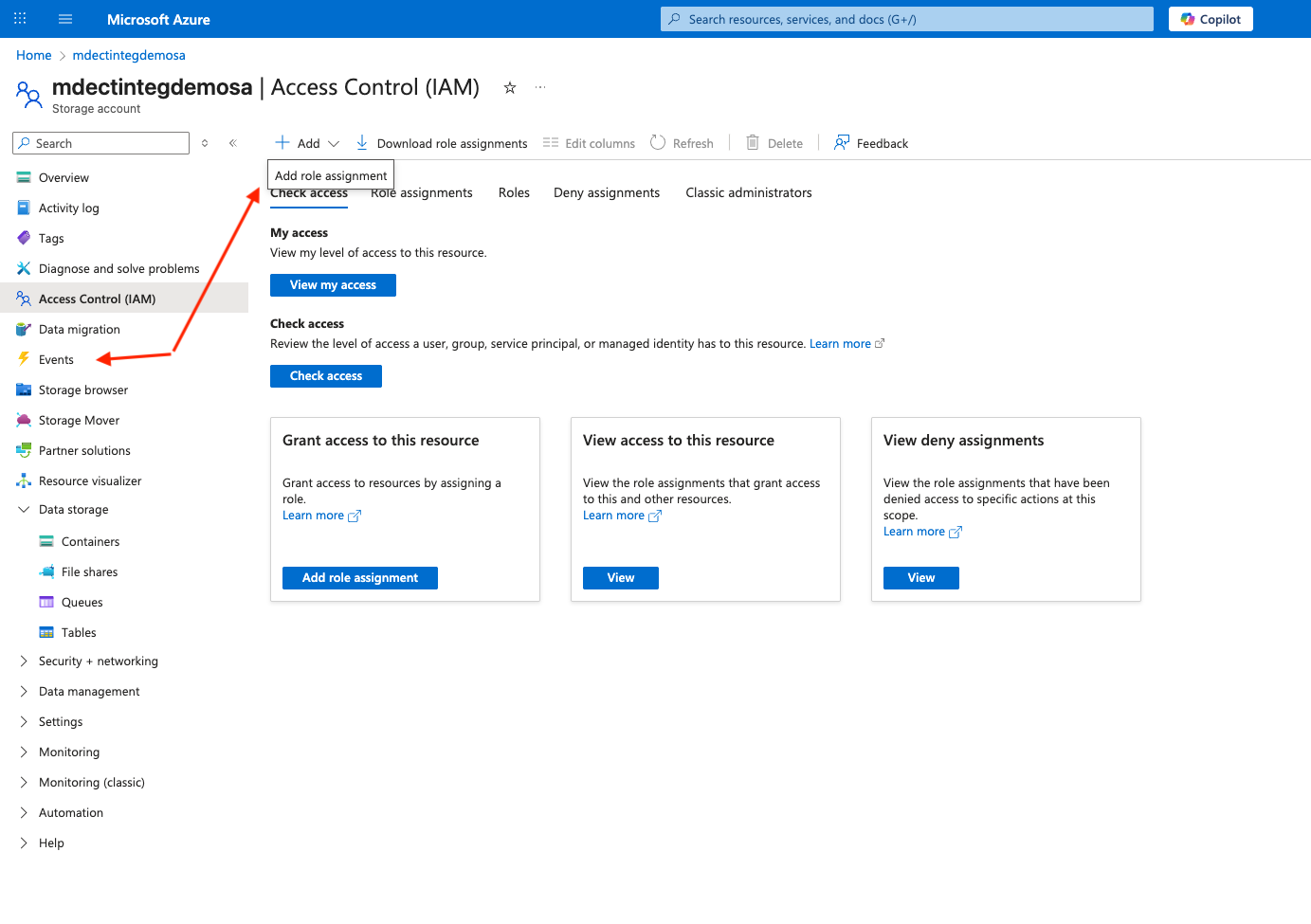
-
Go to Storage Account > Events > +Add > Add role assignment
-
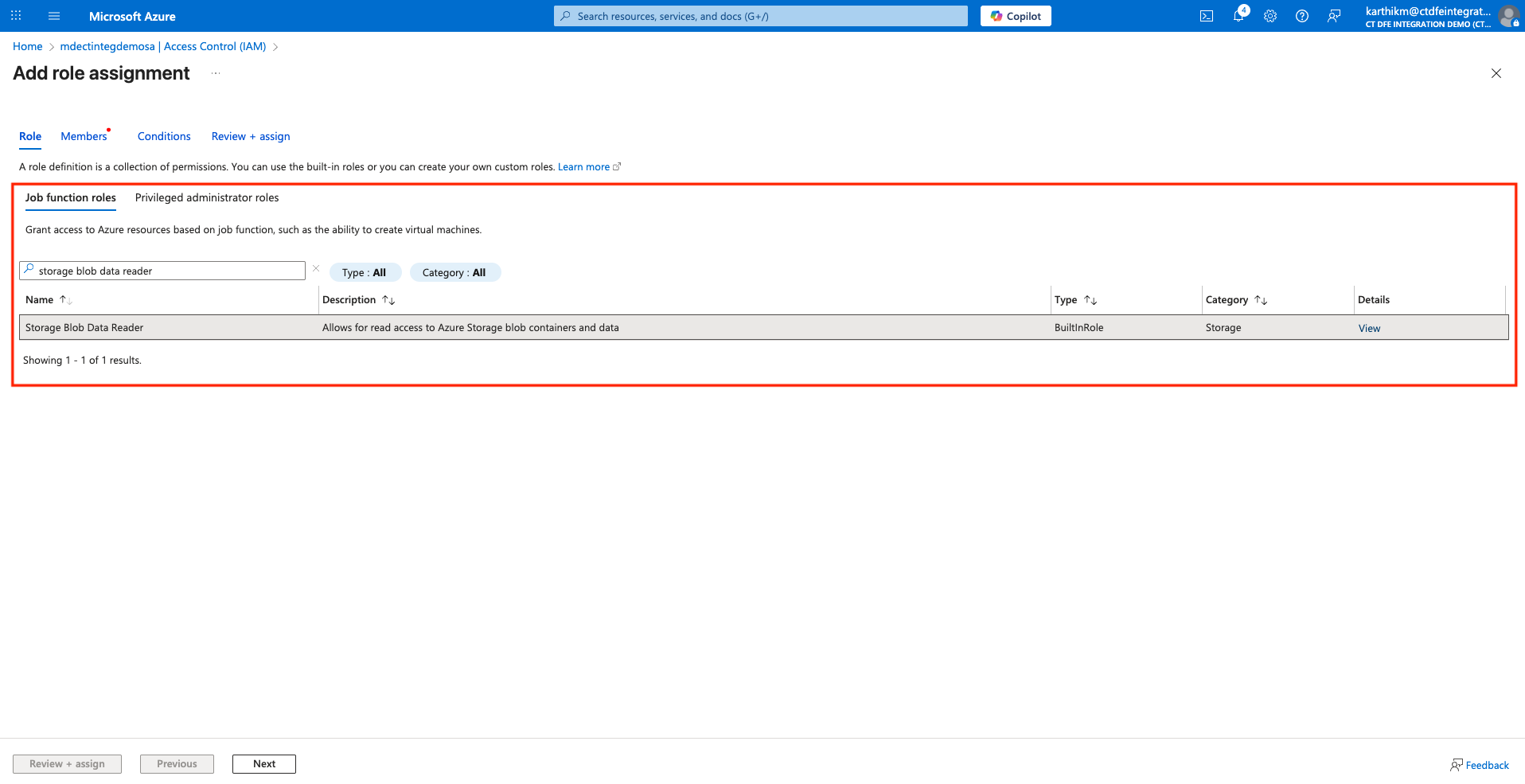
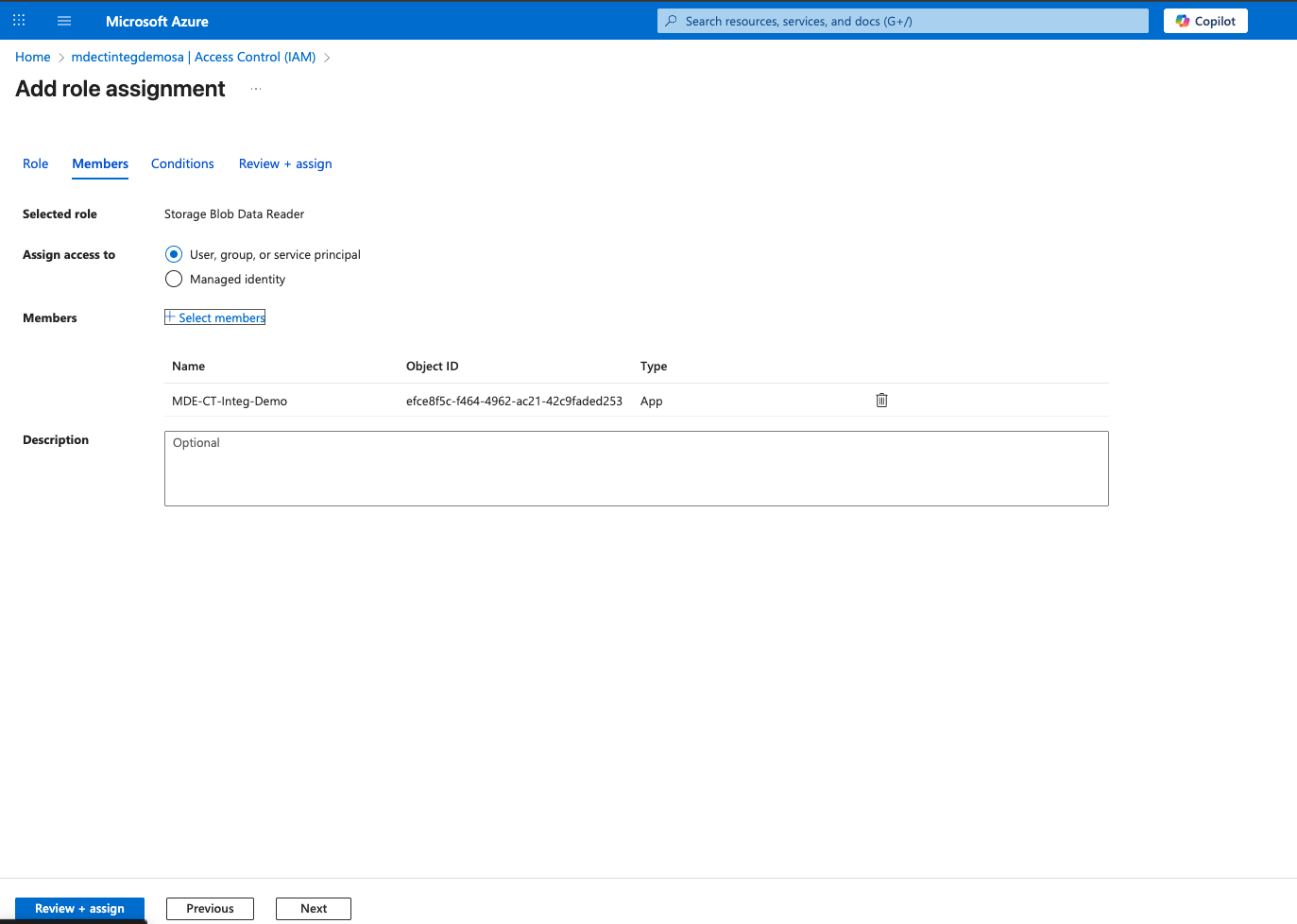
Under Role > Job function roles, select Storage Blob Data Reader
-
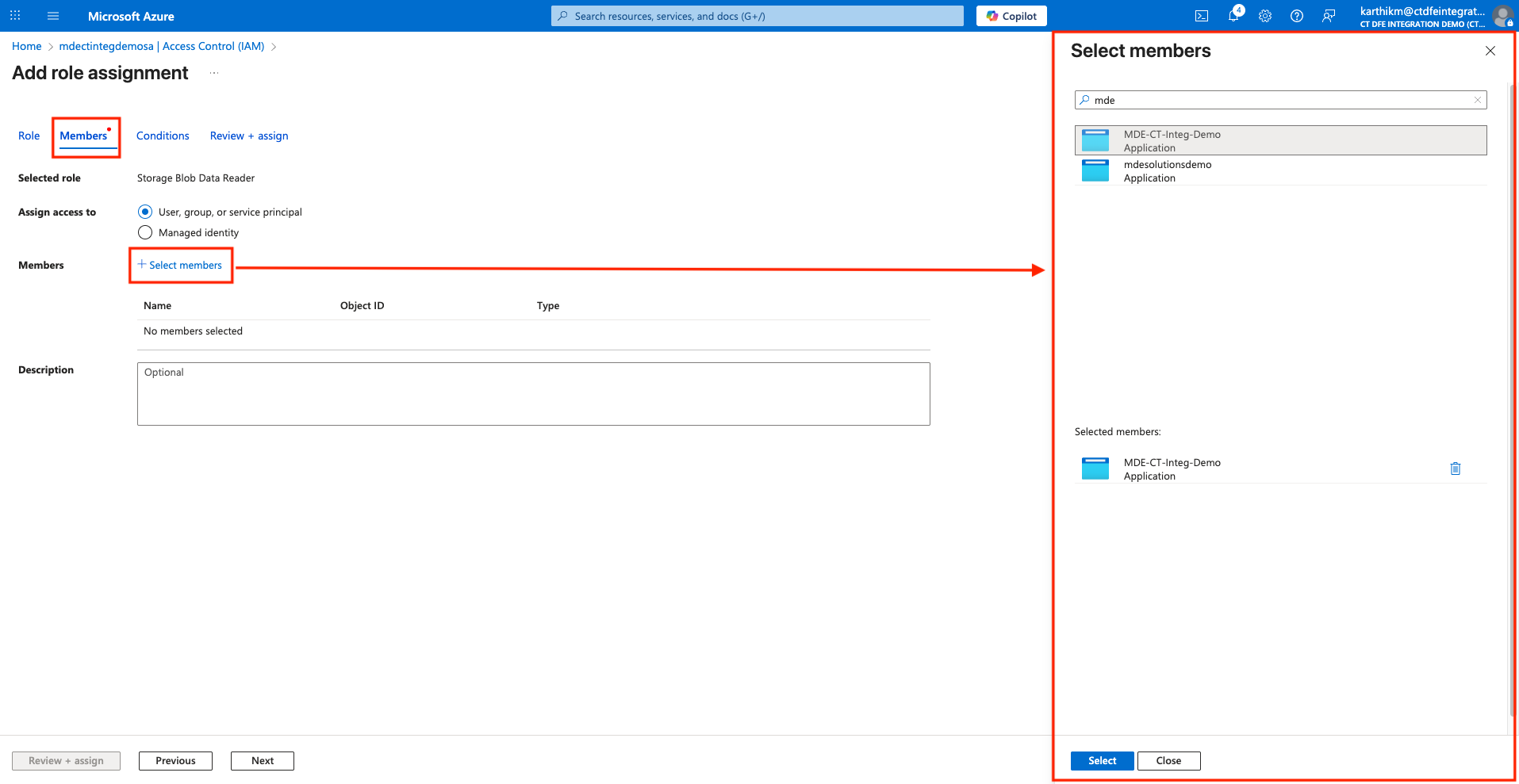
Under Members tab, select on +Select members, and type your Entra ID application name under Select members and click Select
-
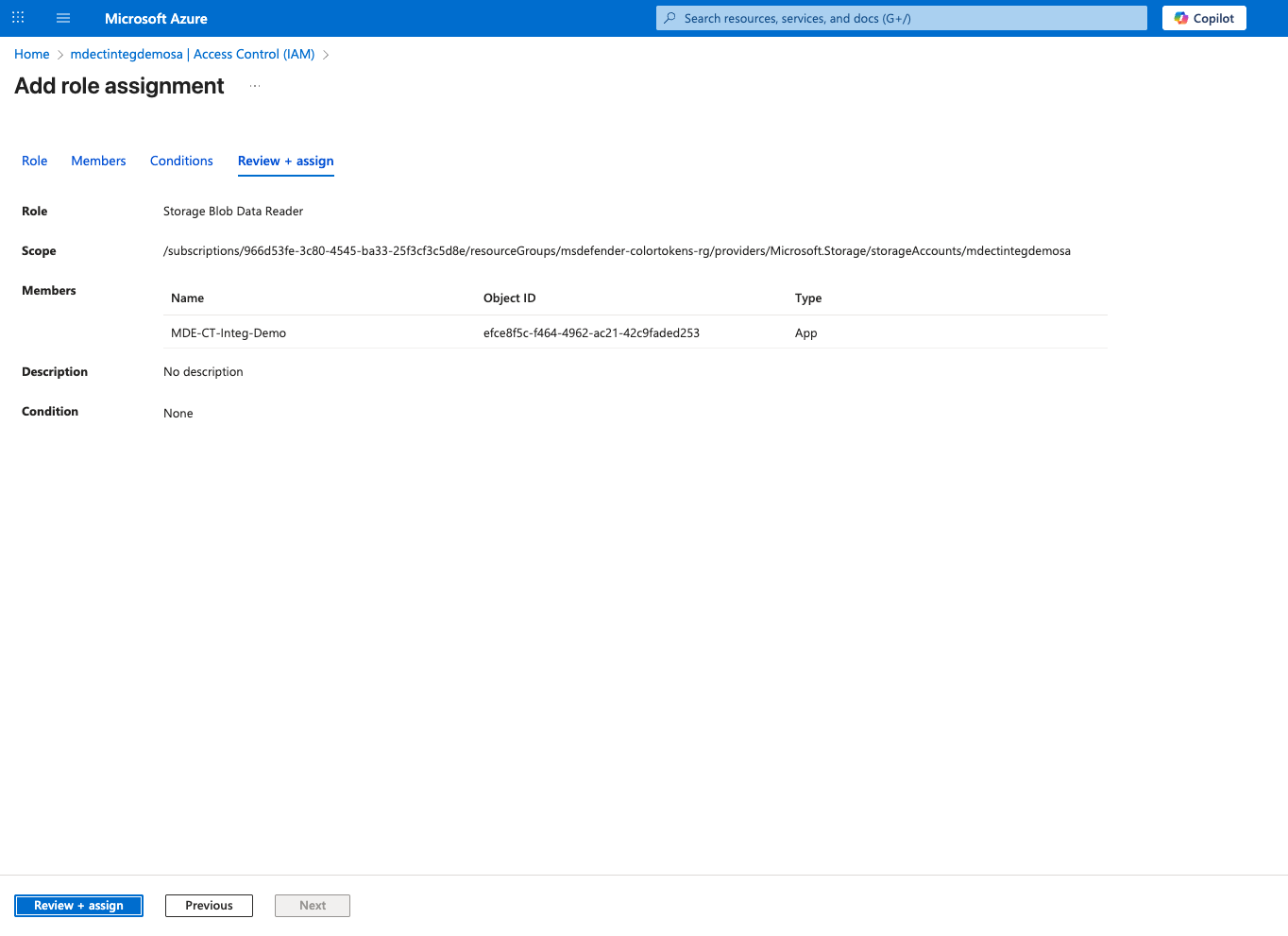
Click on Review + assign to save the changes
2.2 Storage Queue Access
-
Go to Storage Account > Data Storage > Queues > Click on the Storage Queue

-
Click on Access Control (IAM) > +Add > Add role assignment
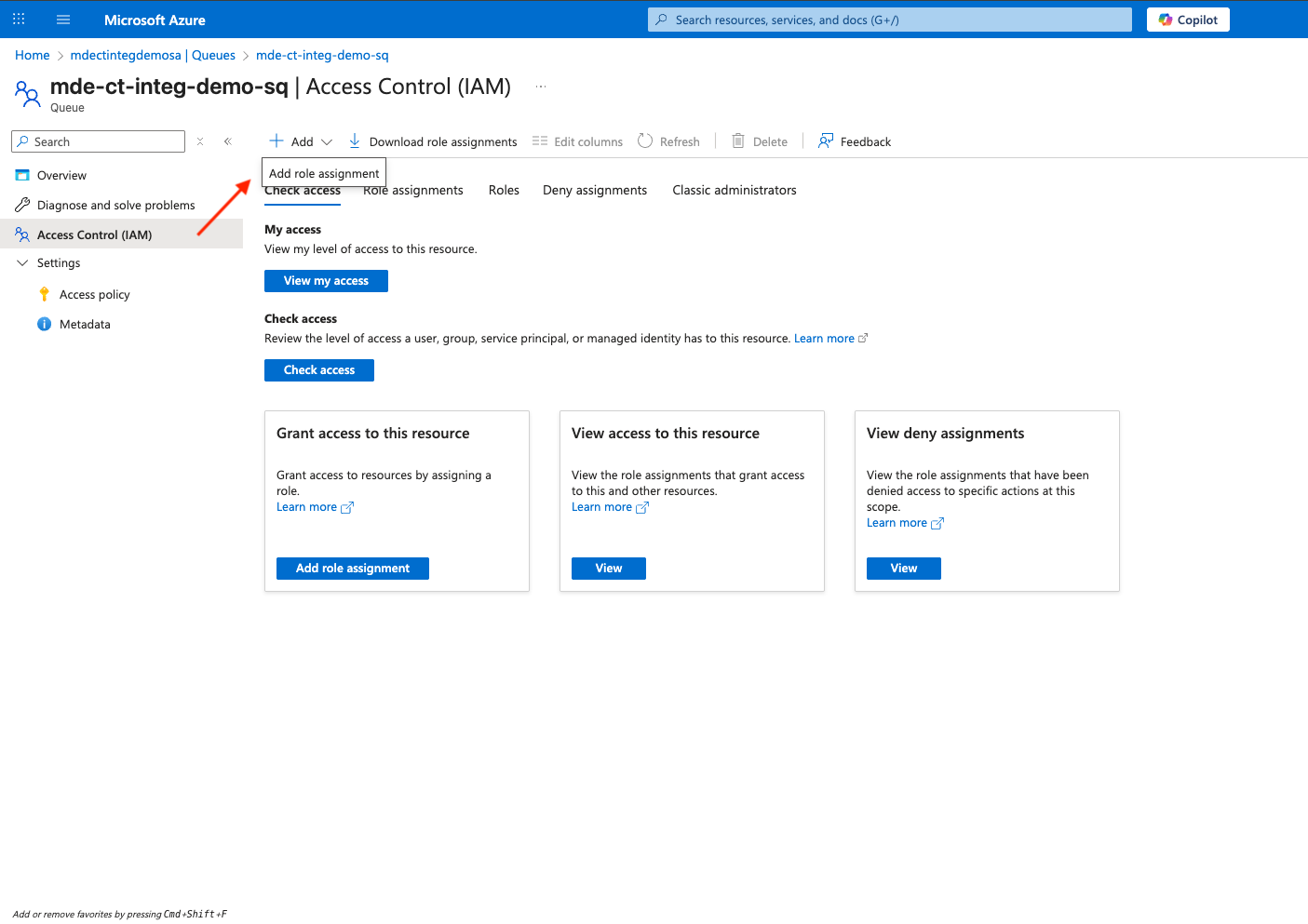
-
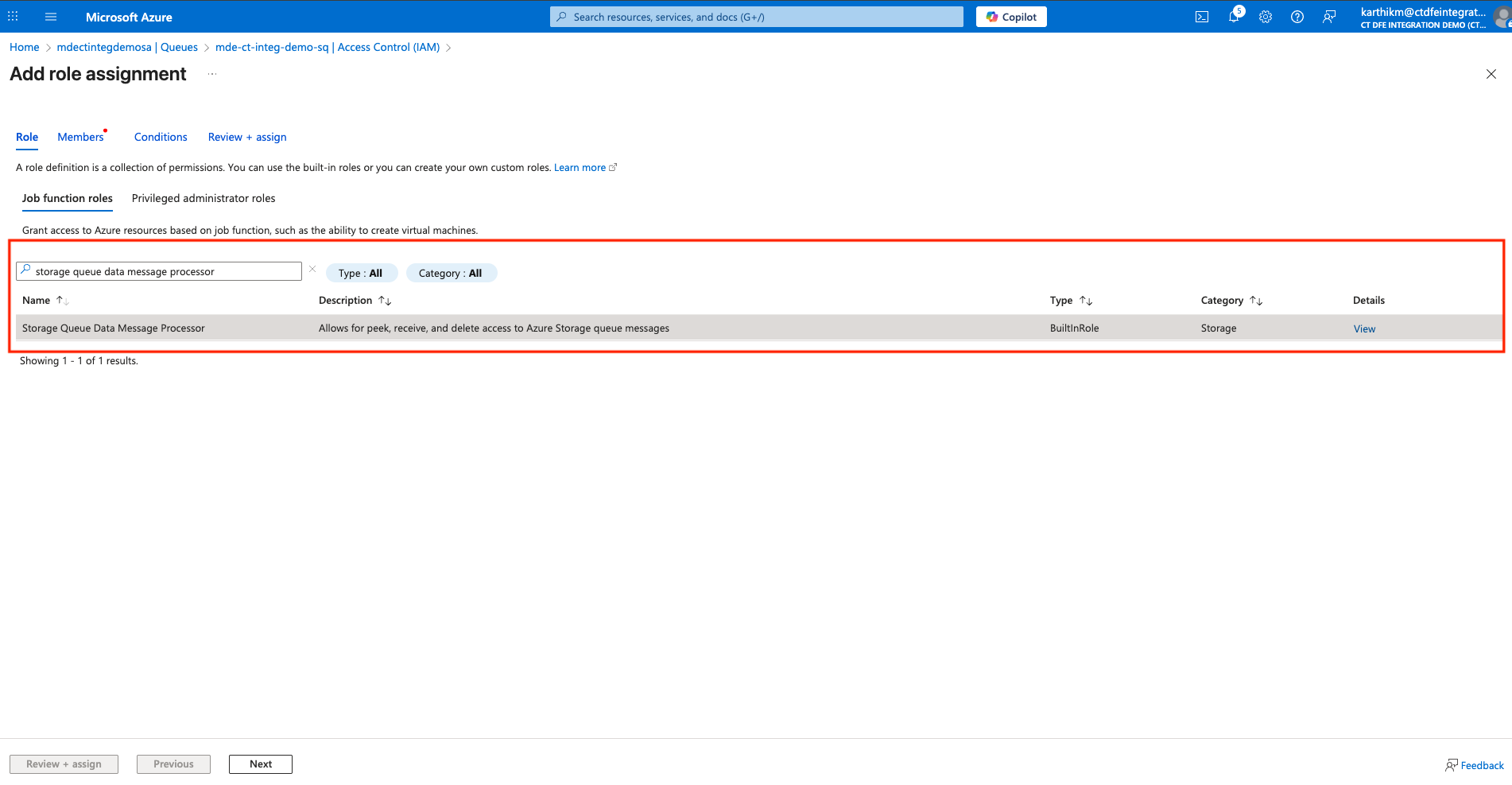
Under Role > Job function roles, select Storage Queue Data Message Processor
We need to provide the Application API credentials with Storage Queue Data Message Processor access to the storage queue. With this access, the Xshield platform can monitor this storage queue for new blob creation events.
-
Under Members tab, select on +Select members, and type your Entra ID application name under Select members and click Select
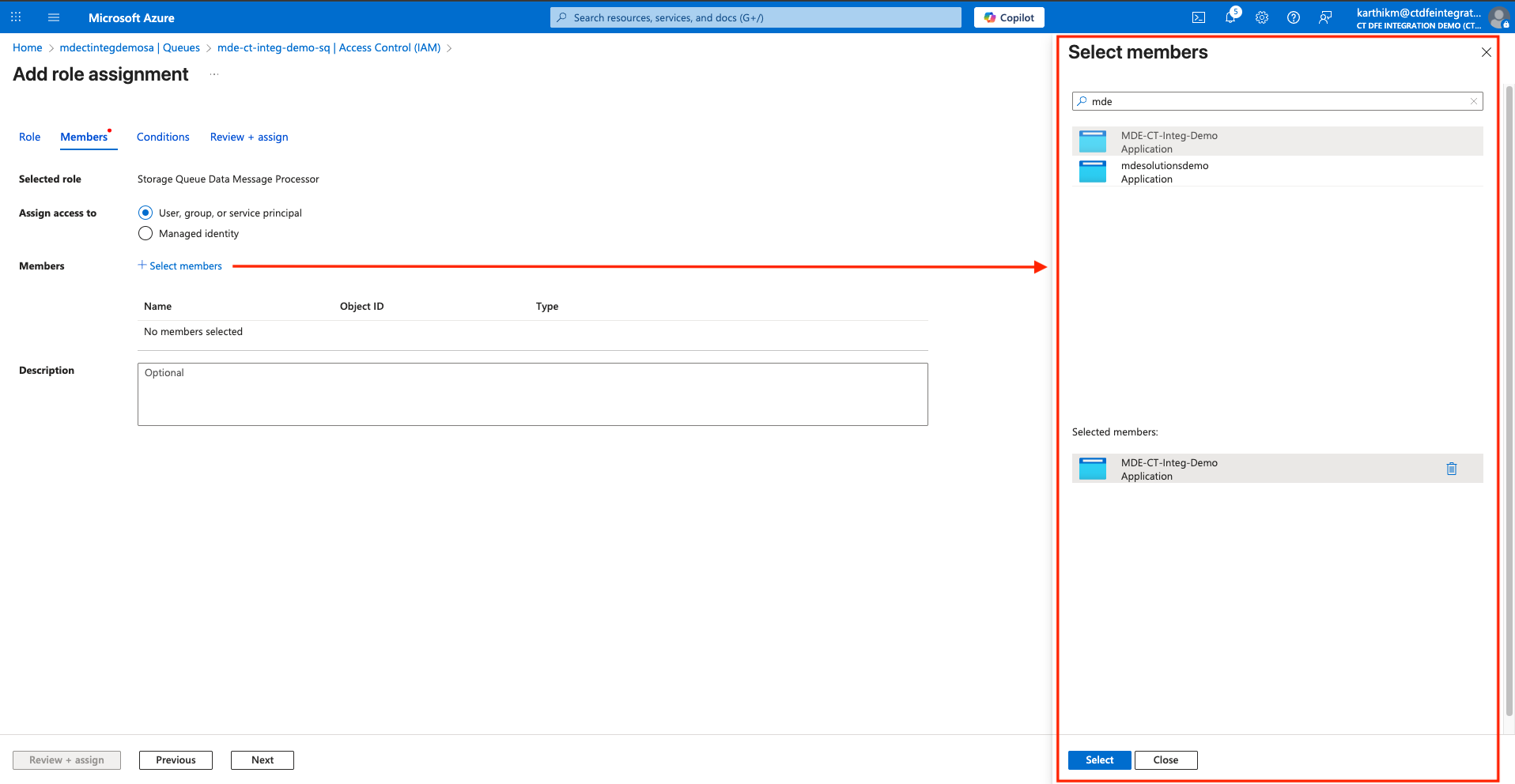
-
Click on Review + assign to save the changes
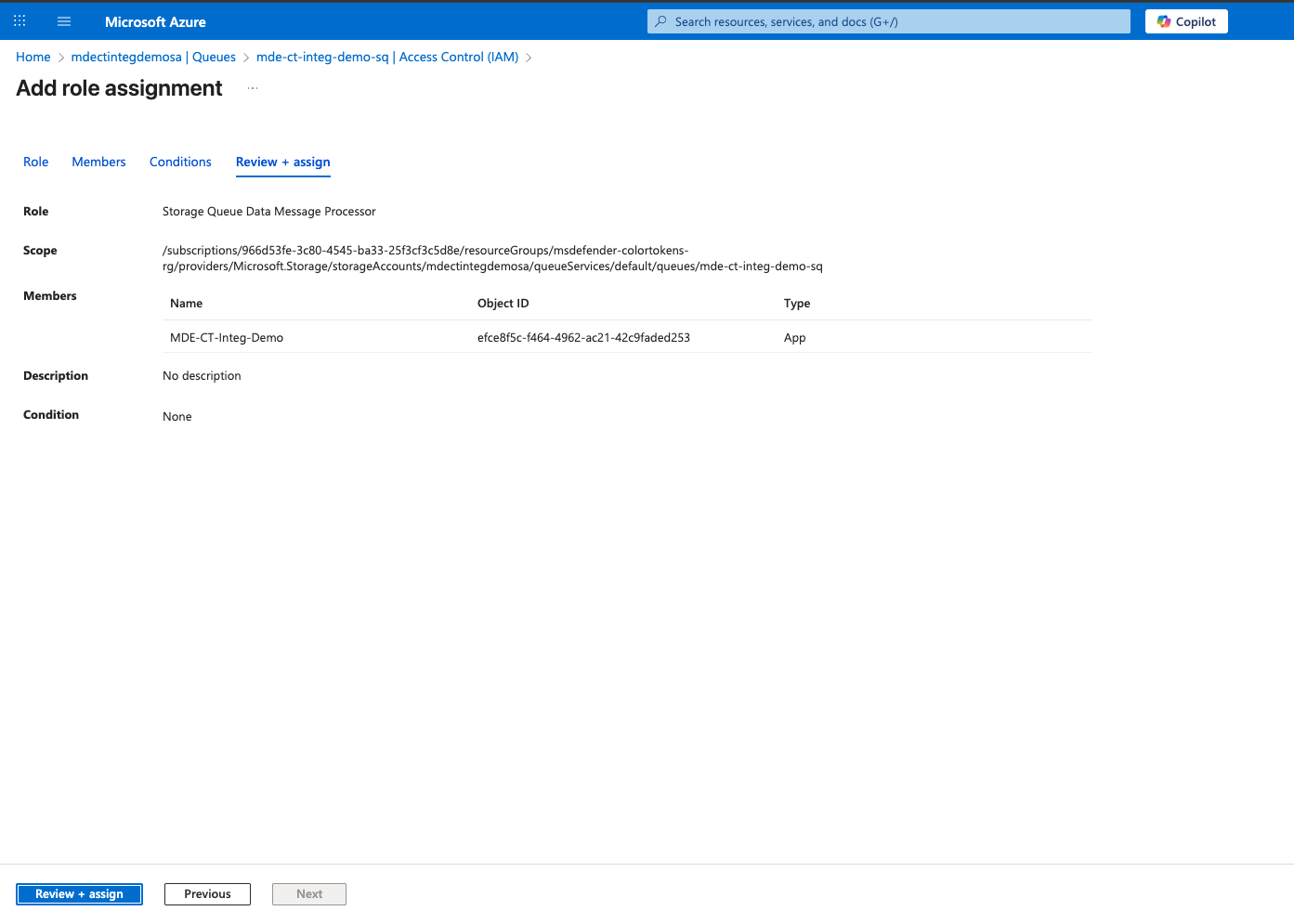
3. Retrieve the Resource ID of the Storage Account
-
Go to Storage Account > Overview > JSON View
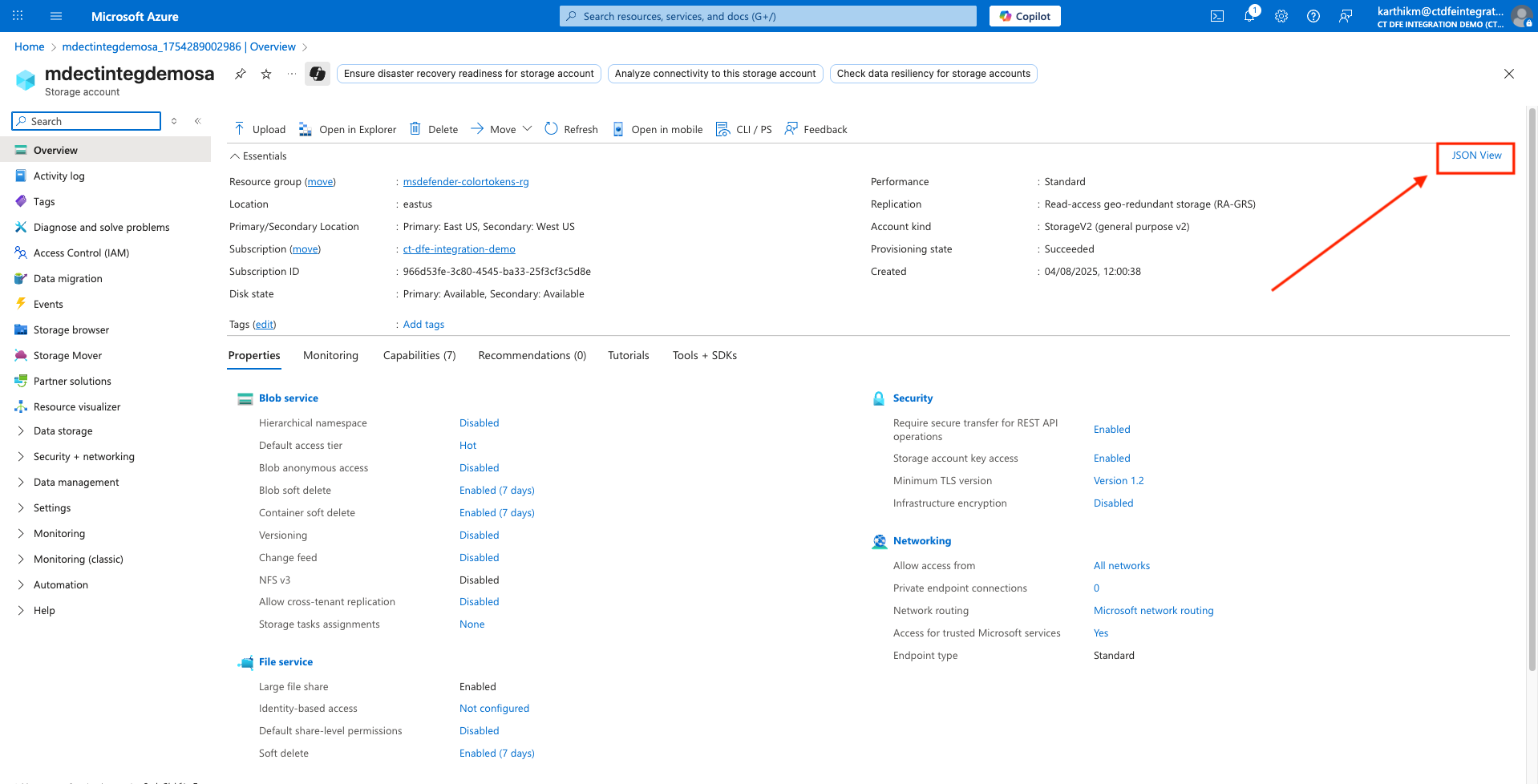
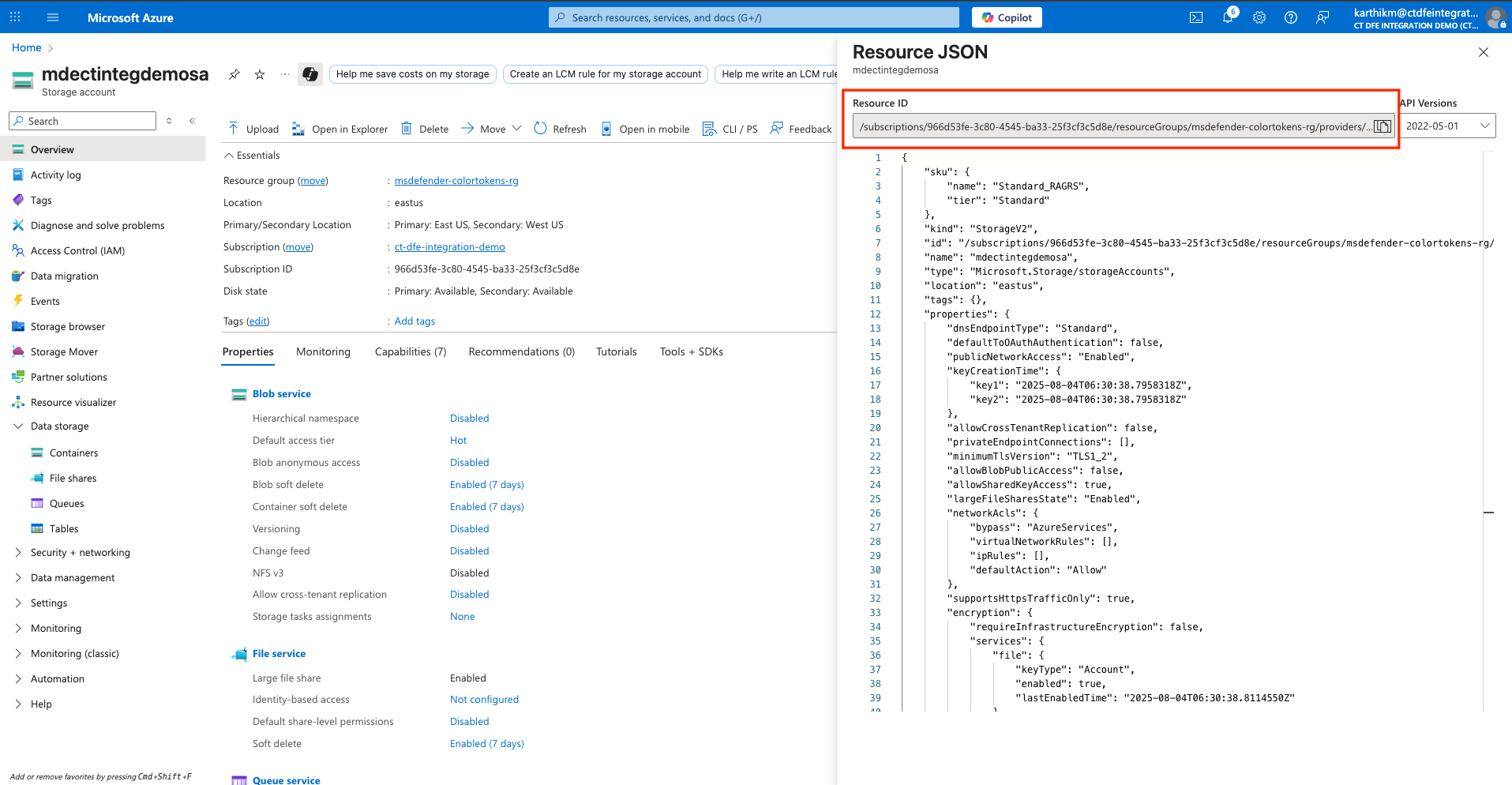
-
Copy the Resource ID from the JSON view. We will need this resource ID to export telemetry data to the storage account from Defender.
4. Configure Defender Telemetry Export via Streaming API
Microsoft Defender for XDR collects various telemetry events from machines onboarded to Defender for Endpoint. The Xshield platform requires access only to events in the DeviceNetworkEvents table to provide network visibility.
⚠️ IMPORTANT NOTE: Xshield only requires
DeviceNetworkEvents. While configuring the Streaming API to export data to Blob Storage, make sure to select only DeviceNetworkEvents under the Devices section of Event Types.
-
Go to Defender for Endpoint > Settings
-
Select Microsoft Defender XDR
-
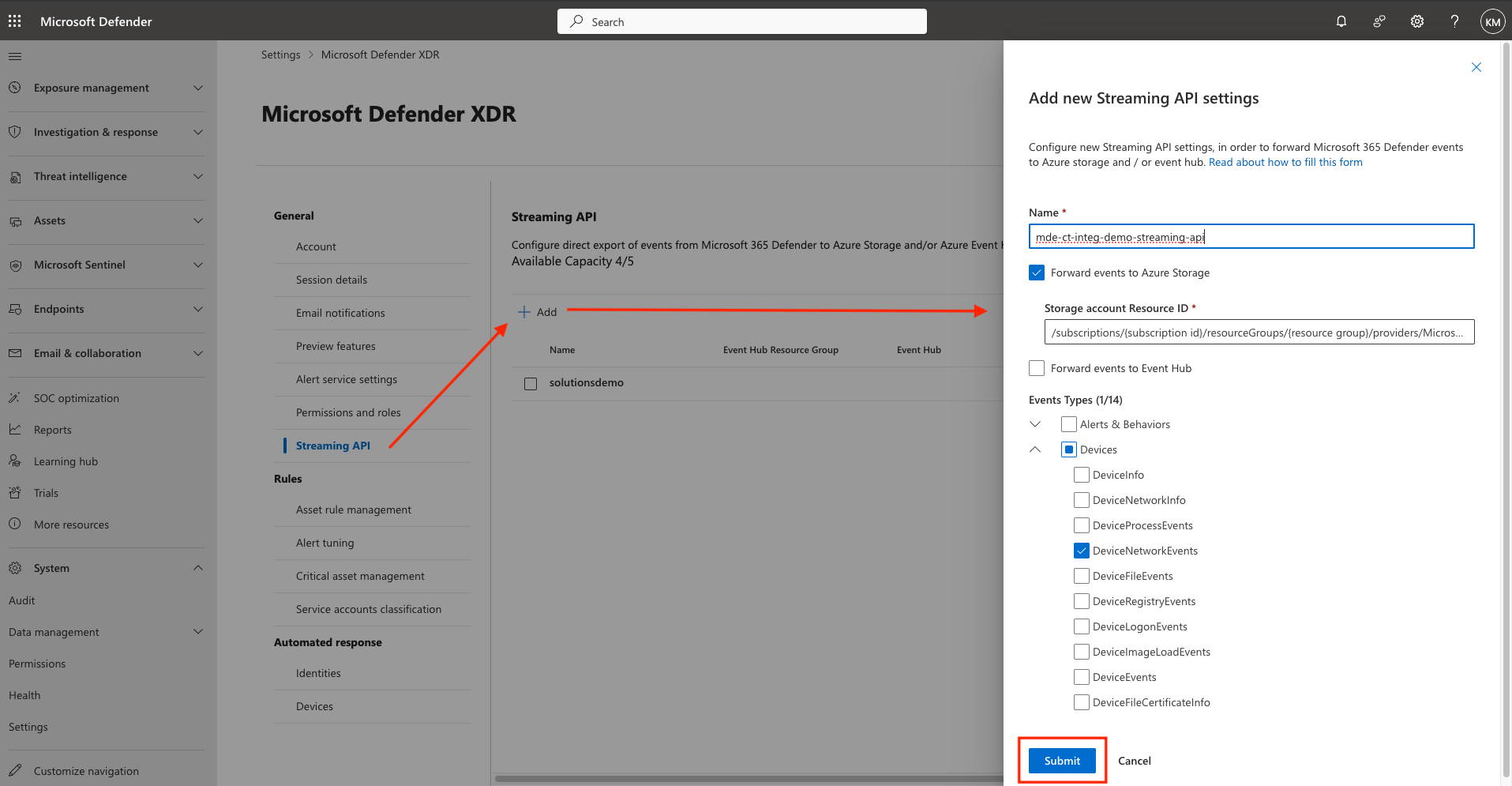
Select Streaming API > +Add. Provide:
- A value for name
- Select Forward events to Azure Storage
- Under Storage account Resource ID, enter the Resource ID of the Storage Account copied in the previous step (JSON View)
- Under Event Types, select Devices > DeviceNetworkEvents
- Click Submit
-
The Streaming API is now Setup successfully.
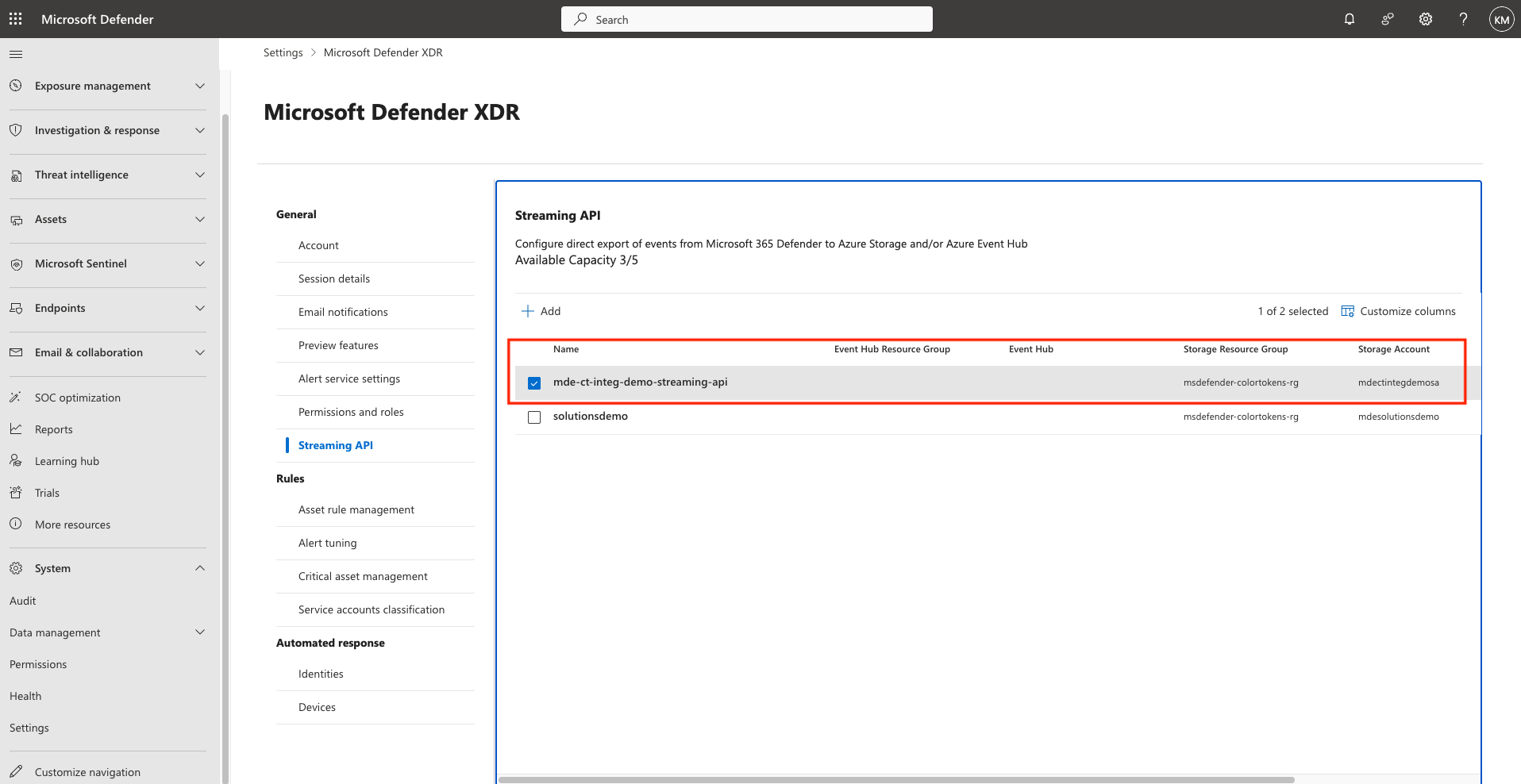
⚠️ Note: This configuration will:
- Export only:
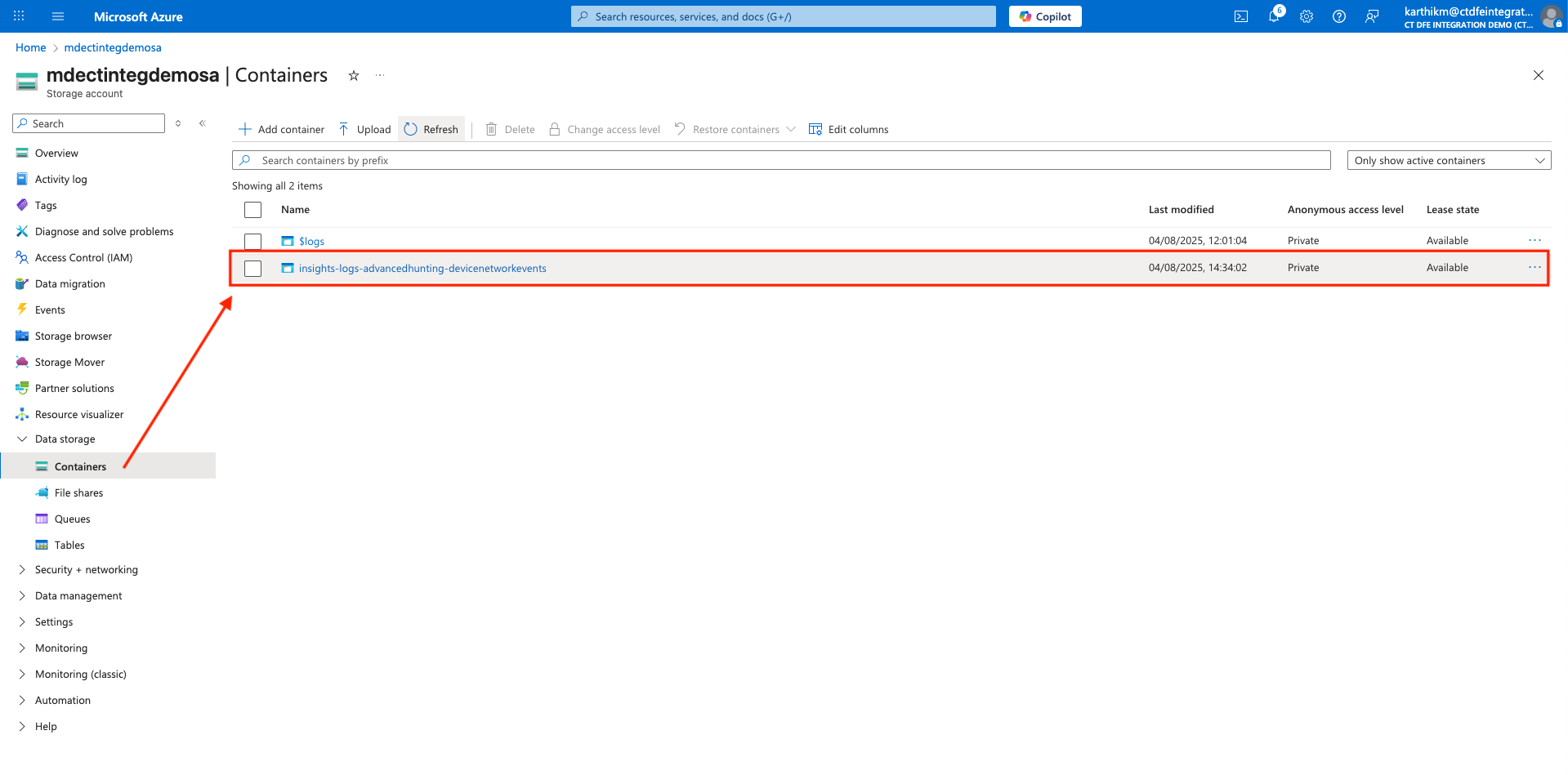
DeviceNetworkEvents- A container named
insights-logs-advancedhunting-devicenetworkeventswill be created automatically in the storage account.- Blobs will be stored in this container. ✅ Verify that blobs are being generated in the container before proceeding to the next steps. It can take up to 30 minutes for the first blob to appear in the storage container.
After completing these pre-requisites, please proceed to Activate Integration on Xshield section.
References and Support
- Register Entra Application Register Entra Application
- Create Client Secrets Create Client Secrets
- Streaming API Setup Streaming API Setup
- Event Subscription for Blob Notifications Event Subscription for Blob Notifications
For assistance, please contact ColorTokens Support.